Neshta and Avaddon groups teaming up to infect Mexican company
November, 25, 2022
10 minutes read
By Miguel Gonzalez from Metabase Q’s Ocelot Team
Ransomware-as-a-Service is on the rise worldwide, and Mexico has become a target. Just a few days after the group Avaddon announced the compromise of Loteria Nacional, Ocelot detected a second variant of the malware targeting another company in the same country. In this blog, we present the analysis of Avaddon, its connection with Neshta, and the Tactics, Techniques and Procedures (TTPs) and Indicators of Compromise (IOCs) identified to help organizations take preventive actions.
New infection of a Mexican company
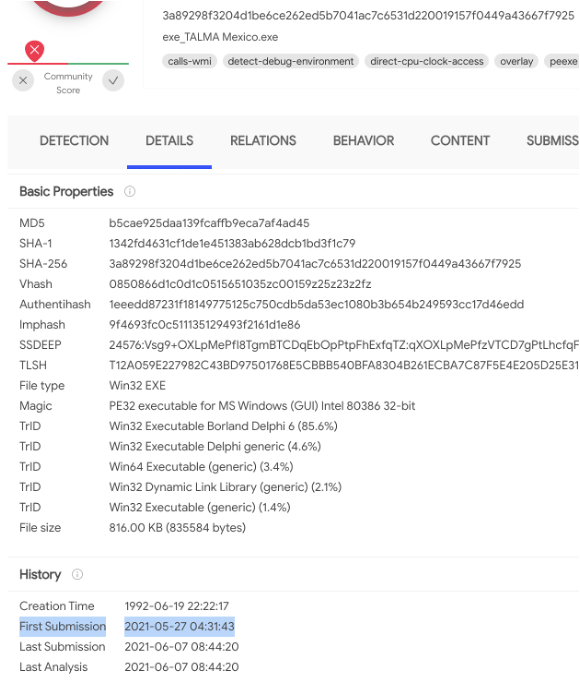
On May 27, 2021, Ocelot identified an executable file with the name exe_TALMA Mexico.exe (see Figure 1) infected with Neshta, a file infector present since 2003, which appends itself to executables to try to avoid detection. Neshta is commonly used inside installers, luring victims to download it from malicious or compromised websites, but in this case it was used differently.
Neshta & Avaddon collaboration
Usually, attackers use Neshta to infect benign files. However, in the identified file, attackers infected a sample of Avaddon Ransomware, which helps bypass detection to encrypt the victim’s files. The steps are as follows:
- Neshta copies the first 41472 bytes of the original file (Avaddon) into a buffer
- Then it replaces those 41472 bytes of the file with its own content
- At the end of the file, the chunk of Avaddon extracted at step 1 is copied
- Finally, when the user tries to open the infected file, it will always run Neshta first, which will then reconstruct the original executable of Avaddon and drop it into a temporary directory (%Temp%\3582-490) to finally execute it
In Figure 2, we can graphically see the infection and execution process.
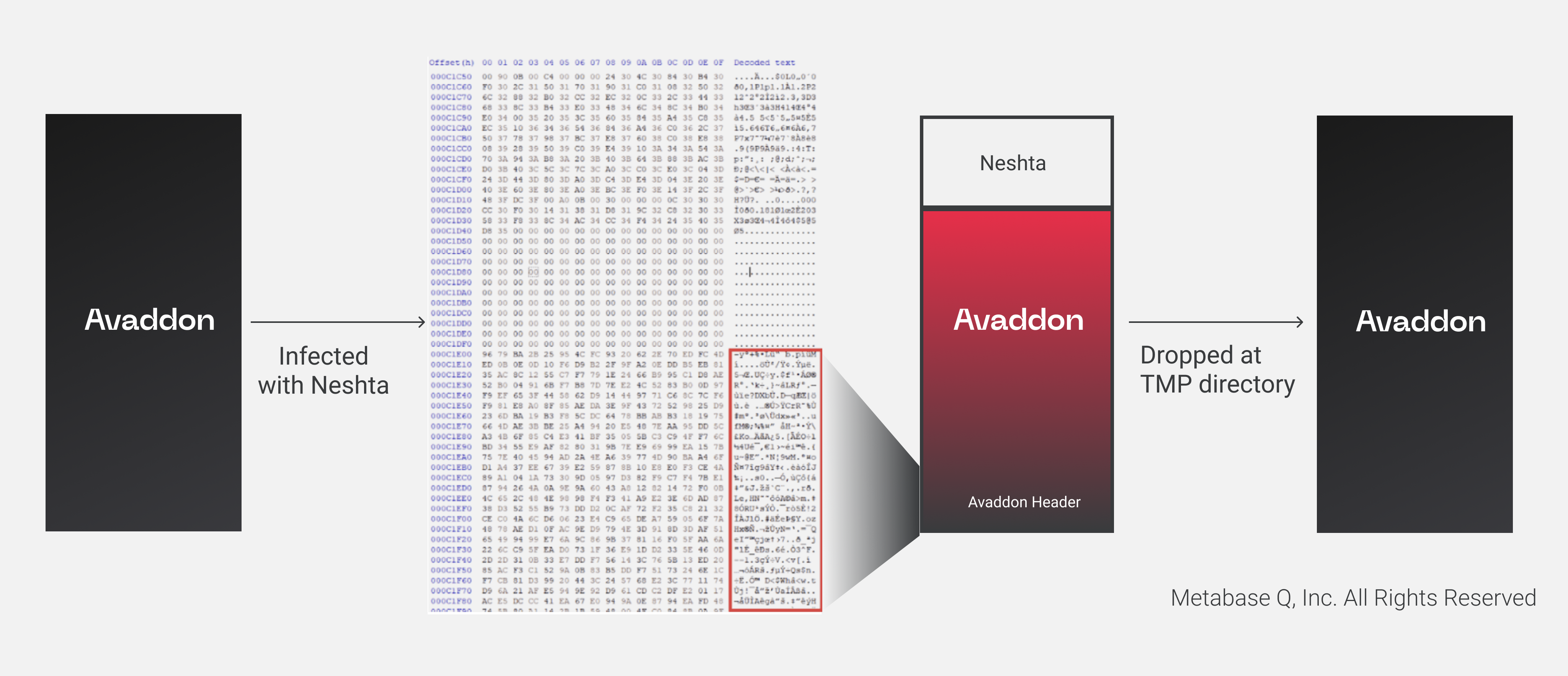
Avaddon Ransomware is dropped and executed by Neshta. This action is not an accidental infection since threat actors must control the activities performed by Neshta to avoid disruption of Avaddon’s operations. For example, both types of malware can exfiltrate information, but only one can operate at a time. To achieve this level of interoperability, the Avaddon Ransomware requires the source code of Neshta.
As further evidence of potential collaboration, the Neshta threat actor comes from Belarus. Interestingly, Avaddon does not infect companies in the Commonwealth of Independent States (CIS), including Belarus.
By debugging the Neshta process, we can grab the Avaddon sample dropped into the %Temp%\3582-490 directory (see Figure 3).
