
Apple AirTags, Unwanted tracking capabilities
April, 19, 2023
16 minutes read
Salvador Mendoza – Research and Development Director, Metabase Q
// Research Summary
Have you heard of AirTag by Apple?
It is a tracking device developed by Apple and designed to help people find misplaced objects. However, even when Apple states that AirTag technology is solely used for tracking objects, a growing number of malicious individuals are taking the advantage of how easy it is to install and set it up to track unaware targets, in other words, people.
It is possible to detect those unwelcome tracking AirTag gadgets with a special third device. By analyzing the AirTag advertising data, a targeted user can scan and identify special characteristics that make AirTags unique. Nevertheless, some attackers disable the AirTags when they figure out the target’s desired location to avoid any future detection. Disabling the gadget will prevent iPhone or Android users from detecting the hidden AirTag with the applied Apple methodologies. This issue with limited tools and deficient mechanisms is leading the community in the direction of a new privacy issue that is laborious and difficult to confront, which is what this paper will cover.
// Introduction
Tracking technology is not new. It has been around for centuries and, like any other type of technology it continues to evolve. It is mainly been used to create navigational tools and track objects; one of the oldest forms of tracking technology were the compasses. From there, the Global Positioning System (GPS) appeared, which works through satellite signals and is used in devices like cars, airplanes, and cellphones. Bluetooth tracking was introduced later. Different from GPS technology, Bluetooth tracking technology works through signals and communications between two devices. Tracking technology can make things easier. However, like any type of technology, it is vulnerable to cyberattacks. The case of AirTags, by Apple, is no exception.
Last year, Apple developed a tracking device called AirTag to help people track important objects that are easily misplaced, such as keys and wallets. In other words, AirTags are Apple-developed tracking devices designed to easily locate any object with the help of an iPhone and the FindMy application. The only thing needed for its operation is to link it to an Apple account through an iPhone and then place it on the object that needs to be tracked. The AirTag device has slightly larger dimensions than a coin (31.9mm in diameter and 0.8mm thick).
Unlike most of its competitors, the Apple AirTag IoT device does not use in-device Global Positioning System (GPS) tools to locate lost items. Instead, it uses Bluetooth Low Energy (BLE) technology to connect to any Apple device nearby to get its exact position from there (even if that device does not belong to the owner of the AirTag). The data transmitted from the AirTag to other devices is encrypted to ensure the users’ privacy. Moreover, the iPhone devices are never notified when they had been used as an antenna relay to transmit those locations. This strategy allows the device to operate simply with the use of a CR2032 battery, which provides almost a year of constant operation.

Figure 1: AirTag dimensions
Apple makes three different methods available to find the AirTag, two of these methods only work if the device is close enough to the tracker (approximately 10 meters seems to be the ideal distance).
- In the first method, the user can activate a speaker that’s integrated into the AirTag, which will then beep for a short period. This process can be repeated as many times as necessary until the source of the sound is found. The sound is not very loud due to the size of the speaker, so this method is useful only if the user is close enough to hear it.
- The second method takes advantage of the integrated Ultra-wideband (UWB) function from the Apple U1 chip in the AirTag. Since the iPhone device has the same technology, the FindMy application can create a compass that points to the exact direction where the AirTag is located, as well as add an approximation of the distance between the iPhone and AirTag. This option is only available at close range.
