
Inside DarkSide, the ransomware that attacked Colonial Pipeline
November, 14, 2022
16 minutes read
By Miguel Gonzalez & Jesus Dominguez from Metabase Q’s Ocelot Team
Executive Summary
On May 7th, 2021, Colonial Pipeline reported that its digital infrastructure had been compromised due to a cyberattack, and as a precautionary measure, it would suspend its services until the severity of the situation was determined.
Colonial is the largest pipeline operator in the U.S. and transports more than 3 million barrels of gasoline, diesel, and jet fuel between the U.S. Gulf Coast and the New York Harbor area.
This cyberattack utilized ransomware which encrypted critical information systems and requested payment to recover the information.
Researchers have allegedly attributed this attack to the DarkSide group, whose modus operandi known as Ransomware-as-a-Service (RaaS), involves not only the encryption of information with Salsa20, using an RSA-1024 public key, but also the exfiltration of information used for payment negotiation.
DarkSide has affected numerous organizations in various sectors, including industry, legal, insurance, healthcare, and energy. However, according to a January 27th, 2021 publication on DarkSide’s website about its rules of use, affiliated individuals cannot target the funeral service sector, hospitals, nursing homes, or companies distributing the COVID-19 vaccine.
To pay the demands, the organization promotes the use of Monero, a cryptocurrency distinguished by its anonymity and superior security compared to other currencies in the market. DarkSide members use an administrative panel via The Onion Router (TOR) to communicate with victims and manage the delivery of the ransomware to its victims.
Government entities have already identified this specific version of the ransomware, and you can find the Indicators of Compromise (IOC) at the end of the blog.
Colonial has already faced a series of extortions so that the stolen information is not published, and it is presumed that the payment has already been made for an amount close to $5 million USD, reported zdnet. According to researcher Brian Krebs, the group’s servers have already been seized, as well as one of the cryptocurrency accounts used to pay its affiliates.
In this blog, we analyze in detail one of the DarkSide samples used during the attack, providing TTPs (Tactics, Techniques, and Procedures) and IOCs (Indicators of Compromise) that serve for monitoring, detection, and eradication strategies of this type of cyberthreats.
Main findings
- DarkSide and SODINOKIBI (REvil),although not identical, share the same modus operandi.
- DarkSide does not attack computers with the language of some of the countries formerly known as the Republics of the Soviet Union.
- DarkSide’s infrastructure is hosted with a Russian provider.