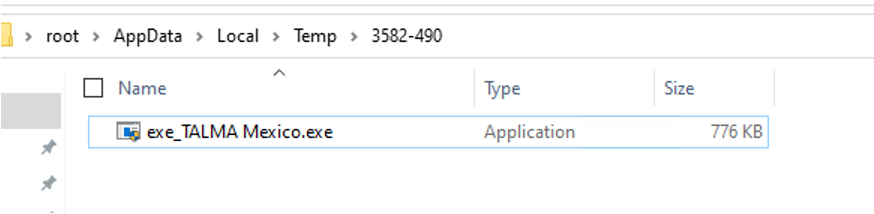
We can now observe that this executable has a small icon indicating that administrator access is needed to run this binary.
Other actions made by Neshta
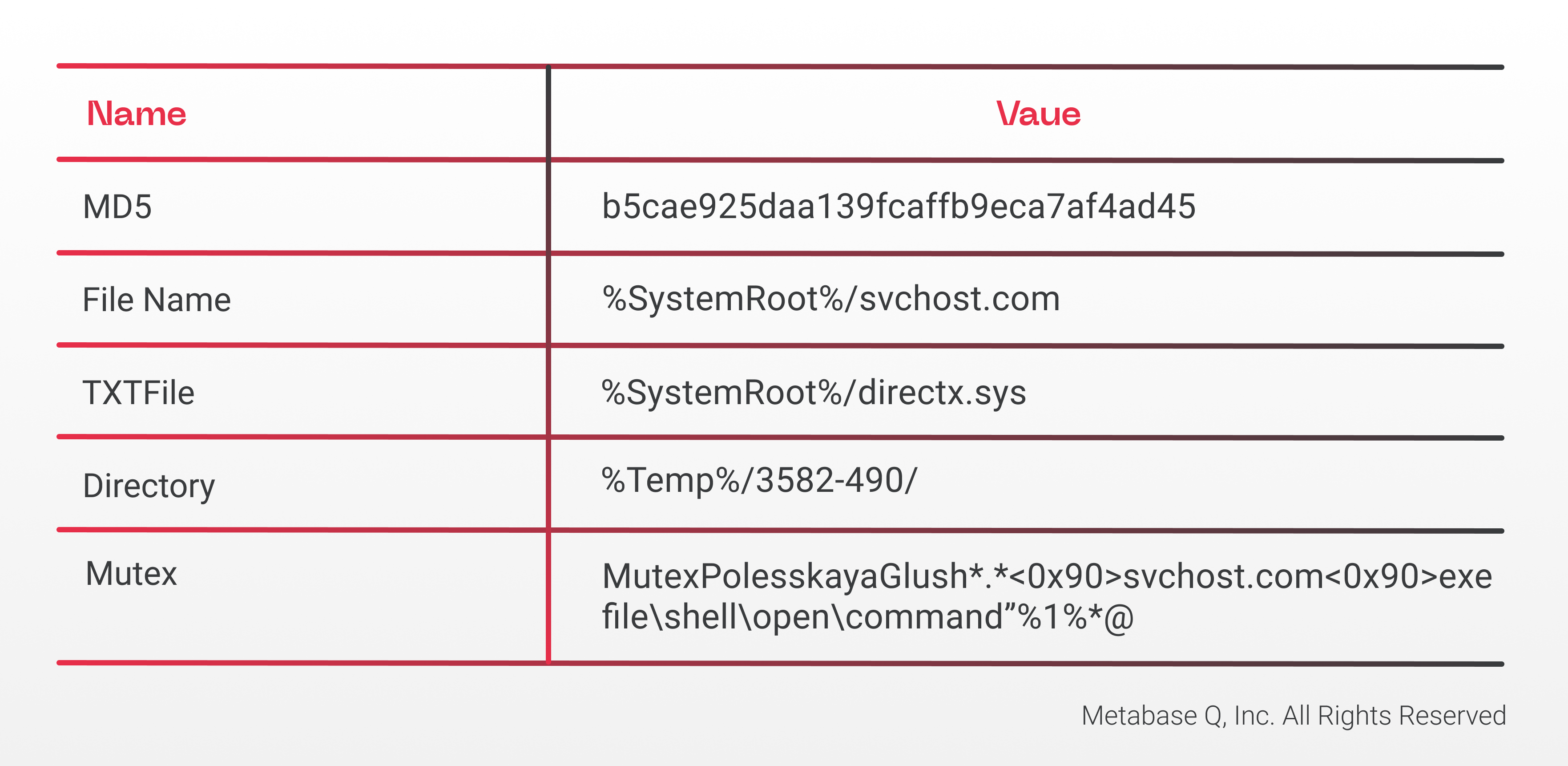
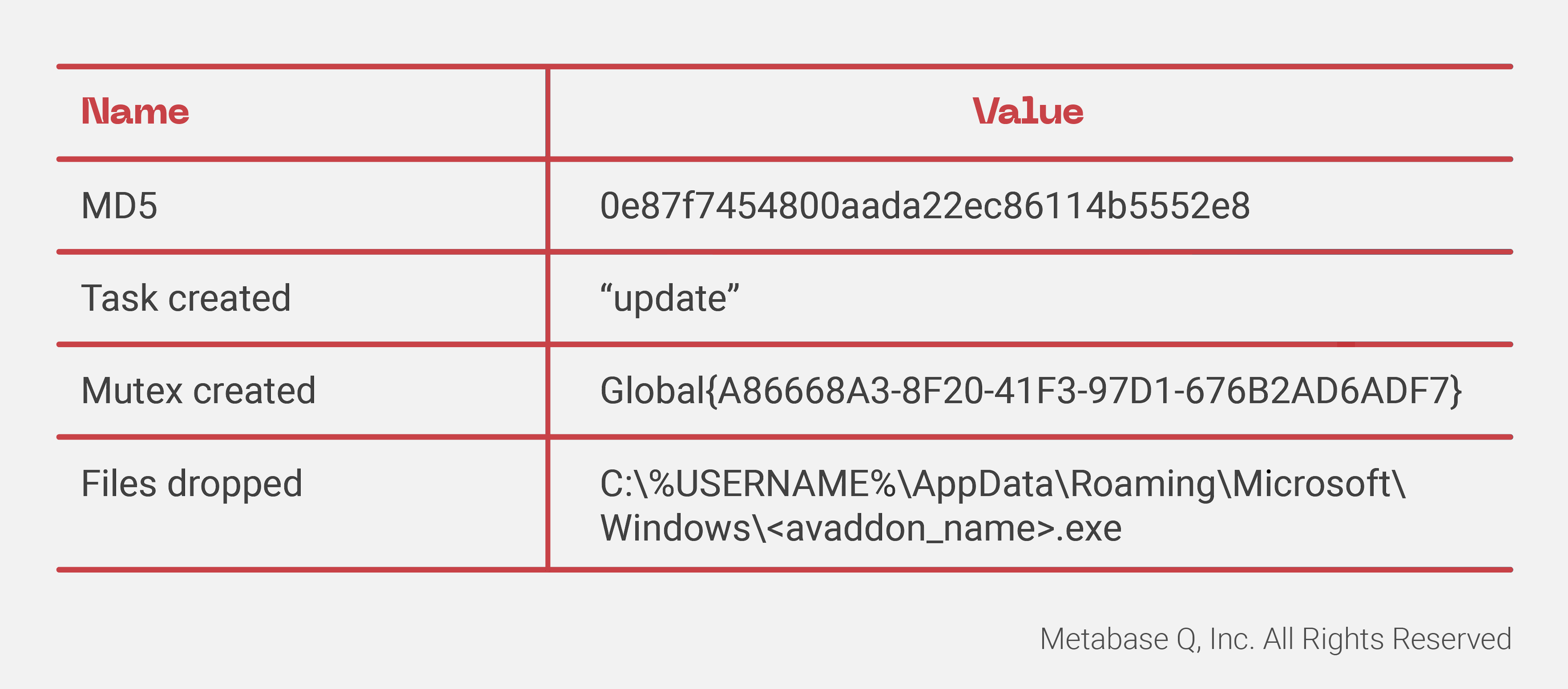
- Mutex creation: Makes sure there is not more than one process running. Mutex name:

- File drop: Copy itself to Windows directory as svchost.com pointed by %SystemRoot% environment variable:
C:\Windows\svchost.com
- Persistence: Registry key altered: To execute Nestha every time the user runs another executable, gaining persistence
Value: %SystemRoot%\svchost.com %1 %*
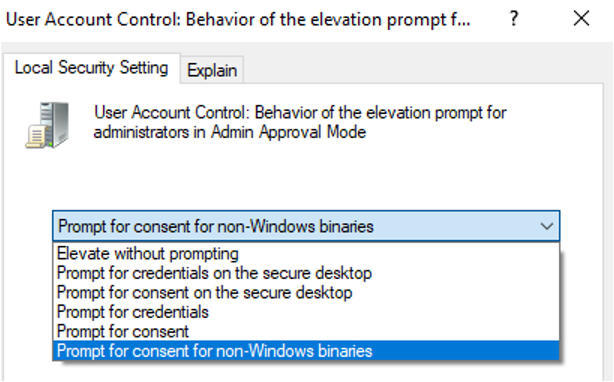
- Privilege Escalation: Disabling UAC consent prompt to obtain elevated processes without the user knowledge
Value: 0
A value of 0 is equivalent to a configuration of the UAC to elevate a process without the UAC prompt, as seen in the Figure 5
Connecting Avaddon with TALMA Organization
Upon initial investigation, we realized that we were dealing with an Avaddon sample. Considering that the sample was found to Virustotal in Mexico and that the name in the binary “TALMA” was probably related to a Mexican company (see Figure 6), we decided to look at the malware to confirm the information. Just a few days earlier, this group had compromised the Lotería Nacional.