- In the third method, if the AirTag is away from the linked device, the owner can request a GPS location from the application. This last function allows the creation of a route to reach the device using FindMy application. This method allows for the AirTag to be registered as lost; if found, and if it has an NFC sensor, it can be read it using an iPhone or even an Android device to obtain the contact information and be able to return it to the current owner. It should be noted that, because AirTag works depending on whether there are iPhones in its vicinity, the location it provides is not in real-time; it
only provides the last position it registere
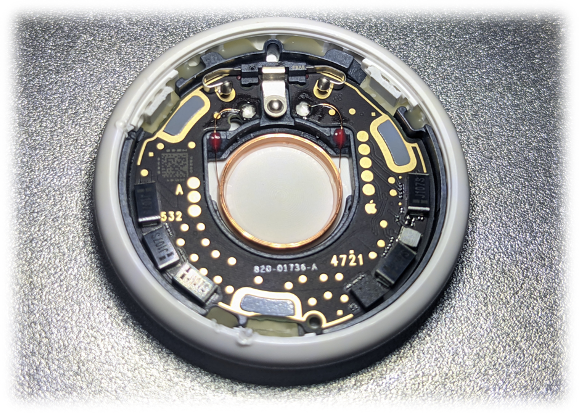
Figure 2: AirTag inside components
The AirTags costs USD 29 when purchased individually, or USD 100 for four devices. This classifies the AirTags as an accessible, and, in some cases, a disposable geolocation device. This technology has been available since April 30, 2020. From the day of its launch, Apple made it clear that this device is for tracking objects, not people. Apple continues strongly emphasizing that tracking people without their consent is illegal and that the company will take all measures in its power to prevent and punish this behavior. However, that has not been enough to deter this behavior and stop users from utilizing this device to track vehicles and individuals.
For instance, in some cities, such as Los Angeles or Atlanta, hidden AirTags were discovered in cars. The notification system from an iPhone made this detection possible (none of the cases mentioned that the devices had been found because of the beeping)[1]. Surprisingly, there are some states where it is not illegal to put a tracker device outside of a vehicle under specific circumstances. “In Georgia, individuals can legally place trackers on others’ vehicles, as long as the device isn’t used to stalk or harass them”.[2] As if that was not enough, some websites already sell AirTags that have the speaker disabled, and there are videos on YouTube showing how easy it is to install the trackers on your own.
To prevent misuse of this technology, Apple uses a couple of techniques to warn its users if anomalous AirTag behavior is detected.
- With the first method, if the AirTag has been out of the owner’s range for a long time, it will start to emit repetitive sounds a couple of times and at intervals of time. This is the only passive detection measure out there for non-iPhone users, which is not very encouraging given the low power of the speaker and how easy it is to disable it.
- In the second method of defense, if an iPhone detects that it has spent a lot of time near an AirTag that has been apart from its owner, then it will send a notification indicating its presence. From there, the speaker can be activated to try to find the device, or simply disable it. This notification can arrive at a random time between 8 and 24 hours after the anomalous behavior is detected. However, many users have reported this system as inconsistent and unreliable, since in some cases, the notification has taken days to be displayed. This type of warning is not available for Android users; the only option is to download Apple’s tracker application to actively search (does not run in the background) for AirTag devices.
Apple is aware of this malicious use of its product, so it is constantly updating its security measures from the applications. In addition, it has a 24/7 support service that can be called if suspicious activity is detected with the use of AirTags. Apple encourages its users to call the local authorities to collaborate and protect their safety. However, in some cases, the police have been overwhelmed by the technological advance that these devices represent, leaving them without instructions on how to proceed because an automatic notification cannot be considered as a case of harassment or violation of privacy.
// Privacy problems
Given the delay warning notifications might take to be received, an attacker could wait for their victim to show up in a public place, like a supermarket, or a parking lot, plant the device in their vehicle, and simply wait for them to arrive home. Within the first 8 hours (the minimum time it takes for the application to notify its misplacement) the attacker would have enough time to obtain all the information necessary to act. So, if the attack is carried out within this timeframe, the victim may never know they were tracked at all. Technically, once the attacker obtains the address, they could periodically approach a range of 10 meters from the device and restart the notification time indefinitely to make it even more difficult for the device to be detected and, thus, be able to acquire more valuable information, such as the victim’s daily routine. The attack’s effectiveness increases if the victim does not have an Apple device.
Knowing that My Find Network only needs an Apple device to be nearby and connected to the Internet, this type of attack can happen practically anywhere in the world. The only limited function that exists is the Ultra-wideband functionality since in some countries[3] they do not have that support, and this functionality is not required to commit the attack.
Although no one is safe from these attacks, women represent a more frequent target in the reported cases, since harassment is still one of the main forms of gender-based violence takes place, as proved by the devices found in jackets and cars. These attacks can also be alarming for civil servants such as politicians, famous personalities, or reporters who might be criminals’ targets. However, it should be clarified that, to the best of our knowledge, no case has yet been recorded where a politician has been the victim of an attack against his integrity with the help of any of these devices, but, without a doubt, it is a latent risk that is crucial to consider.