- Encryption is very fast due toa one-thread-per-processor implementation.
- It encrypts files on hard disks, removable drives, and network drives.
Initial infection
Malicious actors use techniques such as spear-phishing with malicious links to try to infect their victims. In turn, they obtain legitimate credentials through SQL Injection attacks by accessing credentials stored in databases or even in different places on the dark web where compromised credentials of organizations are listed. According to Mandiant, in the case of Colonial, the attackers used valid VPN credentials of an employee who did not have multi-factor authentication enabled, and remote access was achieved without restrictions.
DarkSide’s ransomware behavior
Once it has been possible to access a computer of the attacked organization, some versions occupy a Dropper, where their job is to decrypt DarkSide in memory (in some cases with a simple XOR) and execute it.
DarkSide:
Type: Win32 Binary – Delphi
MD5: 222792d2e75782516d653d5cccfcf33b
Name(s): net.bin, Darkside.exe
Compilation Timestamp: Dec 15, 2020 22:26:41
First time viewed: Dec 29, 2020 18:22:15
First time analyzed: Dec 28, 06:37:28
Last time analyzed: May 14, 2021 00:06:50
Country of first entry in VT: India
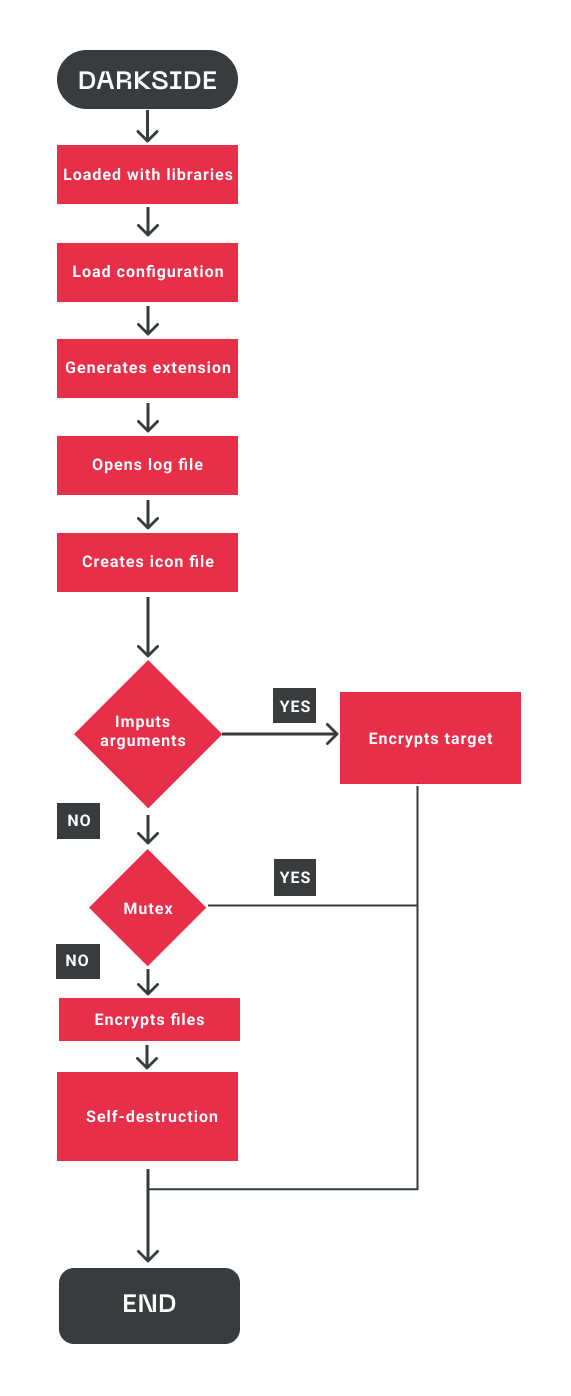
General malware scheme
The following diagram shows a general outline of the ransomware execution flow:
Configuration loaded into memory
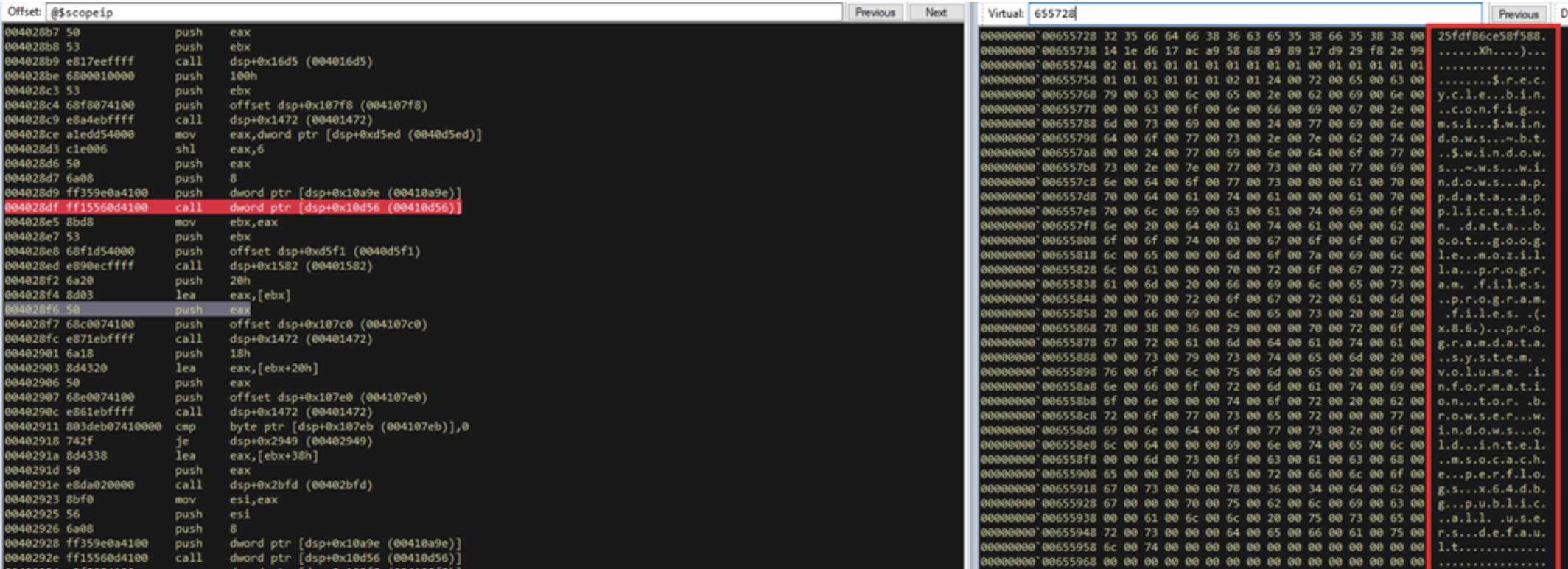
The entire malware configuration is loaded (and compressed) in the .data section in memory with a length of 2745 bytes.
When the decompression algorithm is applied, 159040 bytes are obtained with a table containing the global configuration of the ransomware (See Figure 4):
- Whitelist files
- Whitelist extensions
- Fast encryption files (these files are encrypted with a faster encryption algorithm due to their larger size)
- Name of proccesses to stop:
- vmcompute.exe
- vmms.exe
- vmwp.exe
- svchost.exe
- TeamViewer.exe
- explorer.exe
- Name of services to stop: Many of them ensure that the document is not being occupied and can then be encrypted: sql, oracle, ocssd, dbsnmp, synctime, agntsvc, isqlplussvc, xfssvccon, mydesktopservice, ocautoupds, encsvc, firefox, tbirdconfig, mydesktopqos, ocomm, dbeng50, sqbcoreservice, excel, infopath, msaccess, mspub, onenote, outlook, powerpnt, steam, thebat, thunderbird, visio, winword, wordpad, notepad
- Name of the server where the stolen data will be sent to
- The message written on the screen background
- Ransom message leaving infected directories (with an embedded key
List of whitelisted countries and languages
The ransomware makes a call to GetSystemDefaultUILanguage, which returns a Language Code Identifier (LCID) of the system and also executes GetUserDefaultLangID to get the user’s language.