However, upon looking at the Onion Forum from Avaddon, TALMA was not listed there. We concluded that it was probably only an attempt to infect them.

On June 5th, in the mist of our analysis, the Avaddon group added TALMA to its target list, confirming our suspicions (see Figure 7).
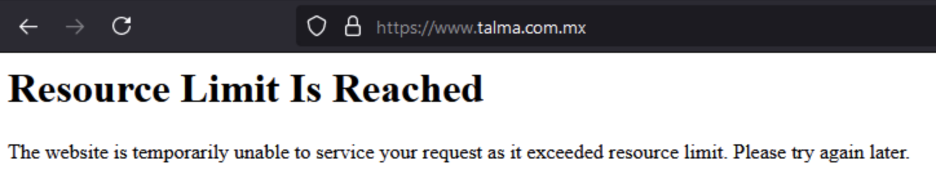
On June 9, we realized the TALMA website was down due to a DoS attack, a known behavior from this group to reprimand companies that are not cooperating (see Figure 8).
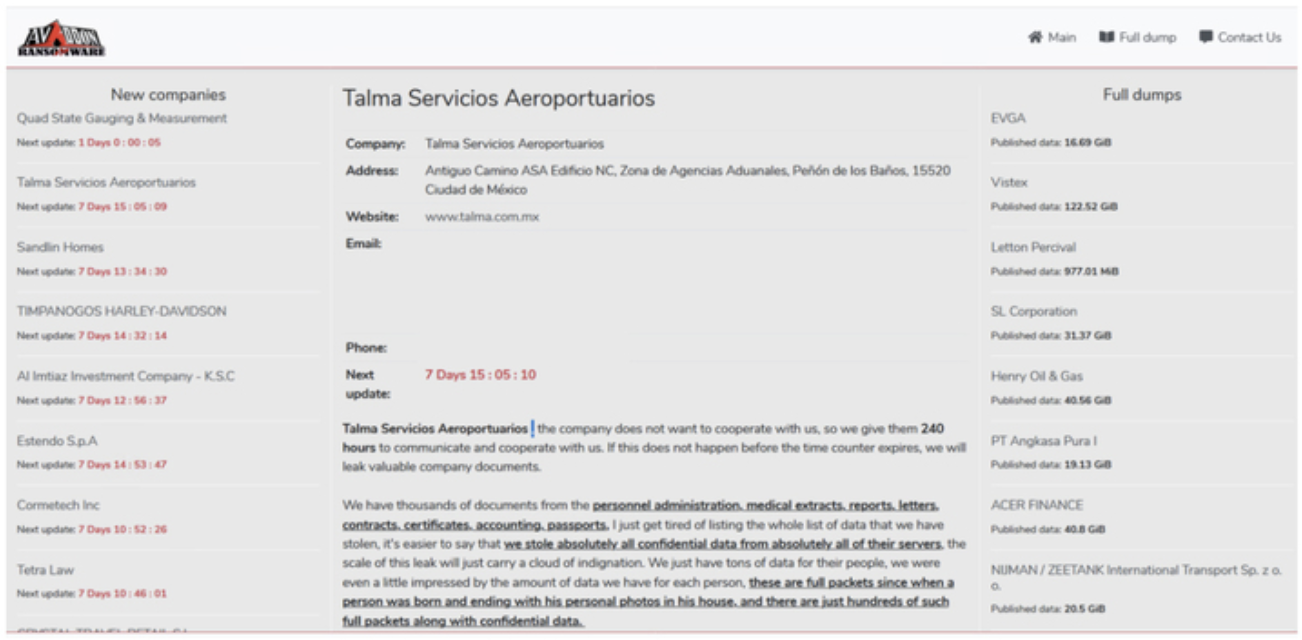
As the company continued to refuse to pay the ransomware and cooperate with the attackers, part of the information collected from their systems was leaked.