Some users argue that making the presence of an AirTag more obvious could backfire. If a tracked item is stolen, the thief could quickly realize they are being tracked and remove the device, eliminating any chance of recovering the stolen item[4]. However, Apple states that AirTags are designed to recover lost items, not stolen ones. So, making the AirTag’s presence more obvious serves mostly the former purpose.
// AirTag Bluetooth BLE technology
Bluetooth BLE technology has been implemented in many different IoT devices around the world. From simplistic communication projects to high-tech industrial devices. The simple way to start the pairing process between two Bluetooth BLE capable devices is by implementing a scan from the central or master device and the advertising process from the peripheral or slave device (Steps 1 and 2 in Figure 3).
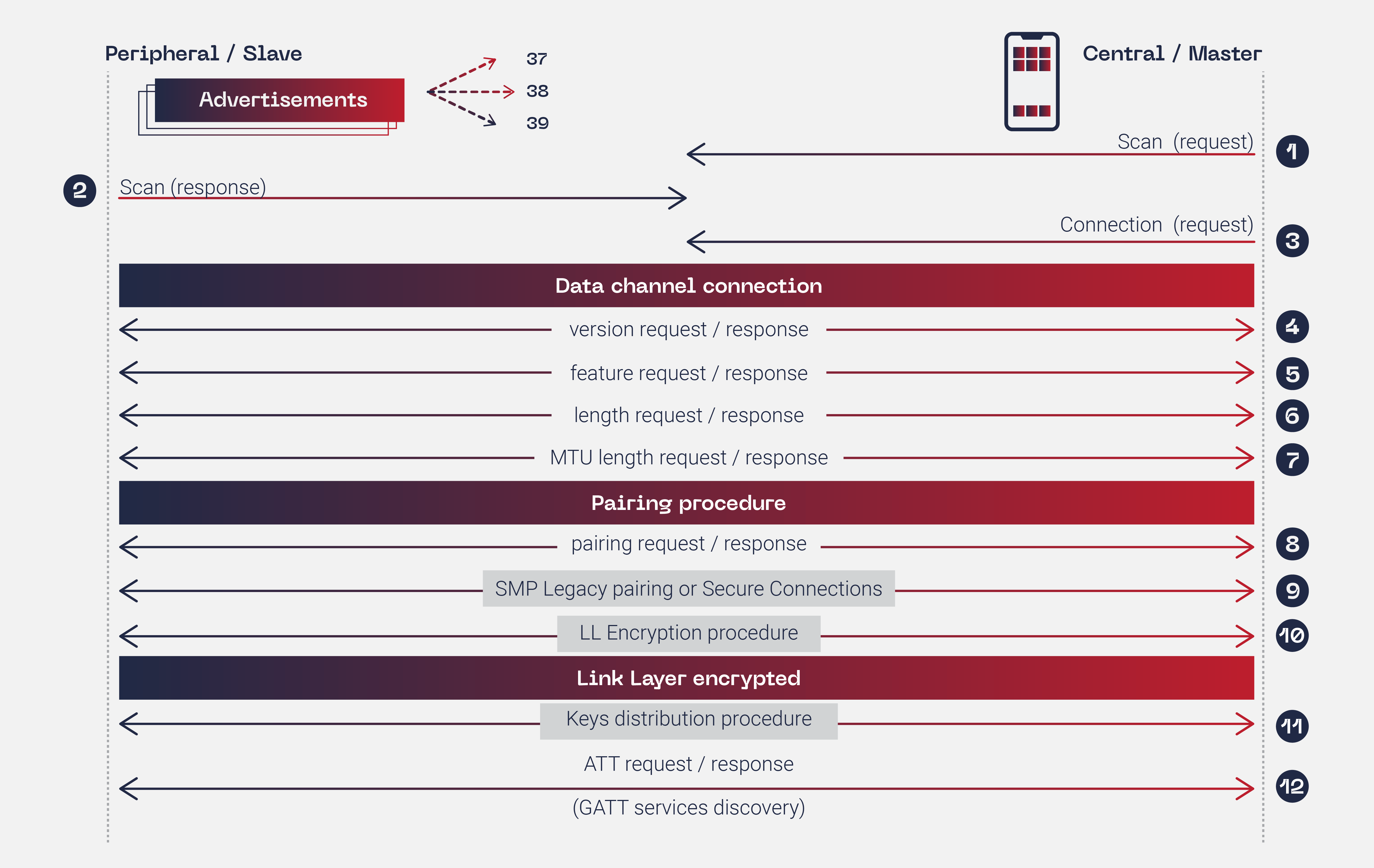
Figure 3: Bluetooth BLE connection process
These first simple steps are where the IoT AirTags develop their tracking potential. Any iPhone device that is close enough to read the advertising Bluetooth BLE signal, will be capable to update the AirTag location. Meaning that it will not require establishing a Bluetooth BLE connection because the needed data to identify the AirTag is in the advertising packet.