The following codes correspond to the countries that fall within the whitelist. In case the system contains one of these LCIDs, the ransomware will not affect any files.
| Russian (Russia) | ru-RU | 0x419 |
|---|---|---|
| Ukrainian (Ukraine) | uk-UA | 0x422 |
| Belarusian (Belarus) | be-BY | 0x423 |
| Tajik (Cyrillic, Tajikistan) | tg-Cyrl-TJ | 0x428 |
| Armenian (Armenia) | hy-AM | 0x42B |
| Azerbaijani (Latin, Azerbaijan) | az-Latn-AZ | 0x42C |
| Georgian (Georgia) | ka-GE | 0x437 |
| Kazakh (Kazakhstan) | kk-KZ | 0x43F |
| Kyrgyz (Kyrgyzstan) | ky-KG | 0x440 |
| Turkmen (Turkmenistan) | tk-TM | 0x442 |
| Uzbek (Latin, Uzbekistan) | uz-Latn-UZ | 0x443 |
| Tatar (Russia) | tt-RU | 0x444 |
| Romanian (Moldova) | ro-MD | 0x818 |
| Russian (Moldova) | ru-MD | 0x819 |
| Azerbaijani (Cyrillic, Azerbaijan) | az-Cyrl-AZ | 0x82C |
| Uzbek (Cyrillic, Uzbekistan) | uz-Cyrl-UZ | 0x843 |
| Arabic (Syria) | ar-SY | 0x2801 |
Information collected prior to data encryption
Before starting file encryption, certain information about the infected host is collected:
- lang: Language configured in the system
- username: Current user name
- hostname: Name of the machine
- domain: Determines if it is attached to an AD
- os_type: Operating system type
- os_version: Malware version, in our case 1.8.6.1
- os_arch: Architecture: x86 o x64
- disks: Ratio of free space versus total disk space
- id: Machine guide, universal device identifier
The previous information is printed in a template, with a JSON format as shown below:
“os”:{“lang”:”%s”,.”username”:”%s”,”hostname”:”%s”,”domain”:”%s”,”os_type”:”windows”,”os_ve.sion”:”%s”,”os_arch”:”%s”,”disks”:”%s. “,”id”:”%s”}
The generated sequence is printed in the following format:
%.8x=%s&%.8x=%s
Giving the following result:
88bed015=/LkZFINJp3VPMHYvngh5vC5eEnPRdbWNJteVfehRLo+C+fI+92EFe5qDvzMSxSE6vLXevA3RamgvvsHXxbuTZW/ED+t\iA3ggKHt9Y8FWVkC04KzDmMKeWdceobah6jiNiNLNbbrvbJJc5HjR3YHdGZ9HZshkQBBcpLHYcJeTw/BHI7IkXn9yF7QV+cpnXFI4e5LzUWnSQiI2/r/RJQTD4XLe9iw8+ABn+JomDvYyItMtMxYO108S+YhWRnUYRcGdQApssFrHGZtnaVKdfkQC8xGajUk1c5NYWM/bQsQLHCfD+w85z/zw4em86BotyC08JdZkhDp/4xjQwWLoExd3FrqYKaLtCnBd5DkfDtBlB36mVEBsaXwYlOiA2Kaji2sMFxXeMhMAA6k=&eeeb0f66=25fdf86ce58f588
This information is sent to the attackers’ central server via HTTP POST request, located at securebestapp20[.]com, a domain created on September 16th, 2020, which is hosted on the infrastructure of the Russian provider Eurobyte (eurobyte[.]ru), which according to SpamHaus, was one of the most used providers for running botnets in 2020 (See Figure 2).
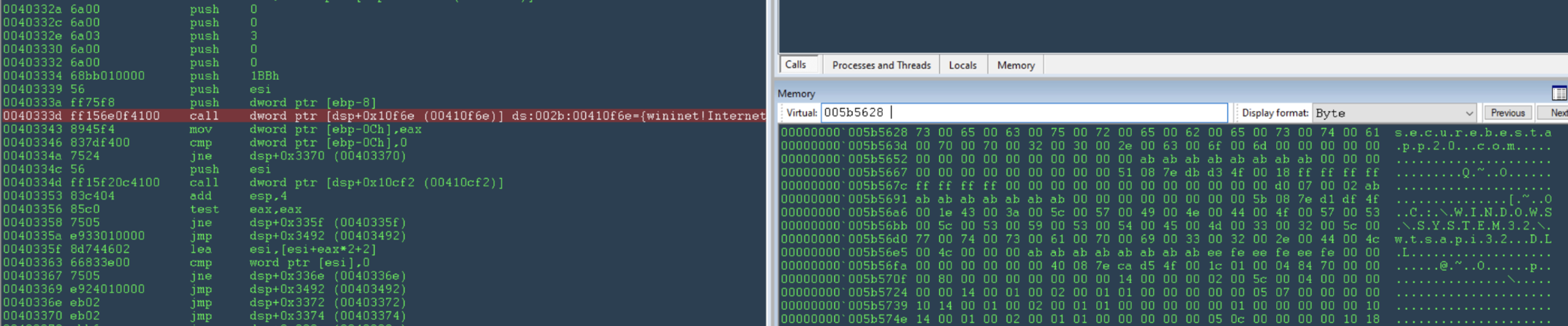
Interestingly, the User-Agent used for communication with the C2 is malformed. At first glance, everything looks normal, but when we look closely at the rv:79.0 field and the Firefox/80 field, we notice a discrepancy. According to the standard, these two fields should be the same, so it may be a factor used by the server to only accept connections from the ransomware controlled by them.
Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:79.0) Gecko/20100101 Firefox/80
In Figure 3, you can see the moment when the domain is accessed using the Windows Internet Connect API.
File encryption
In case the malware decides to continue with the encryption (if it is not discarded by the whitelist), it uses a recursive main function that scans each directory of the identified logical drives (see Figure 4):
- Removable drives: Floppy, Thumb drive, flash card
- Hard drives in the computer
- Mounted network drives
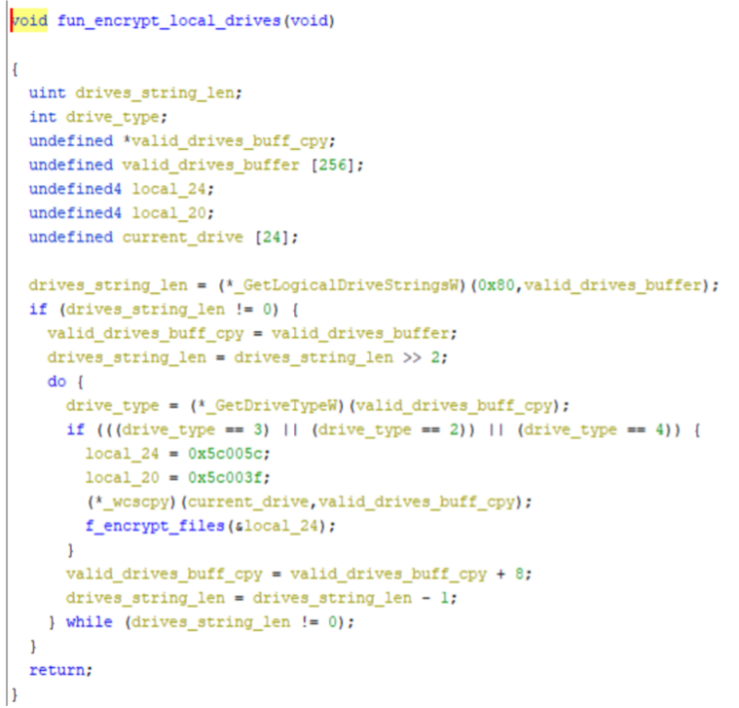
The general process is detailed in the flow diagram in Figure 5.
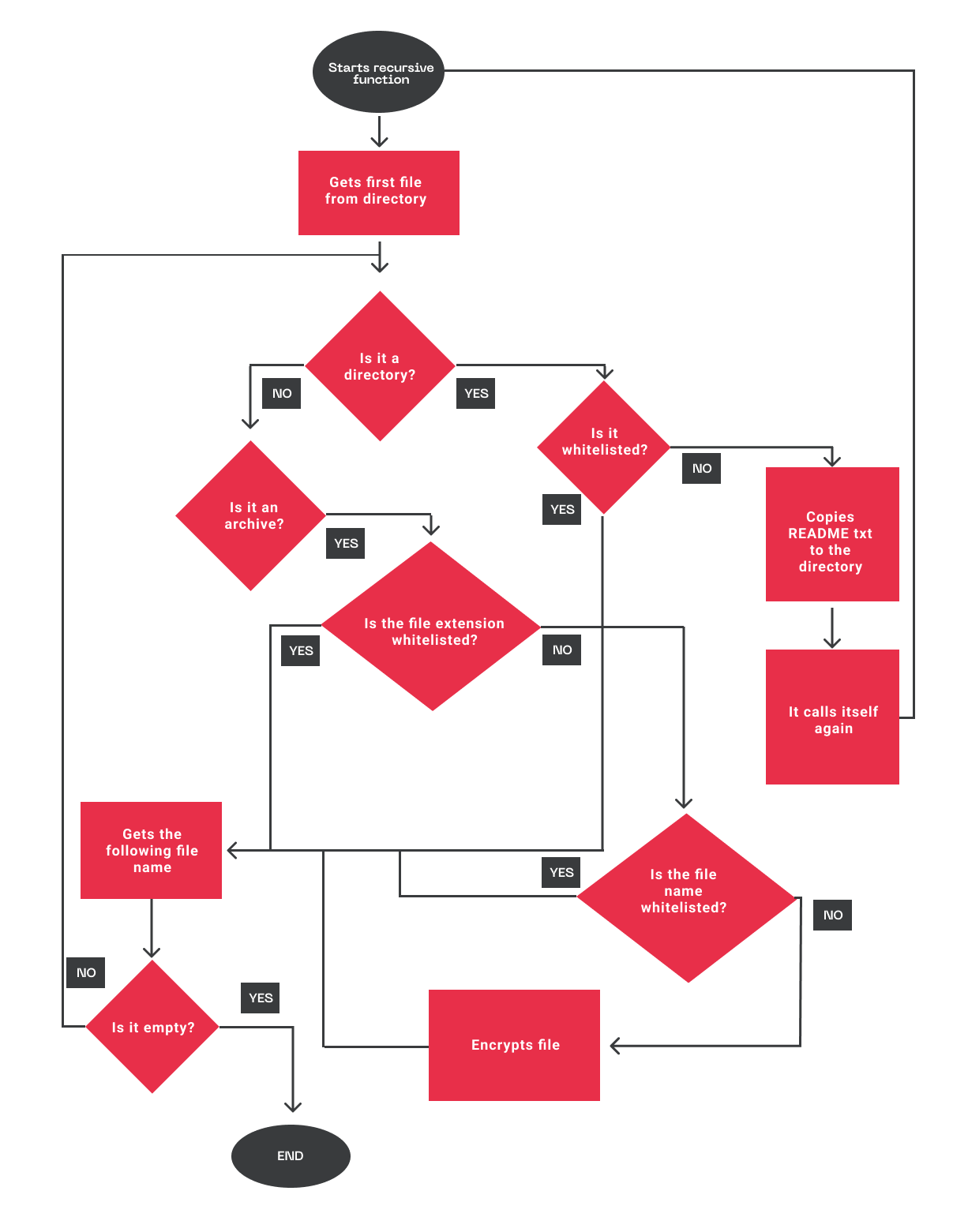
The process starts by evaluating whether the path has a directory. If it does, the process copies the “readme” file with the attackers’ message to that destination.