Avaddon Technical Analysis
Compiler: Visual Studio 2015
Architecture: x86
Persistence
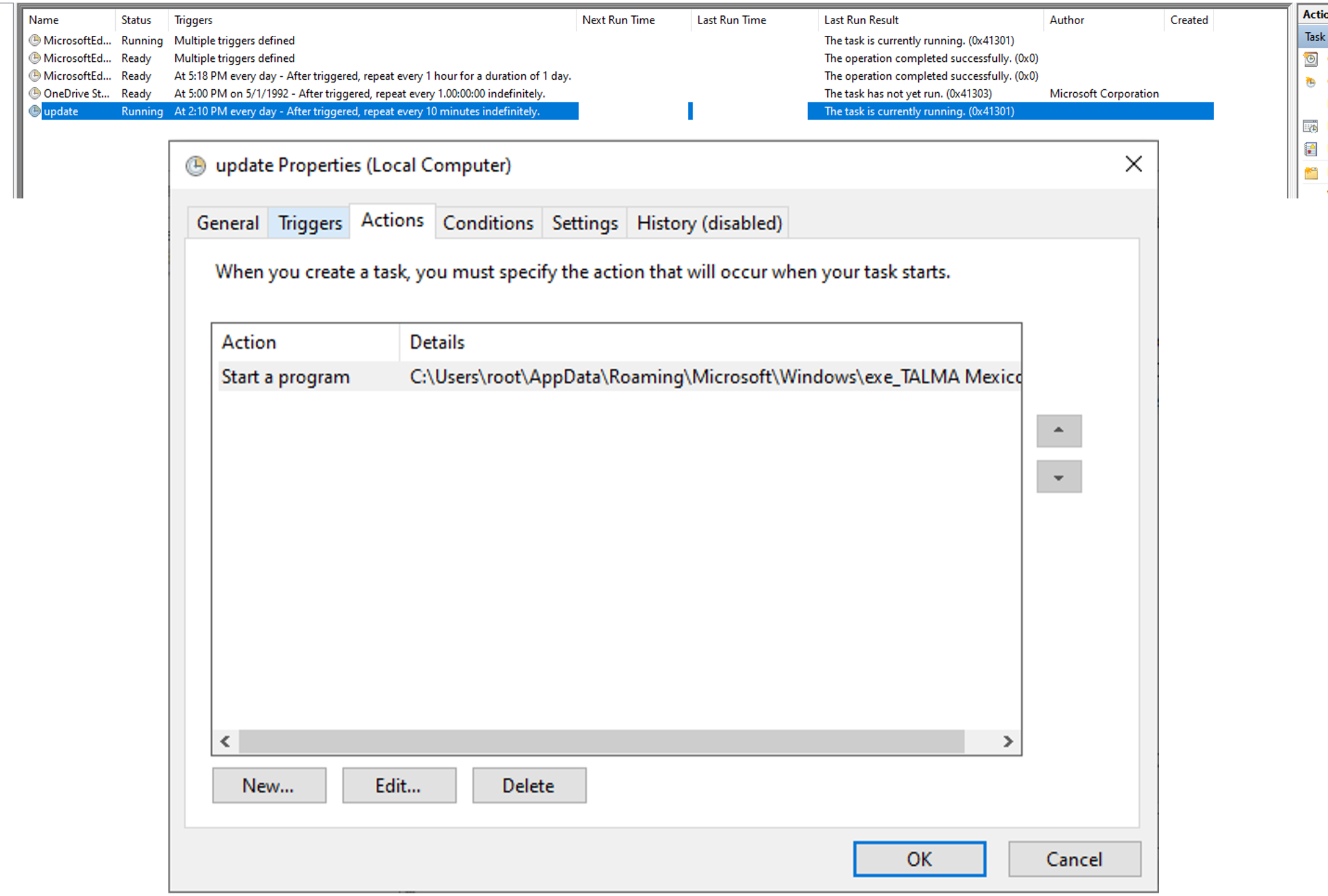
Avaddon uses the Windows Task Scheduler through a COM interface to create a task that executes Avaddon every 10 minutes located at the %APPDATA%/Roaming/Microsoft/Windows/ folder as shown in Figure 9.
Backup deletion
The malware tries to prevent the system from recovering from backups or from trying to repair itself automatically by executing the following list of commands:
Privilege escalation
This sample will always run as an elevated process as it uses a manifest file with the require Administrator directive set as:
However, the binary detects whether it is an elevated process or not. It also has a code to execute a UAC bypass using the COM component CMSTPLUA. In older versions of the operating system, it could bypass the UAC prompt under certain conditions, thus obtaining an elevated process without the user knowledge. In new versions of Windows, this bypass no longer works since the prompt will pop up to the end-user asking for authorization.
File encryption
The binary uses the built-in Windows Cryptographic API to encrypt files. Every file is encrypted with a unique AES key which will be appended to the file but encrypted with a public RSA key embedded in the binary. The AES key is created via CryptGenKey(cryptProvider, AES_256, 1, buff) API, then its exported via CryptExportkey() in PLAINTEXTBLOB format to finally encrypt it with CryptEncrypt(context, null, false, 0 m null, key, 0). The cyphered form of the key is appended to the file once the encryption is completed.
