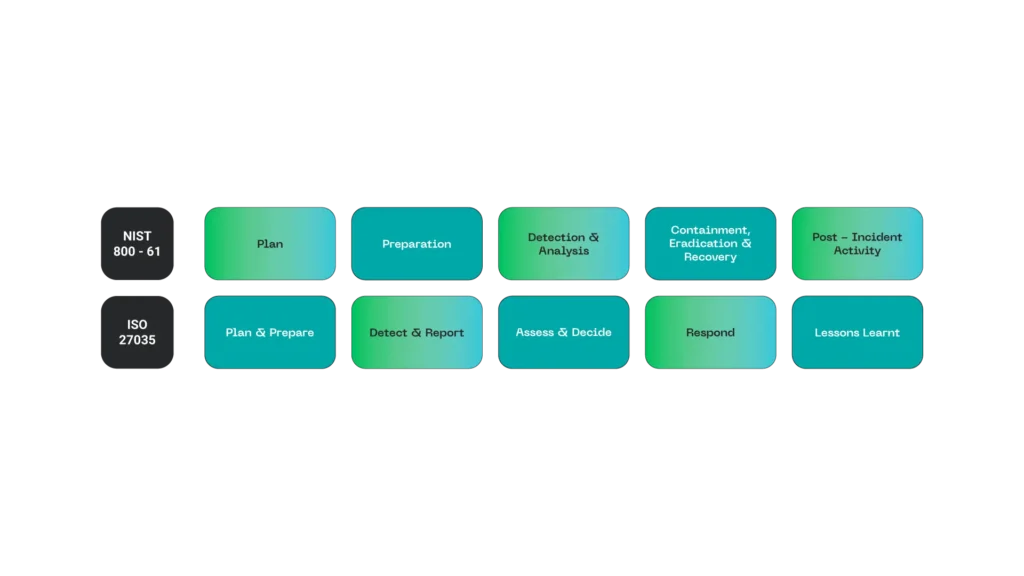
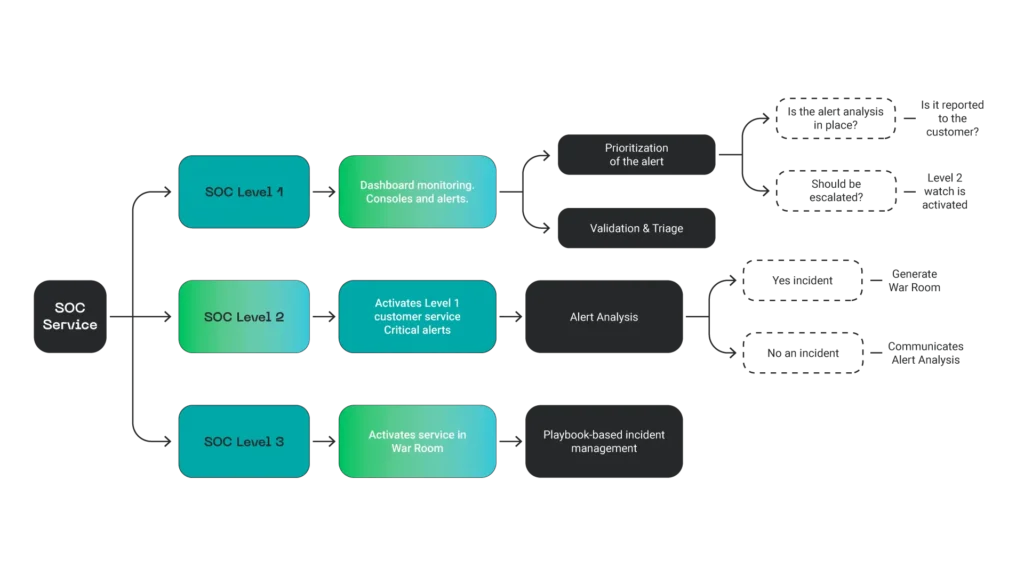
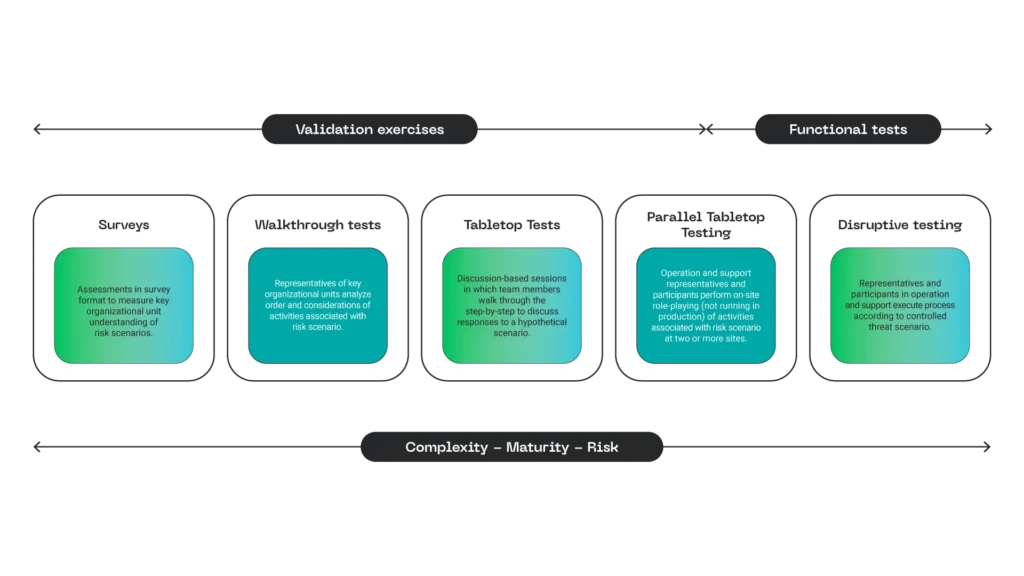
Attacks on critical infrastructures, such as electrical grids, generation plants, drinking water systems, or telecommunications, not only disrupt essential services for the population. They also have a domino effect that can interrupt entire supply chains at national and international levels.
Why are Critical Infrastructures Strategic Targets?
The damage and impact that an attack on critical infrastructures can cause are extraordinarily high, both in terms of their scope and the difficulty of subsequent recovery. To better understand why these infrastructures are strategic targets, it is important to detail some key factors.
Firstly, there is a high dependency on these infrastructures: fundamental sectors such as industry, transportation, hospitals, and financial services rely completely on electricity supply and telecommunications to operate. A disruption in these services immediately affects the functioning of multiple essential economic and social activities.
Moreover, the impact of an attack is not limited to the initial target; it has a multiplicative effect. For example, the paralysis of the electrical system can halt factories, block operations at ports, impact air and land traffic, and even interrupt banking payment systems and transactions. The damage rapidly spreads throughout a country’s entire value chain.
Finally, the difficulty of recovery must be considered. Unlike other sectors, critical infrastructures require complex and delicate restoration protocols. It is not enough to simply “turn on” an electrical system or a telecommunications network again; the recovery must be gradual and controlled to avoid greater damage, meaning that the effects of an attack can extend for hours or even days.
