
FiXS the new ATM Malware in LATAM
February, 27, 2023
7 minutes read
By Jesus Dominguez & Gerardo Corona from Ocelot Team
Context
ATMs are a core part of the financial system, providing users access to their money anytime at different physical locations. Over the past few years, attacks on these devices have increased in sophistication, severity, and frequency, resulting in significant consequences for both financial institutions and end users. According to recent reports, Mexico has experienced billions of dollars of losses annually due to ATM attacks, ranking second to Brazil. This problem only continues to worsen given (1) these devices’ proximity to cash and (2) the scope and range of attacks that they are vulnerable to, both physically and digitally.
At Metabase Q, we’ve been tracking and monitoring the rise of ATM malware that takes advantage of physical and digital components of the ATM. Ploutus, first discovered in 2013, is an instance of this type of malware which enabled criminals to extract cash from ATMs either by using an external keyboard or by SMS messaging. Over the years, Ploutus has since evolved to target different types of ATM XFS middleware. In early 2021, Metabase Q, reported about the return of Ploutus. This new variant specifically targeted ATMs produced by the Brazilian vendor, Itautec, and was prevelent across Latin America. For more information about this research, please visit here.
Metabase Q recently identified a new malware that is currently affecting Mexican banks. Due to it’s code name in the binary, we dubbed it FiXS.
It is not clear yet what the vector for the initial infection is. However, since FiXS utilizes an external keyboard (similar to Ploutus), we anticipate that it follows a similar methodology. In the case of Ploutus, a person with access to these teller machines physically connects an external keyboard to to the ATM for the attack to commence.
So far, we have identified some key relevant characteristics of FiXS malware:
- It instructs the ATM to dispense money 30 minutes after the last ATM reboot