Every file is renamed with a unique extension for every victim (see Figure 10).
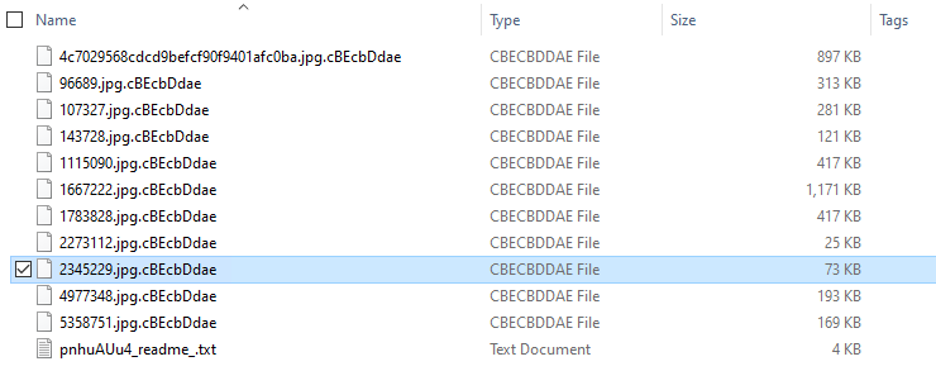
Ransom note
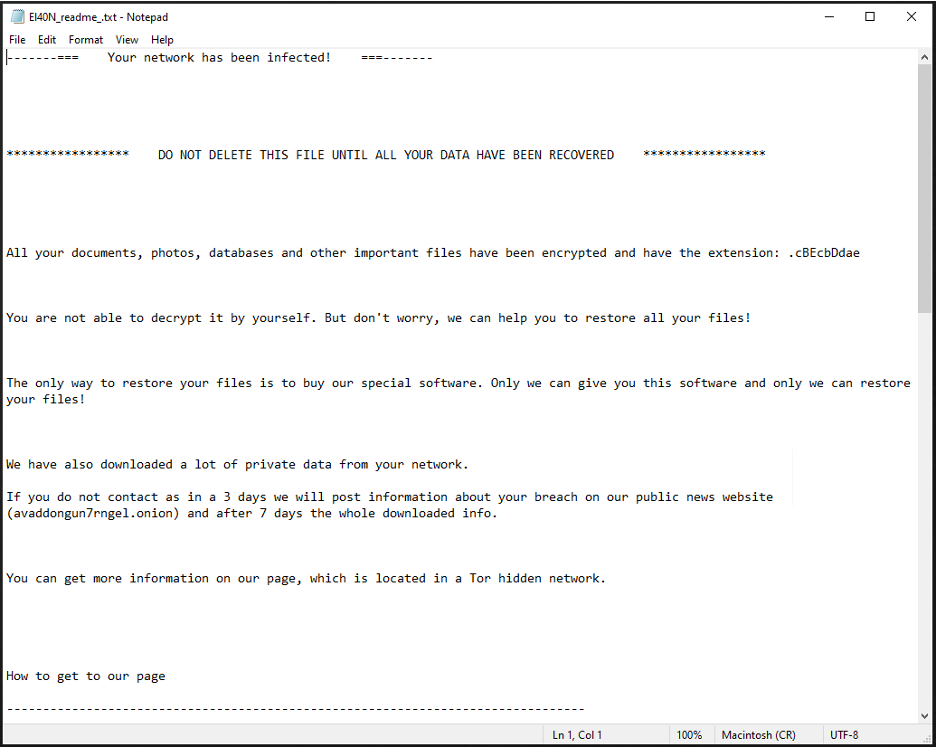
Avaddon leaves the user a note with instructions on how to recover the encrypted files as shown in Figure 11. This file name is randomly generated on every run: <random_str>_readme_.txt
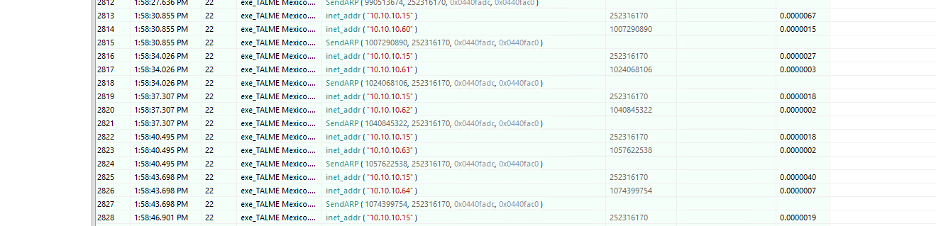
Searching for more victims
Avaddon will try to infect other hosts on the network, performing a scan to find available shared resources, as shown in Figure 12.
Post Infection
According to the ransom note, the malware encrypts files and exfiltrates the user information to force them to pay the ransom. Otherwise, their information would be leaked into their Deepweb forum, as in the case of TALMA.