How Does This Impact the Supply Chain?
The impact on critical infrastructures has direct and severe consequences on the supply chain, compromising its continuity and efficiency on multiple levels.
One of the first consequences is the interruption in production. Manufacturing and logistics companies depend on electricity and communication systems to maintain their production lines, inventory control systems, and distribution processes. Without these basic elements functioning, industrial and commercial activity comes near to a standstill.
Additionally, transportation issues arise. The lack of electricity affects traffic lights, railway systems, loading centers, and land, maritime, and air distribution networks, causing the movement of goods and merchandise to stop or be severely restricted. The flow of products between suppliers, distribution centers, and retail points becomes chaotic or nonexistent.
Another critical effect is the depletion of stocks. Supermarkets, pharmaceutical companies, and distribution centers rely on electronic systems to manage inventories and coordinate orders. A prolonged failure of these systems can make it impossible to log or replenish goods, quickly leading to shortages of essential products.
Finally, financial disruptions further exacerbate the situation. If banking networks and electronic payment systems are impacted, wholesale and retail payments slow down or are interrupted, halting commercial operations and severely impacting both businesses and consumers.
What Recent Attacks Have Taught Us?
Recently, several attacks have demonstrated how a single incident targeting critical infrastructures can have devastating effects on the supply chain and the daily lives of millions of people.