- It is hidden inside another not-malicious-looking program
- It is vendor-agnostic targeting any ATM that supports CEN XFS
- It interacts with the crooks via external keyboard
- It waits for the Cassettes to be loaded to start dispensing
- It contains Russian metadata
This blog is released to share indicators to financial institutions to protect accordingly.
Malware Dropper Analysis
Name: conhost.exe (Borland Delphi) – Size: 145 KB
Architecture: Intel 32 bits
MD5 : 8e41f365cde91e8f74d6d7ea1cdbd1d9
First Submission: 2023-02-11 04:26:43 UTC
The ATM Malware comes embedded in a dropper which immediately caught our eyes when we identified XFS related strings like:

Normally this DLL MSXFS.dll comes with the necessary XFS APIs to control the Dispenser.
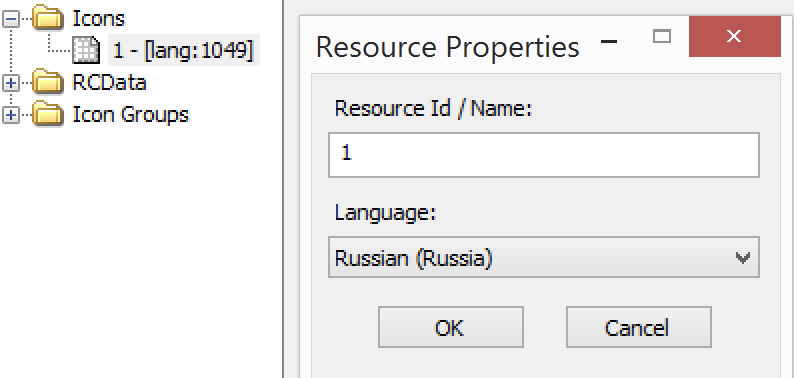
Interestingly, the source locale/language reflected in the resources is Russian (LCID=1049), which suggest the origin of this piece of malware:
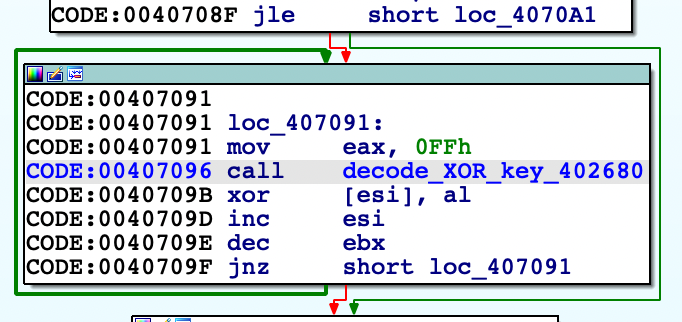
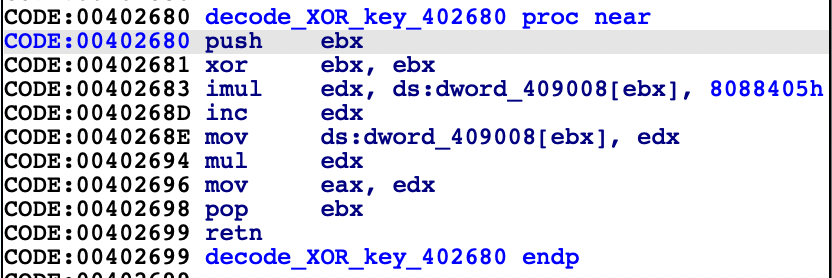
The embedded malware is decoded with XOR instruction where the key is changed in every loop via decode_XOR_key() function:
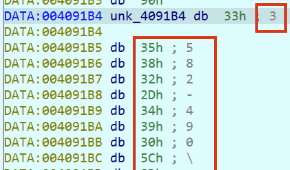
The encoded binary is stored in the appended data section (overlay) with a size of: 107008 bytes (105 KB), which is the size of FiXS. In the image below the first two bytes decoded are shown:
Then dropper identifies the system temporary directory to store the embedded one within a folder with the hardcoded name: “3582-490”, and sets the name equal to the dropper one as conhost.exe:
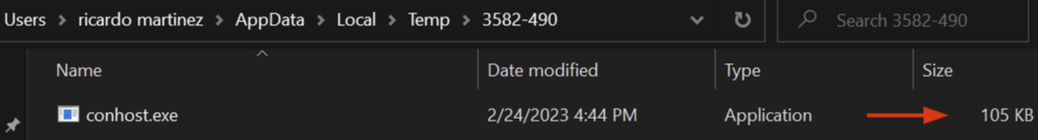
Finally, FiXS ATM Malware is launched via “ShellExecute” Windows API.
Criminal Interaction with FiXS
Name: conhost.exe (C Microsoft Visual C/C++(2012 update 2) – Size: 105Kb
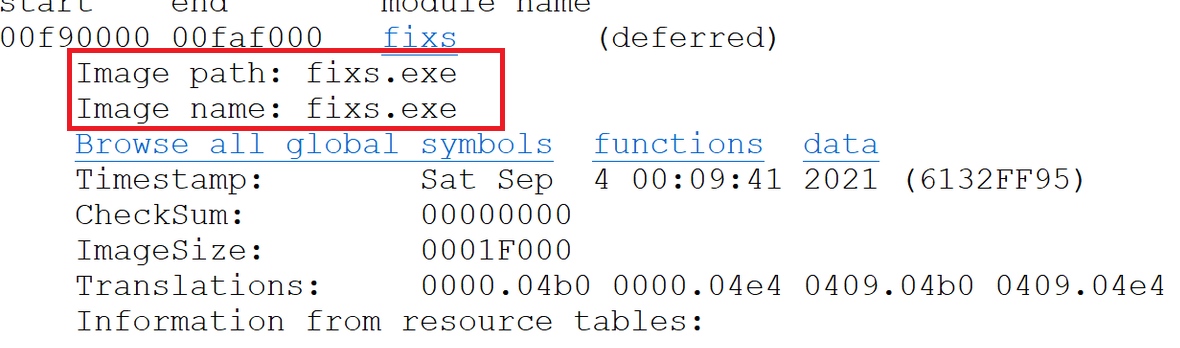
Code name: FiXS.exe
Architecture: Intel 32 bits
MD5 : 8c9f2298275fd486a40b8811436a3a04
First Submission: 2023-02-11 04:29:32 UTC
As mentioned before the original name of the binary was FiXS.exe.
