Optimizing Incident Detection and Response: Real-Time Security for Endpoints
March, 28, 2025
4 minutes read

Managing efforts for cybersecurity incident detection and response involves defining multiple elements of strategic, tactical, and operational nature to ensure an effective response within the organization. Below are these elements, integrating specialized solutions like Batuta to optimize protection and response on endpoints.
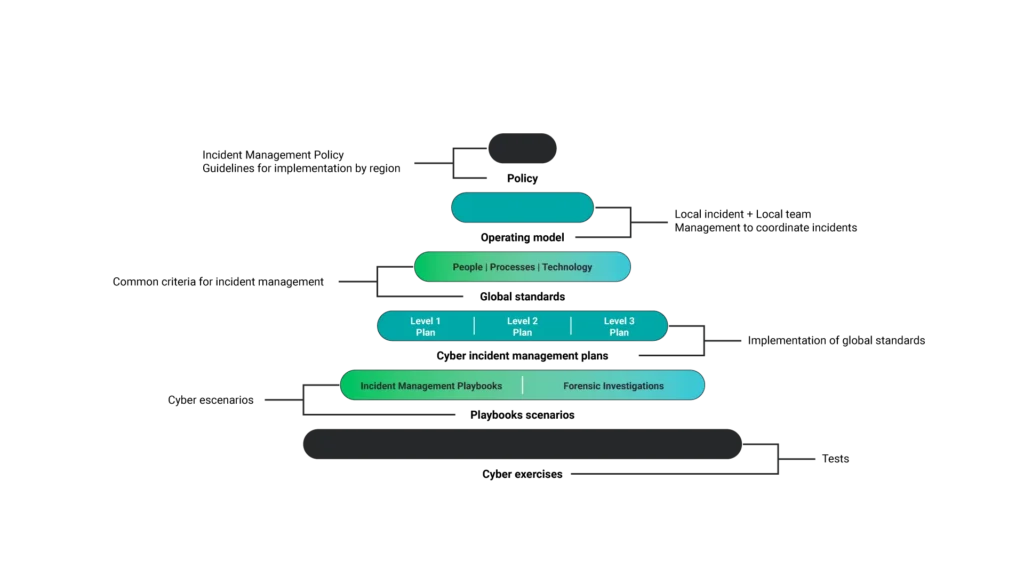
Policy
The Incident Management Policy is a strategic element that establishes the guidelines and roles necessary for implementing response processes. This policy clarifies who is responsible for what and organizes communication across different phases, from preparation through recovery.
Operational Model
The operating model determines the structure and coordination of the incident response team.
| Local Response Model | Global Response Model |
| Local Coordination with Global Support. Local teams can handle incidents without compromising security. | Global Coordination with Local Support. Major incidents requiring a unified response. |
Beyond defining roles and procedures, it is crucial to have tools that allow continuous security monitoring of endpoints. In this context, Batuta integrates as a solution that:
- Enables real-time monitoring of the security posture of each endpoint.
- Facilitates the immediate implementation of corrective actions upon detecting anomalies.
- Effectively connects local and global teams through a centralized view of the situation.
While local teams can have permanent staff (fixed roles), virtual staff (not exclusively dedicated to incidents), or hybrid members (both permanent and virtual), the expected structure typically includes the following core members:
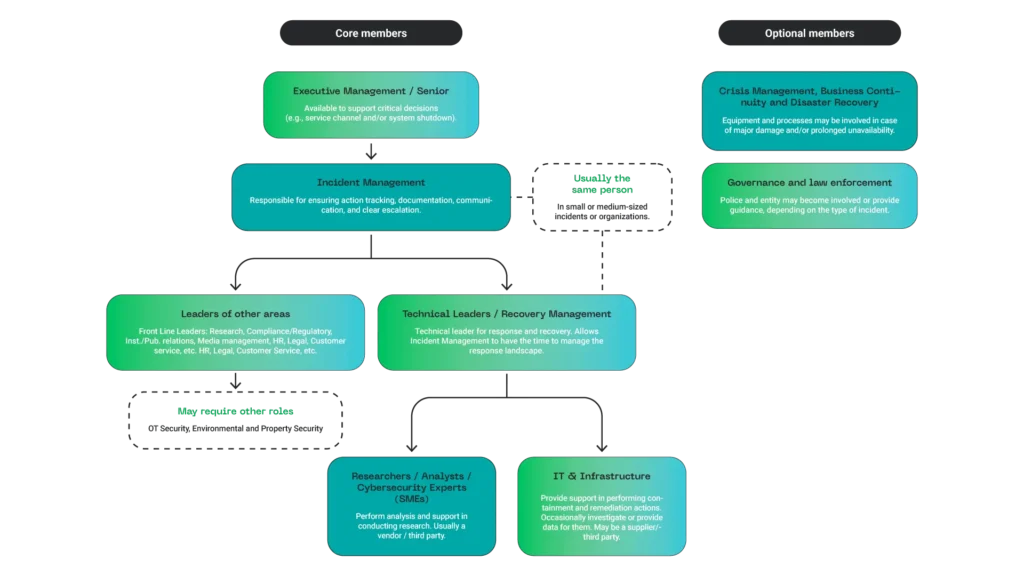
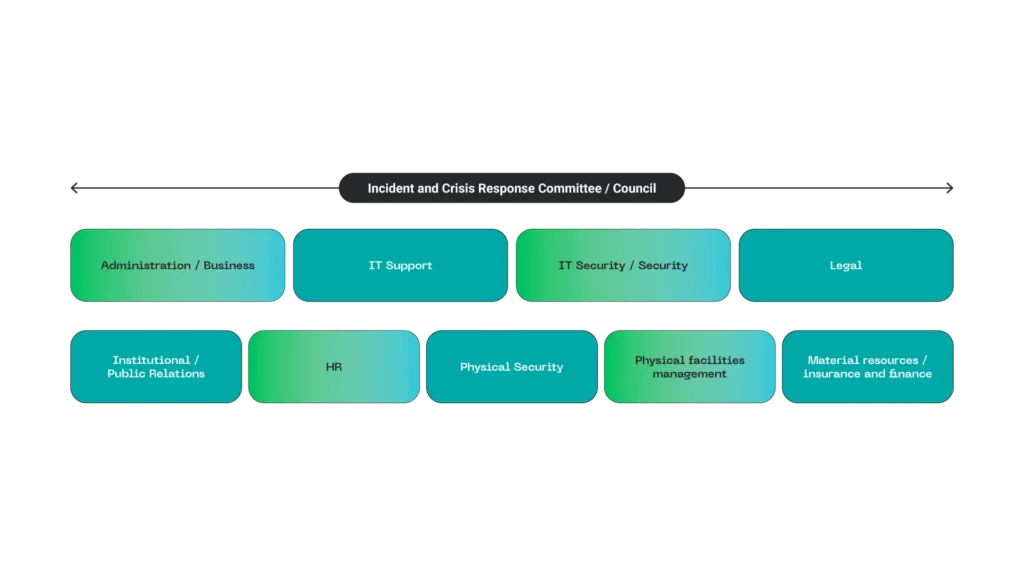
Given the need for global coordination in crisis management, it is common to create one or more committees that provide a cross-organizational view of incidents and their impacts. The structure of participating roles involves considering the following management aspects within the organization:
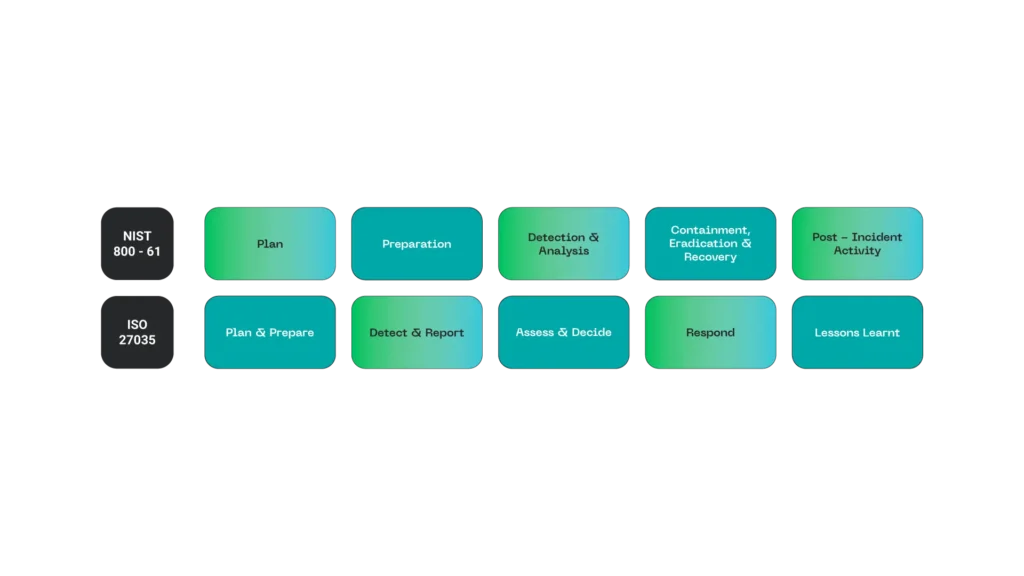
Global Standards
To ensure a coherent response aligned with international best practices, organizations must adhere to recognized standards, such as:
- NIST SP 800-61: Computer Security Incident Handling Guide.
- ISO/IEC 27035: Information security incident management.
Compliance with these standards establishes clear rules for coordination and delineation of efforts, ensuring that every action is backed by proven processes.
Incident Management Plans
Traditionally, incident management plans rely on structures such as Security Operations Centers (SOCs) to monitor, analyze, and respond to threats. However, the integration of Batuta allows for:
- Centralized incident management through continuous endpoint monitoring, eliminating sole dependence on a SOC.
- Automation of incident responses via preconfigured scripts, accelerating threat containment and remediation.
- Real-time audits and validations that significantly reduce response times to any anomalies.
Thus, Batuta positions itself as a solution capable of optimizing and complementing traditional response processes, providing agility and precision in incident management.