If not, the path is viewed as a file and the process evaluates if the filename is present in the whitelist embedded in the malware, as shown below:
- autorun.inf
- boot.ini
- boot
- font.bin
- bootsect.bak
- desktop.ini
- icon
- cache.db
- ntldr
- ntuser.dat
- ntuser.dat.log
- ntuser.ini
If the file contains one of the following extensions, it is not encrypted:
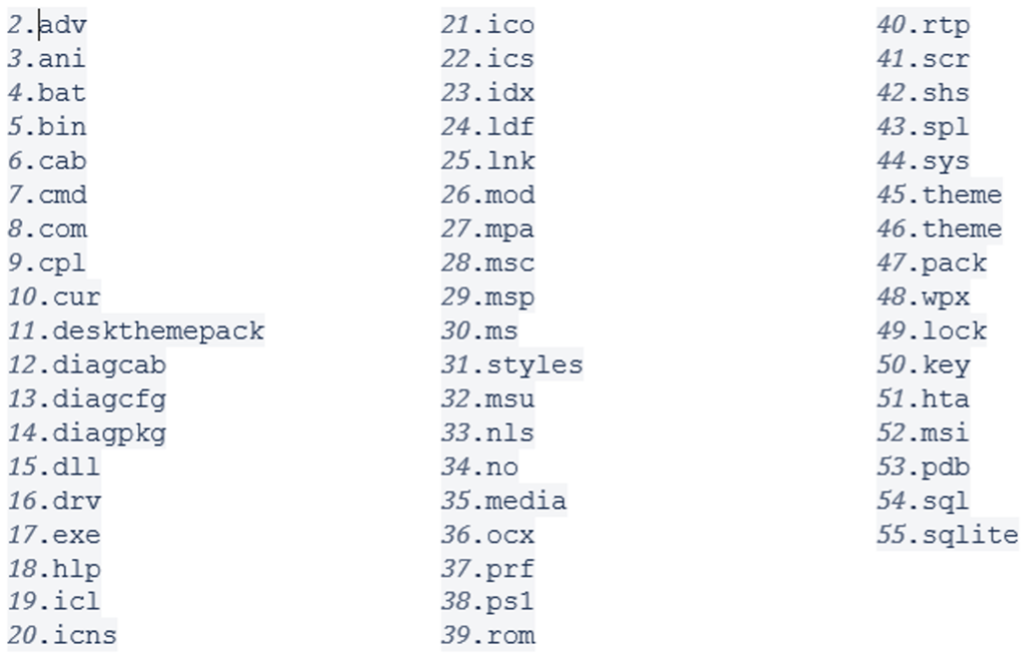
After making the initial validations, the malware proceeds to encrypt the files swiftly by occupying one thread per available processor following the following steps:
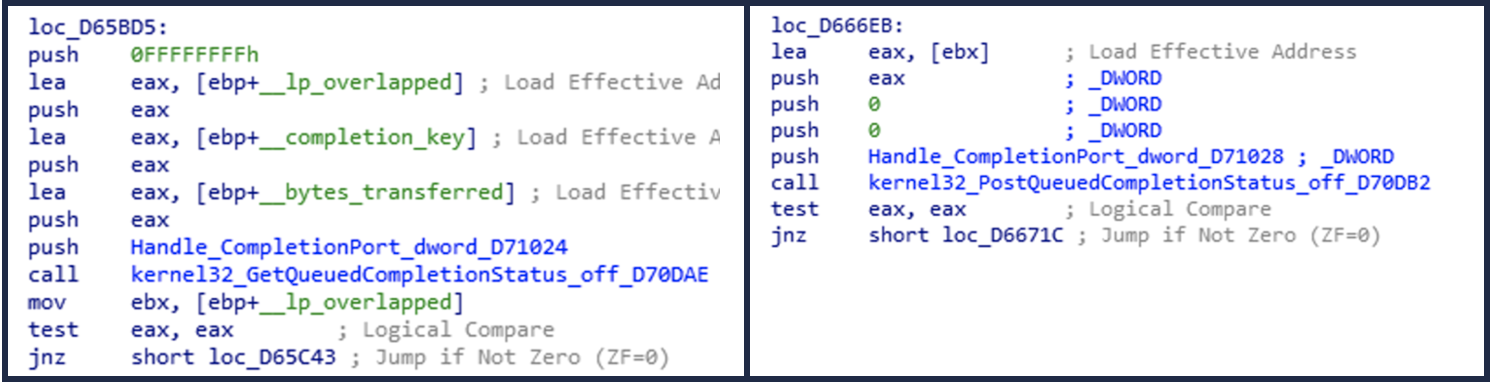
- An input/output (e/o) completion port is created via the CreateIoCompletionPort API
- Files to be encrypted are added to a queue via PostQueuedCompletionPort API
- The encrypted files are obtained from the queue via GetQueuedCompletionPort
The file to be encrypted is passed to the function at address 0xD6209C, which starts this process. Figure 6 shows the use of the APIs to enqueue and remove encrypted files.