Interacting with the Avaddon support team
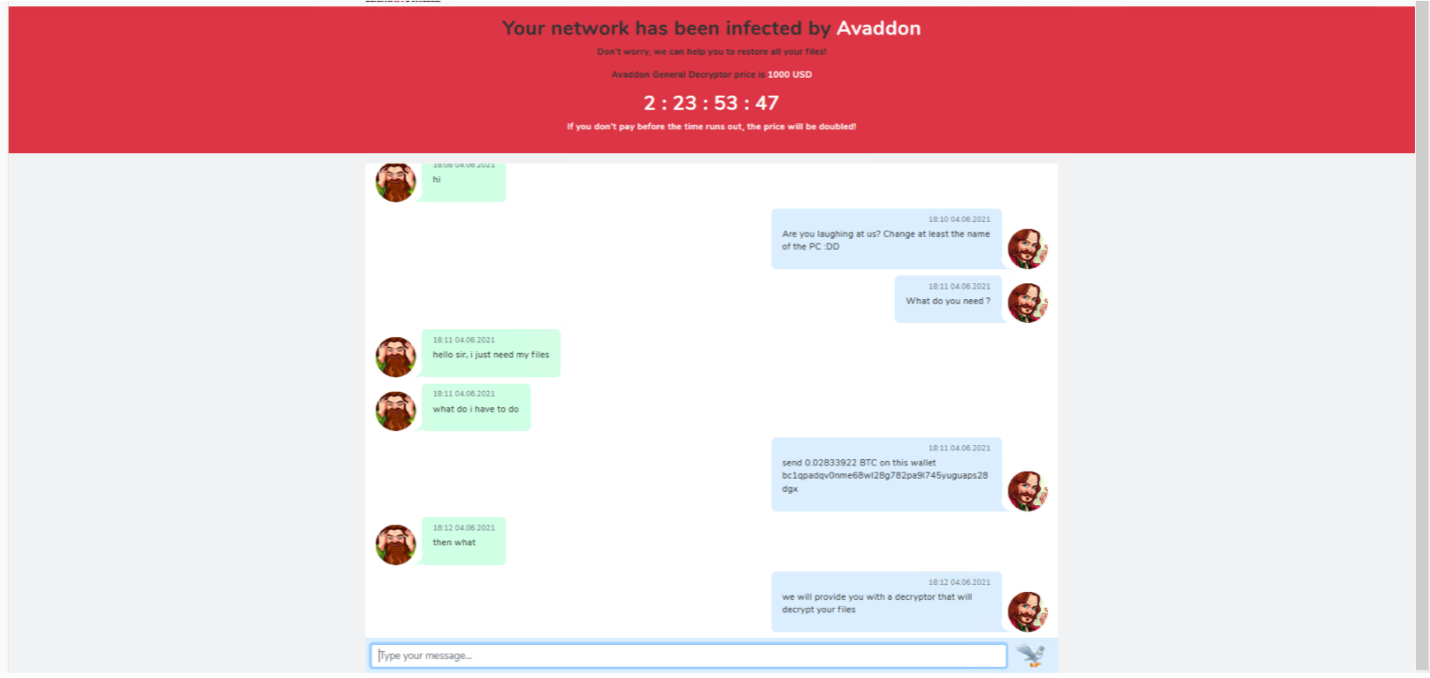
We reached out to the 24/7 support service from Avaddon to confirm the understanding of the post-infection process. Once you get infected, the ransom note will provide a unique key with a link to reach out to the group. In addition, they will validate the identity of the person talking to them. In our case, they found out we used a six-month-old version of Avaddon to talk to them and complained about it as seen in Figure 13.
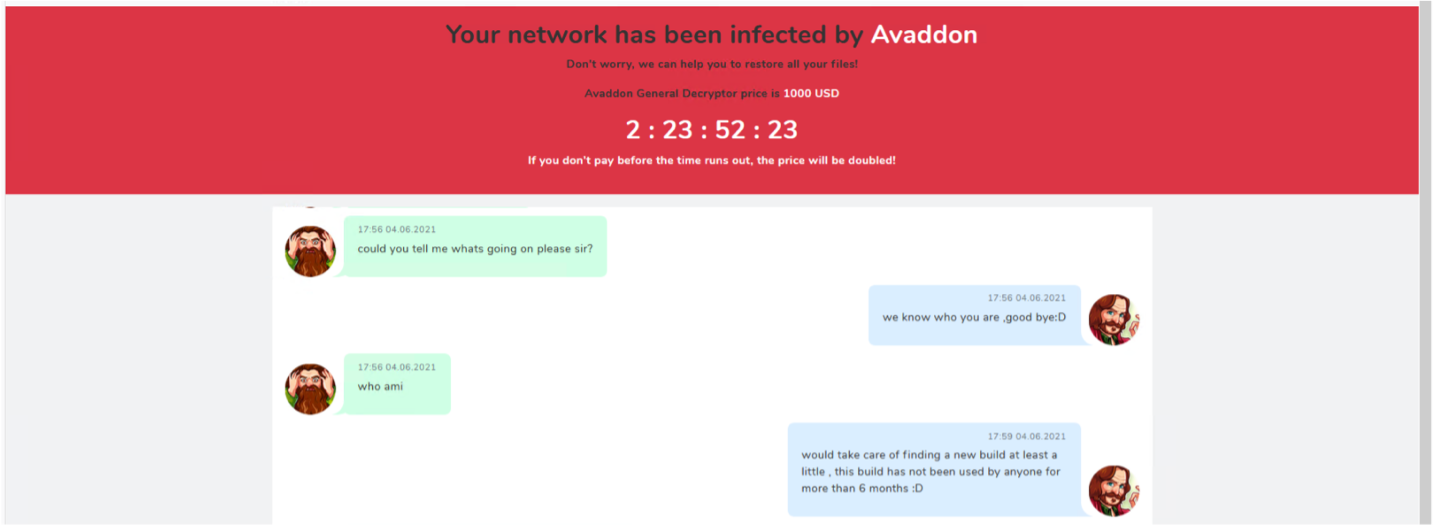
In our second chance of running the same old version, the strange behavior was detected once again. Still, this time they provided us with a valid btc wallet bc1qpadqv0nme68wl28g782pa9l745yuguaps28dgx to pay the ransom (see Figure 14). Since we were not an infected company and they were aware of it, it is possible that we were not talking to the real attackers.