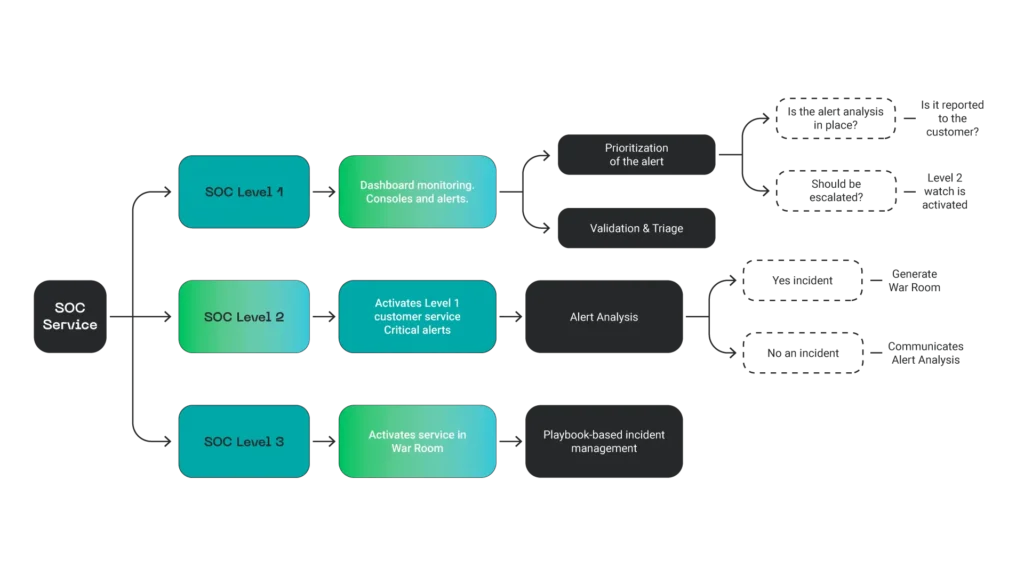
Playbook Management
A security playbook defines the procedures an organization will follow in various incidents. Implementing playbooks becomes even more effective by incorporating solutions like Batuta, as it:
- Allows the management and execution of playbooks directly on endpoints, ensuring that each action is automated and executed in real-time.
- Facilitates the adaptation and customization of playbooks according to the specific needs of the environment, covering scenarios such as malware infections, ransomware attacks, credential theft, or cloud incidents.
- Offers continuous updating and validation of playbooks through simulations and audits, ensuring their effectiveness against emerging threats.
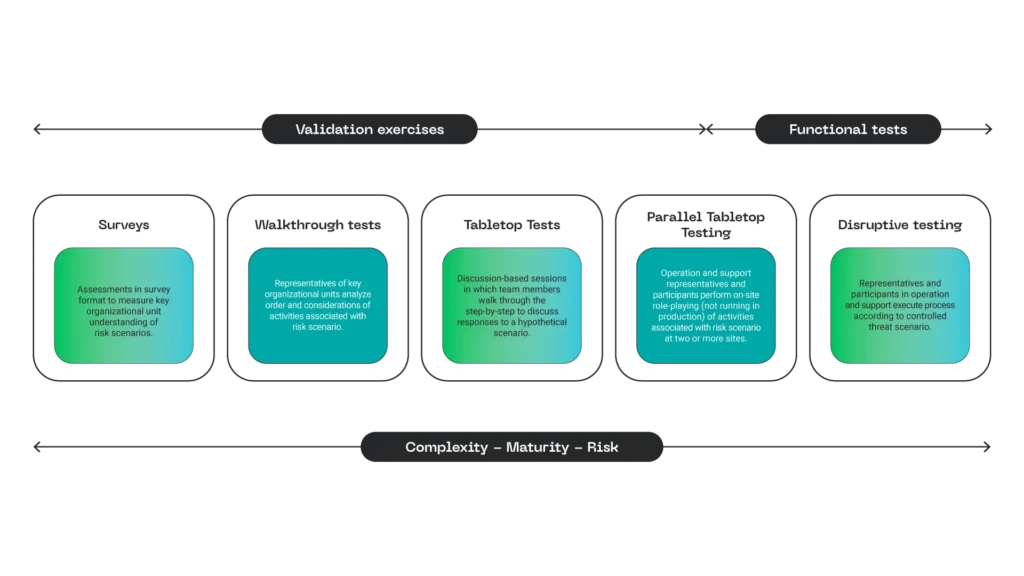
Cyber Exercises
Cyber exercises are a vital element, providing methods to familiarize roles with different threats, as well as testing, validating, and enhancing incident management plans and playbook definitions, ensuring their implementation remains relevant and effective.
Conclusions
Incident detection and response is an integral process encompassing the definition of policies and operating models, the implementation of global standards, and the execution of cyber exercises. In this framework, endpoint management becomes a critical component. Integrating specialized solutions like Batuta enables:
- Real-time monitoring of endpoint security.
- Automation of responses through preconfigured scripts and immediate actions.
- Management of playbooks and validation of responses to incidents.
This way, Batuta complements and enhances traditional processes, offering a centralized, agile response aligned with international best practices.