The BLE implements 40 radio frequency channels. Each of them is separated by 2 MHz. The AirTag device only implements the advertising channels: 37, 38, and 39.
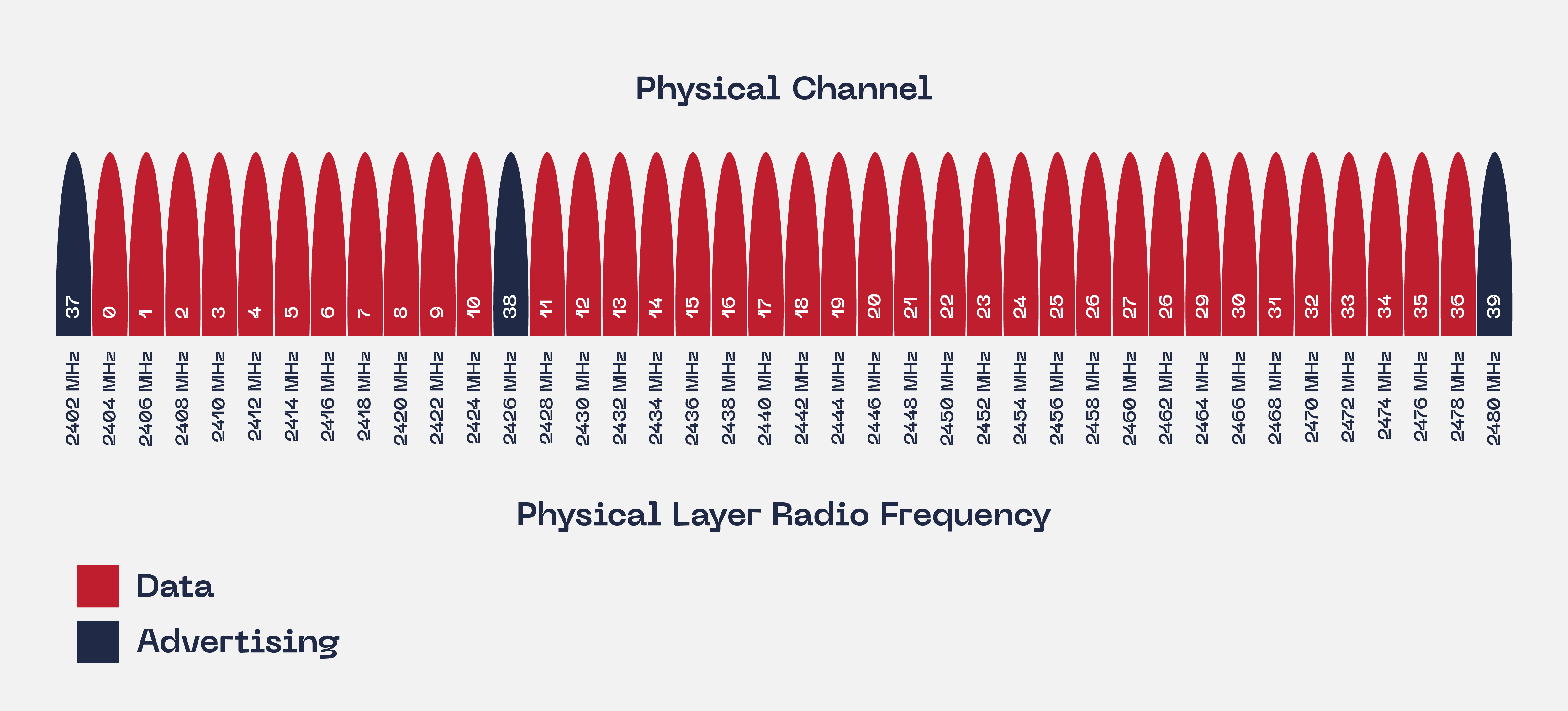
Figure 4: Bluetooth BLE advertising channels
When an AirTag is not in the range of the owner device, the AirTag will advertise a constant Bluetooth BLE signal with some variable information. Part of that advertising information is its cryptographic public key. If any other iPhone device detects this signal, it will update the AirTag path location. Apple AirTags also work with Ultra-Wideband technology or UWB to establish critical communication that could take place indoors.