One of the most significant examples occurred in Ukraine in 2015 and 2016, where coordinated cyberattacks against electric companies caused massive blackouts. In 2015, the Ivano-Frankivsk region experienced power outages that affected tens of thousands of people for hours, and a year later, a more sophisticated attack caused a blackout in Kyiv. These attacks were attributed to groups linked to Russian military intelligence, such as Sandworm, demonstrating that cyberspace can be used as a strategic weapon to destabilize a country.
Another notable case was the Colonial Pipeline incident in the United States in 2021. A ransomware attack forced the temporary shutdown of the largest pipeline network on the East Coast, severely impacting fuel supply and creating shortages in multiple states, impacting both consumers and industries dependent on the transportation of goods.
In Japan, in 2023, the Port of Nagoya, one of the main export ports for cars and electronics, was paralyzed by a ransomware attack. This incident severely altered the logistics chain and delayed key exports for the Japanese economy.
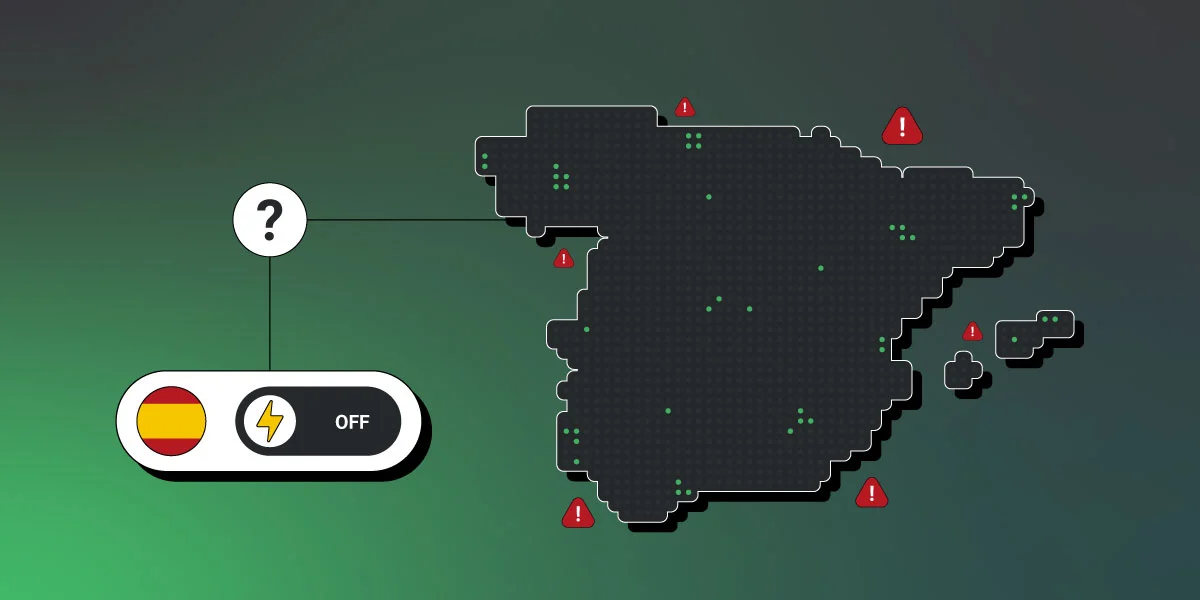
The recent power outage affecting Spain, Portugal, and some areas of southern France also recalls other events where, although cyberattacks were initially suspected (such as the blackout in Argentina and Uruguay in 2019), the causes were later attributed to technical failures or problems in energy network management. Nevertheless, experts agree that the risk of cyberattacks on critical infrastructures is real and growing, as evidenced by more recent incidents in countries like Denmark in 2023, where the energy sector suffered cyberattacks, though without actual supply outages.
In all these cases, an attack or failure at a critical point triggered cascading consequences, affecting industrial, financial, logistical, and basic service sectors, clearly demonstrating that critical infrastructures are a central link in the security of the global supply chain.
Effective cybersecurity management in critical infrastructures is essential to mitigate the risks associated with cyberattacks. Through platforms like Batuta, oversight and control of endpoints are facilitated. Its comprehensive approach allows organizations to achieve total visibility over their IT infrastructure, identifying vulnerabilities.