The use of the stream cipher Salsa20 for file encryption is confirmed. In Figure 7, we can see the quarter-round function described in Wikipedia, which is used to customize the matrix, and on the right side (in the function sub_D6209C), the implementation made by the malware.
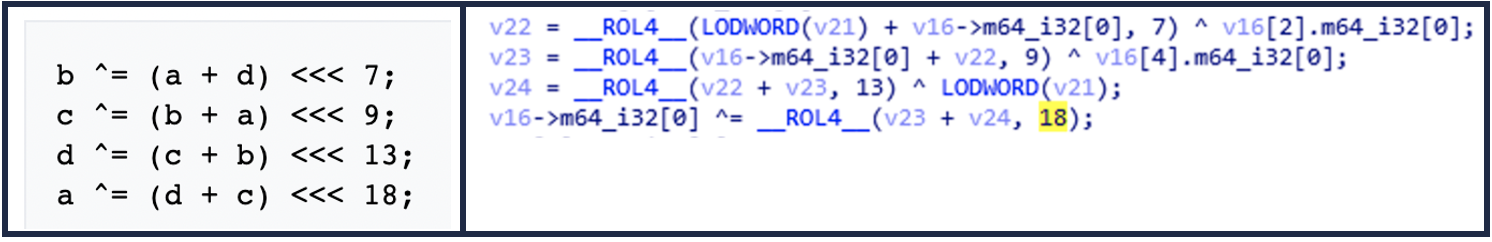
With this matrix, a 64-byte block is generated and used to encrypt the files, to which this block (encrypted with RSA) is also added at the end. In Figure 8, you can see the encrypted block in memory and how it ends up being added to the encrypted files on disk.
Once the files have been encrypted, the following information is sent to the server:
- id: Previously generated victim ID
- uid: again the victim’s ID
- enc-num: number of infected files
- enc-size: total number of encrypted bytes
- skip-num: number of files that were not encrypted (on the whitelist)
- elapsed-time: length of time of infection
Shadow copy removal
Shadow copies are a mechanism by which Windows generates a backup of the information, if they are deleted, there is no way to restore the information once encrypted.
In the case of DarkSide, the command is encoded in hexadecimal and uses the call to CreateProcessW to invoke it as follows:
powershell -ep bypass -c “(0..61) | % {$s+=[char][byte]
Which via VMI, it gets the shadow copies and deletes them:
Get-WmiObject Win32_Shadowcopy | ForEach-Object {$_.Delete();}
Generation of the wallpaper
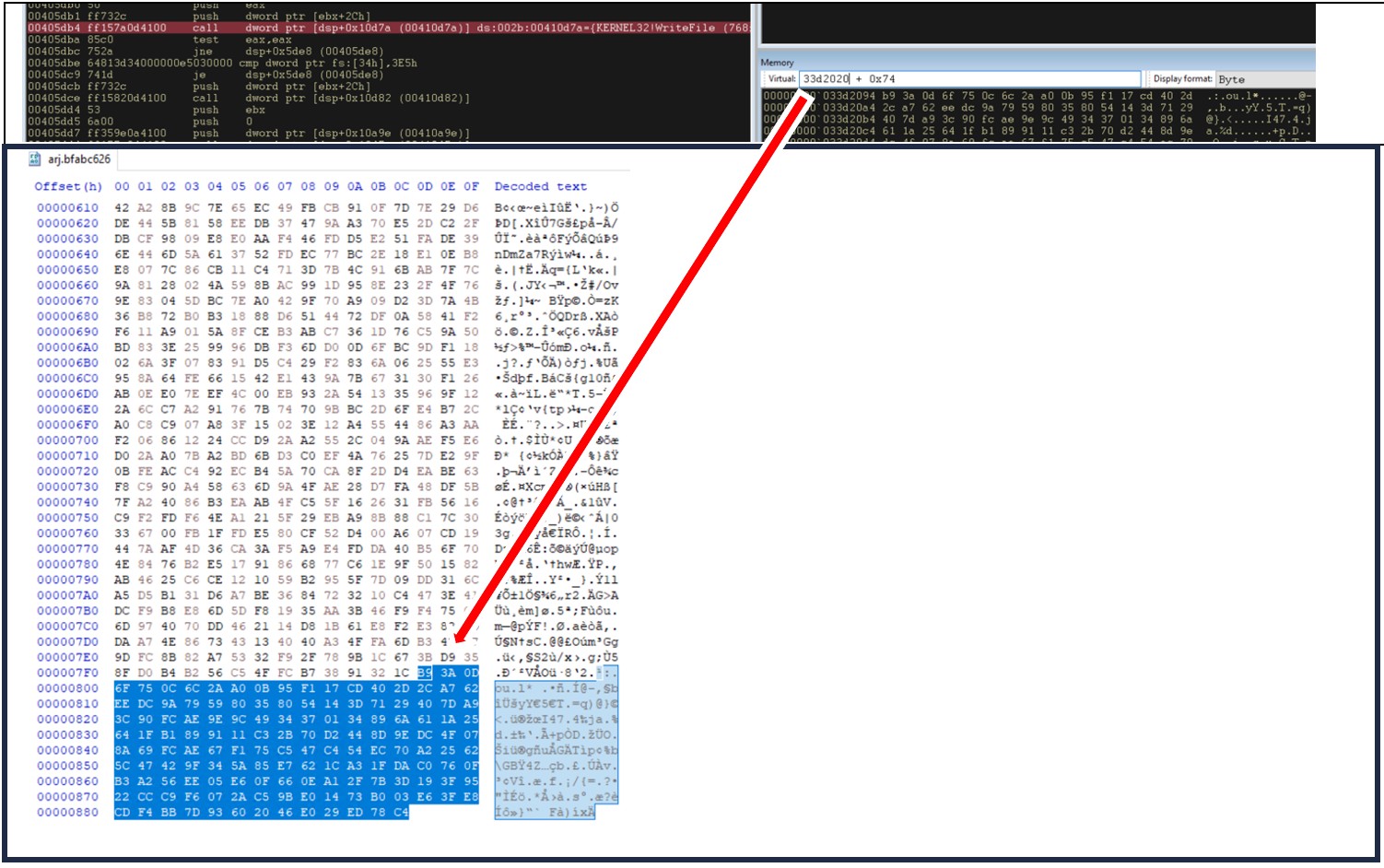
Once the victim’s files have been encrypted, the malware will change the wallpaper of their computer to inform them. The image seen in that wallpaper is generated by the malware and is stored in the C:\ProgramData directory <id>BMP with <id> being the id generated for that particular victim, as shown in Figure 9.
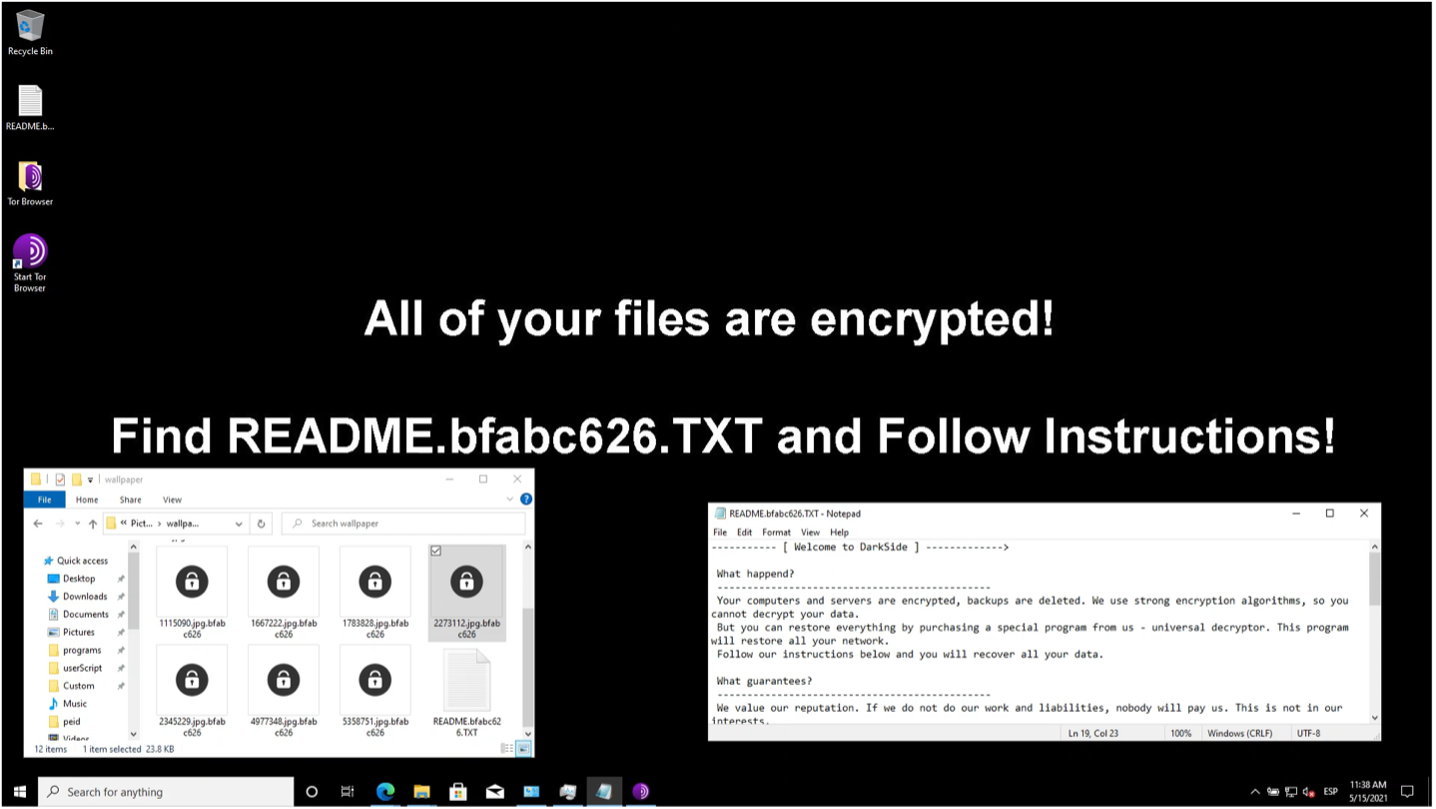
Cleanup after encryption
Once the file encryption tasks are finished, the malware deletes itself, usually to make forensic analysis more difficult. For this task, it calls ShellExecuteW function with the following command:
cmd.exe /C DEL /F /Q C:\%USERNAME%\<ruta_del_malware>\darkside.exe >> NULL
DarkSide and REvil similarities
// Configuration