Analyzing the advertising data from an Apple IoT AirTag:
1E FF 4C 00 12 19 10 66 77 88 99 00 1F 2E DA BA F6 35 7E 2F 7E 66 77 88 99 00 38 AF 0A 02 37
| 1E | Packet length |
| FF | AD Type |
| 4C 00 | Apple ID device |
| 12 | Special byte for Apple service |
| 19 | Payload length |
| 10 | Special identifier byte |
| 66 77 88 99 00 1F 2E DA BA F6 35 7E 2F 7E 66 77 88 99 00 38 AF 0A 02 37 | EC P-224 public key |
One of the most important aspects of AirTag’s advertising packets is their constant length (0x1E). Also, the Apple ID device plays an important role to detect the AirTag advertising signal easily.
// AirTags Bluetooth BLE services and characteristics
The AirTag device implements 6 different services. Those services are implemented to communicate commands or information in the communication process between the master or central device and the AirTag:
- 1800: Generic Access Service
- 1801: Generic Attribute service
- 7dfc8000-7d1c-4951-86aa-8d9728f8d66c: Unknown Service
- 7dfc7000-7d1c-4951-86aa-8d9728f8d66c: Unknown Service
- 7dfc6000-7d1c-4951-86aa-8d9728f8d66c: Unknown Service
- 7dfc9000-7d1c-4951-86aa-8d9728f8d66c: Find My network Service
The FindMy network service contains a special characteristic that will oversee writing a specific order to the AirTag. To make the AirTag play a sound, the normal Apple application must write one byte(0x01) in the characteristic 7dfc9001-7d1c-4951-86aa-8d9728f8d66c:
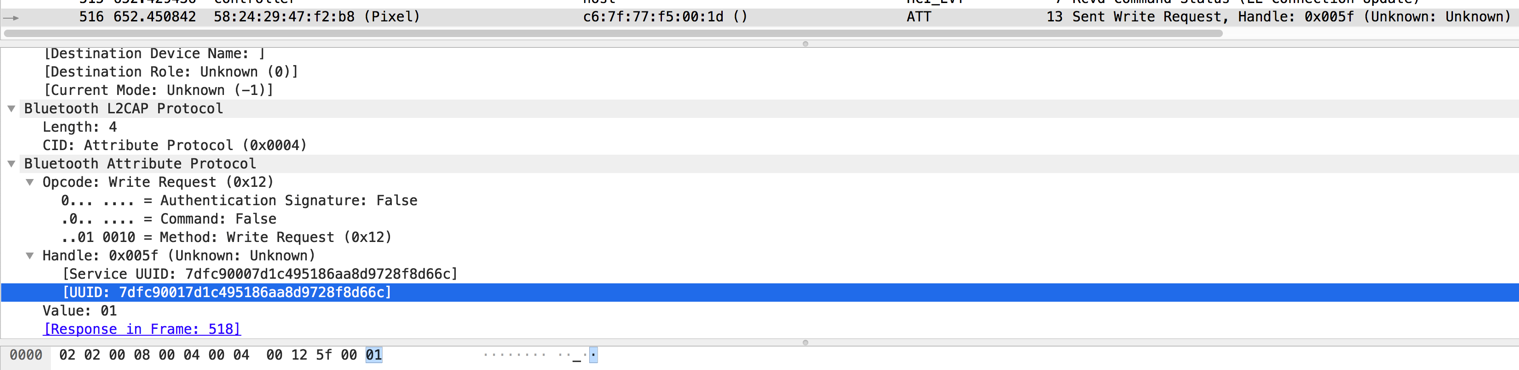
Figure 5: Bluetooth BLE sound command
Moreover, to force the AirTag to play a sound from a different Bluetooth registered device, some important steps must be satisfied first:
- The AirTag must not be connected to the registered Bluetooth owner device. Not even in range.