FiXS is implemented with the CEN XFS APIs which helps to run mostly on every Windows-based ATM with little adjustments, similar to other malwares like Ripper. The way FiXS interacts with the criminal is via external keyboard, similar to other viruses, this can be confirmed by identifying the hooking mechanisms intercepting the keystrokes:
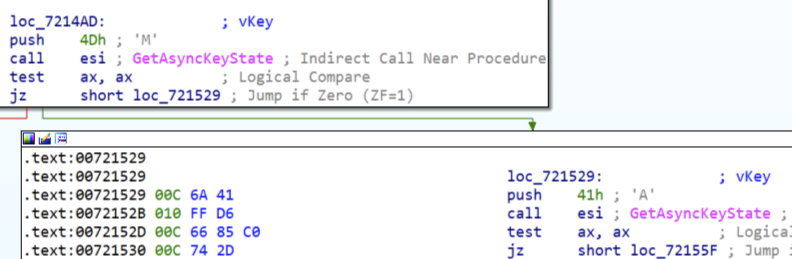
The malware runs in a infinite loop reading the keyboard and waiting to find the right combination to display
M - Show or Hide the Window A - Get Cash units info C - Close session with Dispenser and kills the process B - Dispense money J - Not validated P - Not validated
By pressing the letter ‘M’ to show the malware interface and then, pressing the letter ‘A,’ we can see the face of FiXS in the next figure:

In this case, it does not come with a rich interface like Ploutos or Padpin where different information is displayed and even an activation key is required, in this case it only displays the numbers of bills as follows::
- Data 3-6: Number of bills in each cassette
- Data 1: Number of bills in the recycle bin
- Data 2: Number of bills in rejected bin
Dispensing money
One critical note: given the malware implements a generic way of supporting any time of dispenser, it is vendor agnostic. This is done by interacting in the registry key to list the logical name of the dispenser without picking a particular one:
It tries to open the registry key SOFTWARE\XFS\PHYSICAL_SERVICES to iterate with all physical services:
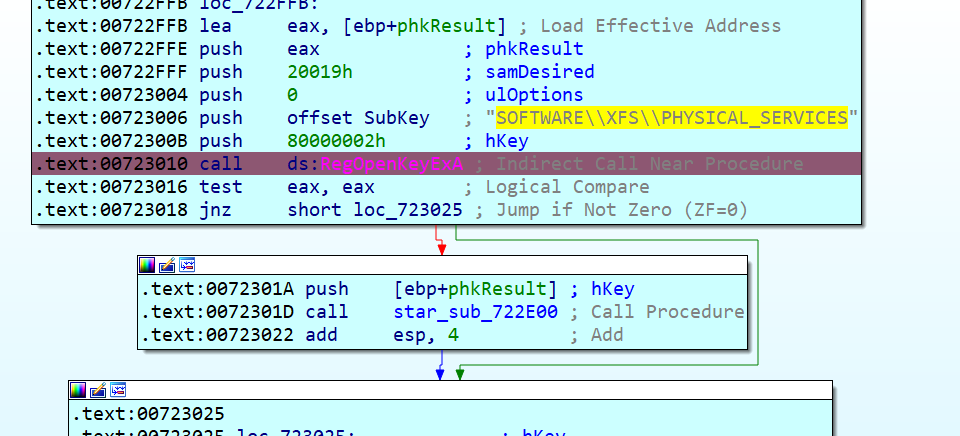
Every service identified is checked to make sure it is the Dispenser by calling the WFSGetInfo API with command ID equal to 303 (WFS_INF_CDM_CASH_UNIT_INFO):