In both cases, the binaries occupy a configuration that is encrypted and embedded within the data section of the binary. This configuration in both cases affects some parameters of the execution, in addition to containing the address of the connection server and the attacker’s public key. However, the format differs; while REvil uses a single string with JSON format, DarkSide has a division between the configurations and the public key. In addition, for DarkSide, the configuration after being decrypted must be unpacked. Figure 10 shows these differences:
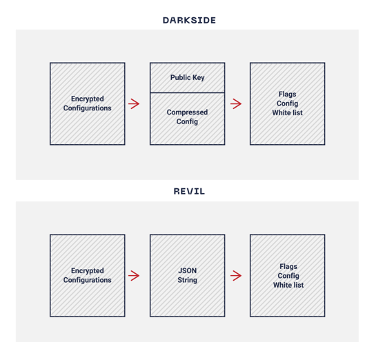
// Generation of the Mutex
// Packaging
The REvil executable is packaged with a custom algorithm, making it much more challenging to analyze, while all DarkSide samples found so far are unpackaged.
// Generating the file extension
Recommendations
Ransomware attacks have become the top method used by attackers worldwide to obtain large amounts of money in a short period of time. ransomware payments have tripled from 2019 to date. In the case of Colonial, due to the critical nature of their business and the need to restart operations immediately, the company did not have many options but to pay the total of $5 million USD. Unfortunately, ransomware attacks are global and are increasing in frequency and scale.
In Latin America and Mexico, the cases continue to rise. In November 2019, the IT systems of PEMEX were compromised by ransomware; according to bleepingcomputer, attackers asked for the sum of $4.9 million USD. In 2021 alone, we’ve seen attacks on multiple Mexican institutions, including banks, with gigabytes of information were leaked on the deep web, due to a possible lack of payment, along with an attack on the National Lottery of Mexico.
Why are ransomware attacks growing exponentially?
The ease of executing ransomware attacks through services known as ransomware as a service (RaaS) reduces the barriers of entry. RaaS allows non-technical people to hire a service that allows them to compromise companies with minimal effort, sharing profits with the creators of the service.
How can we combat this threat that is here to stay for years to come?