- The user must connect to the AirTag to register the Bluetooth address. It is not necessary to keep a constant connection to the AirTag.
- The AirTag has a timer that is used to keep track of how long it was detected by this new Bluetooth device.
- After ten minutes from the initial connection, the user should connect to the AirTag again and send the command to play a sound.
- During these ten minutes, the AirTag has to not be in contact with the registered owner device.
This approach will only work if the AirTag device was initialized and registered by an iPhone user.
// How to detect a disabled/unregistered AirTag device
It is possible to detect an AirTag even after a malicious user disabled it. The objective of disabling the AirTag is to avoid the alert detection system used by the Apple devices and Apple programs. The Apple alert mechanism is triggered when the AirTag is away from its registered owner for some hours, depending on different unknown variables. Also, the AirTag will stop making sounds after a few hours by itself.
If malicious actors disabled an AirTag after they figured out the desired target location, the targeted person should be able to find the disabled device by detecting the advertising signal. This could be achievable by implementing a BLE scanner to navigate through the signal source. To do this, the user must implement a capable device that can verify the RSSI from the AirTag BLE signal. If the device is close, the intensity will be high; and if the device is far, the signal intensity will be low. To play with these variables, the BLE device must be capable to calculate the RSSI in real-time and accurately detecting the disabled AirTag location.
The malicious user can disable the AirTag in two different ways: first, by enabling the lost feature which indicates that, if someone finds the AirTag, what would be the steps to return the device to its owner. The advertising data does not change with this mode:
Lost AirTag:
1E FF 4C 00 12 19 10 66 77 88 99 00 1F 2E DA BA F6 35 7E 2F 7E 66 77 88 99 00 38 AF 0A 02 37