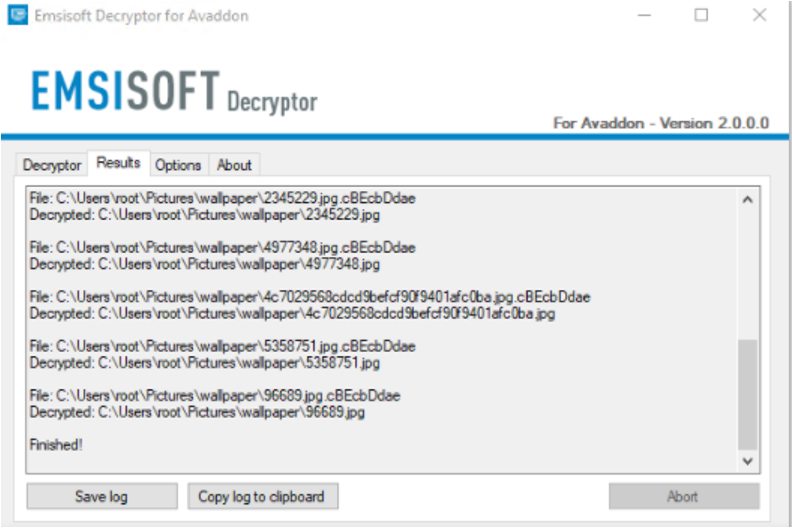
Decryption of files publicly available
On June 11, the threat actors announced that their operations would cease, and to show goodwill, they released a bundle with all the RSA private keys used in their campaigns to EMISOFT. A few hours after, EMISOFT released a decryption tool (see Figure 15), which allows victims to recover the files infected by Avadddon. This tool can be downloaded from https://www.emisoft.com/ransomware-decryption-tools/avaddon
Recommendations
Ransomware attacks have become the top method used by attackers worldwide to obtain large amounts of money in a short time. Ransomware payments have tripled from 2019 to date
In Latin America and Mexico, the cases continue to rise. On November 2019, the IT systems of PEMEX were compromised by ransomware; according to bleeping computer, attackers asked for the sum of $4.9 million USD. In 2021 alone, we’ve seen attacks on multiple Mexican institutions, including banks, with gigabytes of information leaked on the Deepweb, due to a possible lack of payment, along with the aforementioned attack on Loteria Nacional.
Why are ransomware attacks growing exponentially?
The ease of executing ransomware attacks through services known as Ransomware as a Service (RaaS) reduces entry barriers. RaaS allows non-technical people to hire a service that will enable them to compromise companies with minimal effort, sharing profits with the service creators
How can we combat this threat that is here to stay for years to come?
First, accept that your organization will be infected with ransomware sooner or later unless you proactively make changes. The initial step is to strengthen your processes, people, and technology by testing your systems against a ransomware attack. Metabase Q offers a different spin on Ransomware as a Service via its APT Simulation service. By replicating multiple ransomware families like WannaCry, Ryuk, REvil, DarkSide, Avaddon, etc., in your network, we can test how well your systems would respond. The benefits include:
This new service reverse engineers emerging threats such as ransomware to reproduce the malicious code. Unlike RaaS, Metabase Q has the control to execute the ransomware without the potential side effects of irreversible damage, such as deleting shadow copies or publishing sensitive information on the Deepweb. By utilizing the TTPs (Techniques, Tactics, and Procedures) and IOCs (Indicators of Compromise) used by malware in the real world, we can train and strengthen your processes, people, and technology.
We train your team to detect and fight real ransomware in your organization without having to pay millions of dollars for the ransom. Contact us at: contact@metabaseq.com
Appendix
Avaddon TTPS
- Infects Avaddon with Neshta
- Network scan with ARP
- Strings encrypted
- Highly obfuscated
- Encrypt files with AES
- Infect network resources
- Deletes backups via WMI
- Privilege Escalation
IOCs
Neshta TTPS
- Infects exe files
- Drops in temp directory
- Persistence through HKLM\SOFTWARE\Classes\exefile\shell\open\command
- Privilege Escalation
IOCs