First of all, accept that sooner or later, your organization is going to be infected with ransomware unless you proactively make changes. The first step is to strengthen your processes, people, and technology by testing your systems against a ransomware attack. Metabase Q offers a different spin on ransomware as a Service via its APT Simulation service. By replicating multiple ransomware families like WannaCry, Ryuk, REvil, DarkSide, Avaddon, etc., in your network, we are able to test how well your systems would respond. The benefits include:
This new service reverse engineers emerging threats such as ransomware to reproduce the malicious code. Unlike RaaS, Metabase Q has the control to execute the ransomware without the potential side effects of irreversible damage, such as deleting shadow copies or publishing sensitive information on the Deepweb. By utilizing the TTPs (Techniques, Tactics, and Procedures) and IOCs (Indicators of Compromise) used by malware in the real world, we can train and strengthen your processes, people, and technology.
We train your team to detect and fight real ransomware in your organization without having to pay millions of dollars for the ransom. Contact us at: contact@metabaseq.com
Thank you, Bryan Gonzalez & Jose Zorrilla from Ocelot, for your support during this analysis.
Indicators of compromise (IOCs)
// Registry Changes
// Created files
C:\%USERNAME%\AppData\Local\bfabc626.ico
C:\ProgramData\bfabc626.BMP
C:\%USERNAME%\AppData\Local\Temp\3582–490
//URLs seen
The last part is variable so it is not recommended to use it as a detection pattern.
hxxp://securebestapp20[.]com/mhzPjMHjEl
hxxp://securebestapp20[.]com/mhzpjmhjel
hxxps://securebestapp20[.]com/i7zMFQGyg0
hxxp://securebestapp20[.]com/adbeeccba
hxxps://securebestapp20[.]com/TpqTgJUS3v
hxxp://securebestapp20[.]com/ddbcebcd
hxxp://securebestapp20[.]com/bbaededade
hxxps://securebestapp20[.]com/Fg7xJ8MG6
Binaries communicating to securebestapp20[.]com
F9fc1a1a95d5723c140c2a8effc93722
F75ba194742c978239da2892061ba1b4
Cfcfb68901ffe513e9f0d76b17d02f96
9d418ecc0f3bf45029263b0944236884
91e2807955c5004f13006ff795cb803c
6a7fdab1c7f6c5a5482749be5c4bf1a4
3fd9b0117a0e79191859630148dcdc6d
222792d2e75782516d653d5cccfcf33b
E44450150e8683a0addd5c686cd4d202
C2764be55336f83a59aa0f63a0b36732