When an individual removes the AirTag from the iPhone FindMy service, the device will change the advertising data. This new behavior will mimic a new AirTag device. With this approach, the AirTag device will not be detected by the iPhone detection mechanisms or by the Android Apple application, making it difficult for a targeted user to detect an AirTag after some else has disabled it:
Unregistered AirTag:
1E FF 4C 00 07 19 05 66 77 88 99 00 1F 2E DA BA F6 35 7E 2F 7E 66 77 88 99 00 38 AF 0A 02 37
The only way to stop the AirTag to advertise data is by removing the battery.
// Amini project
Amini is a specialized open-source project to scan, detect, spoof, and play a sound for AirTags devices. Amini was designed to be implemented with the Arduino environment, for easy purposes, and to be used in any Arduino-supported device with BLE capabilities.
It is possible to make a constant scan for AirTag devices. Amini can analyze specific parameters in the Advertising packets to identify specific information such as company name, advertising type, and the technology the device is implementing. The project can detect up to 10 AirTags simultaneously. This parameter is variable, and it could be adapted to the user’s needs:
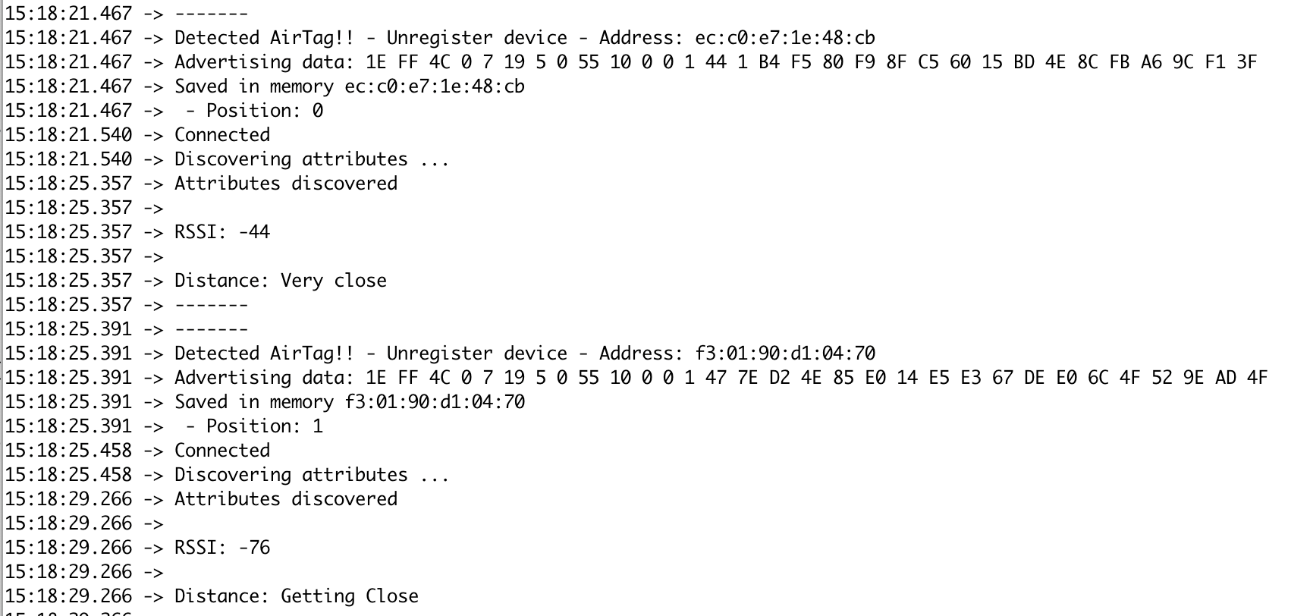
Figure 6: Discovering AirTags simultaneously
Adding on to the fact that the distance between the device that is running Amini and the AirTag can be detected, the project can also detect registered or unregistered tags automatically. This feature is useful to detect AirTags that have been disabled for the malicious individual’s practical conveniences. Amini is capable to keep track of each AirTag that it discovers. It has a timer counter for every AirTag which will help to continually analyze the environment and, if it detects the same AirTag, after 10 minutes, it is capable to play sound writing in a specific AirTag BLE characteristic for easy detection:
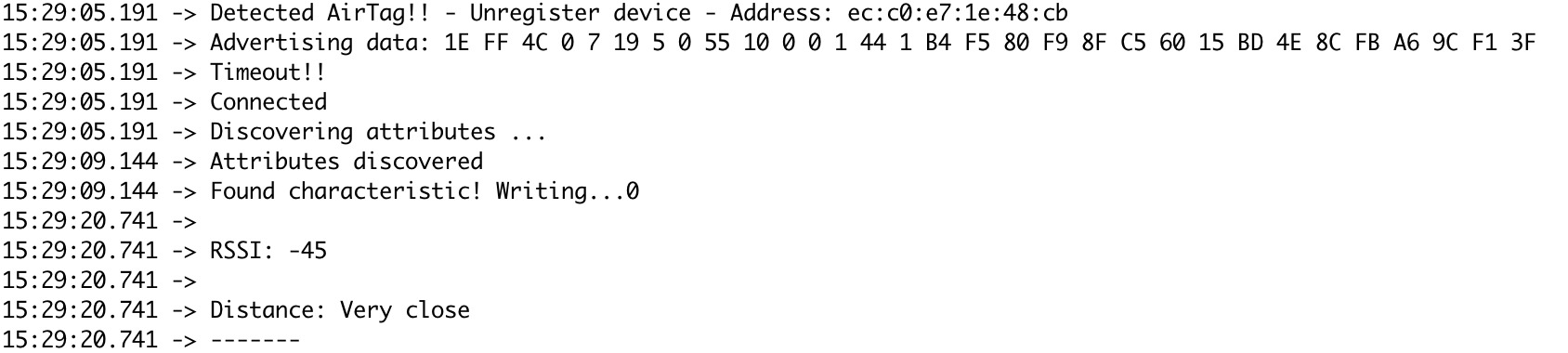
Figure 7: Writing AirTag characteristic to play a sound after the timeout
Also, Amini can spoof the advertising packets. Mimicking the AirTag behavior to simulate that specific device. This helps to deceive the malicious user about the current AirTag situation.
// Recommendations
Anyone is vulnerable to these kinds of attacks, therefore, it’s always better to take preventive measures and know what actions to take in case of becoming a victim,
- Users need to frequently run Bluetooth scans to detect undesired devices. Applications such as nRF connect suits perfectly to identify Apple devices nearby. One of the most important characteristics to detect the AirTags is the advertising package:
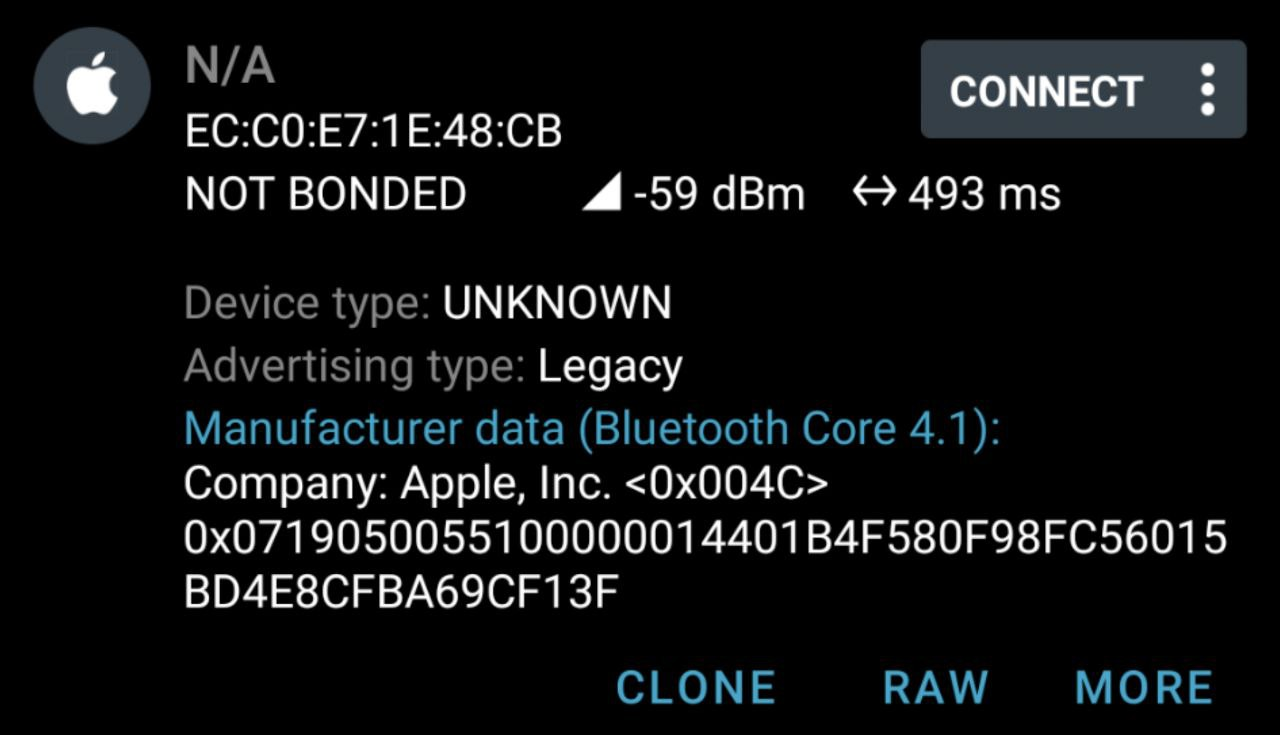
Figure 8: nRF Connect advertising data detection
- For Android users, they need to frequently run the Apple Tracker Detect application and make sure that it is updated. Be aware that this application does not run in the Implementing a project such as Amini, which scans constant BLE nearby devices, is the best approach to detect tracking AirTag devices.
[1] Are Apple AirTags Being Used to Track People and Steal Cars?. New York Times, Dec. 30, 2021
[2] Apple AirTags are being used to stalk people. CBS news, Jan. 27, 2022
[3] What to Know if You Plan to Travel Abroad With AirTags. MacRumors Apr. 23, 2021
[4] How an AirTag owner used it to find their stolen vehicle. Apple Insider Oct 14, 2021