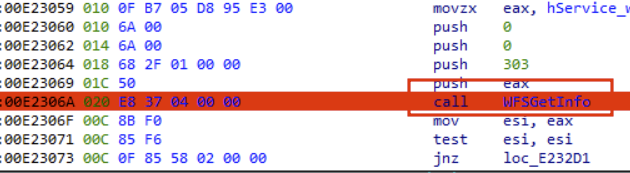
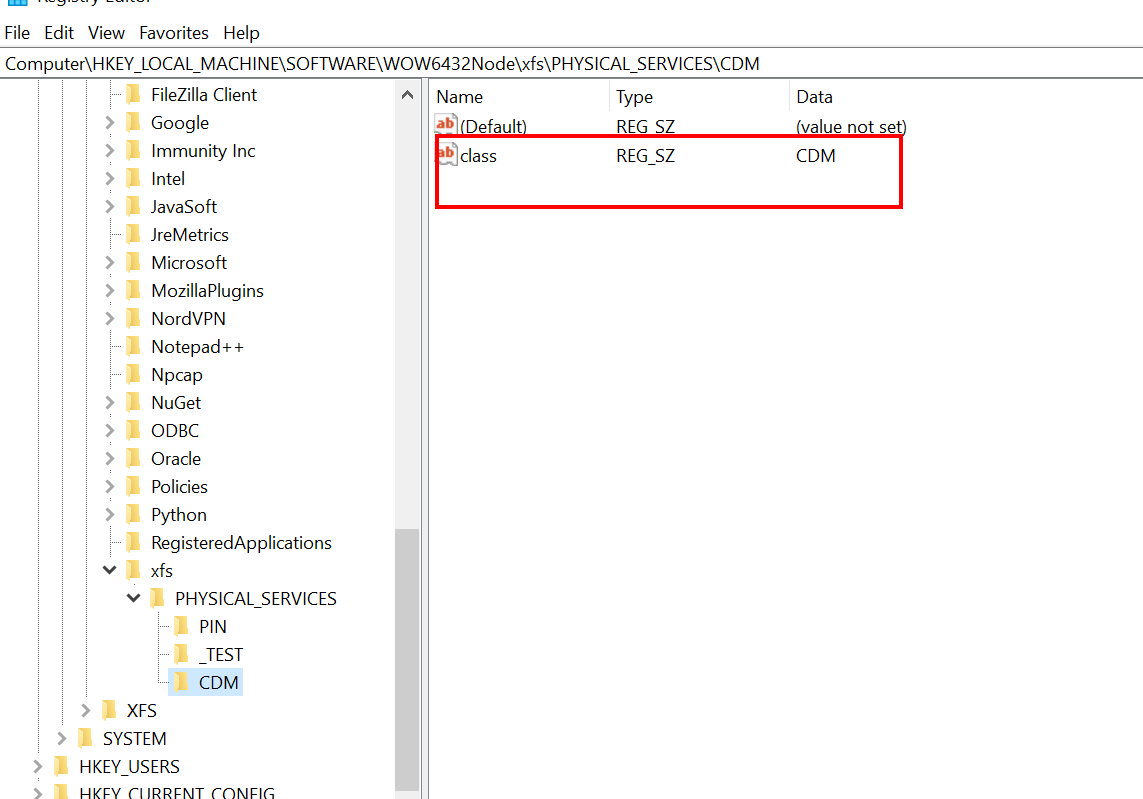
If an error is received, it goes to the next peripheral in the list, in our lab, the Dispenser name is “CDM” which allows the malware to continue:
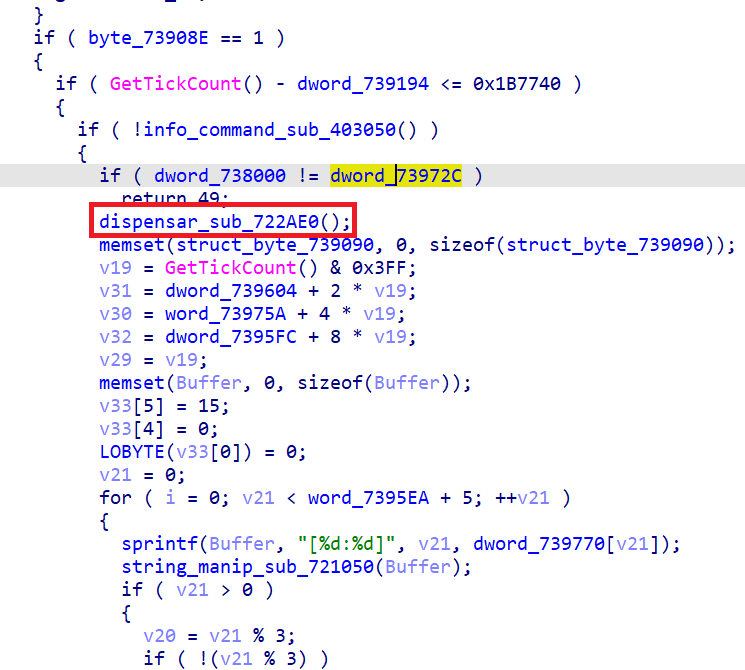
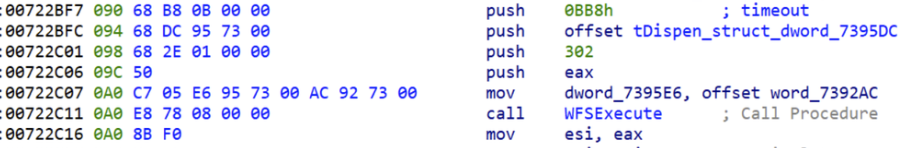
As described before, once the “B” key is received, and if the ATM has been up for less than 30 minutes, it will proceed to dispense money. This means that whoever restarted the ATM last time, and probably the one who installed the malware ( a maintenance engineer, a consultant, etc), the mule will arrive soon after.
In the next figure, the 30 minutes validation can be seen via GetTickCount API, and then the Dispenser is commanded to spit out money via command id 302 equal to WFS_CMD_CDM_DISPENSE:

Conclusions
Given the importance of ATMs in the financial system chain for cash-based economies, malware attacks are far from over. It is critical for banks and financial institutions to assume potential compromises of devices and focus on reducing the Time to Detect and Response to these types of threats.
At Metabase Q, we support customers across their cybersecurity journey. We utilize our APT Simulation service to test customers’ environments against these types of attacks – testing ATMs across hardware, middlewarwe, software, network, and memory to monitor, detect, and respond according. Please reach out to use if you’d like more information on this service.
We also offer frequent training on this subject to promote better ATM cybersecurity practices in Mexico City. In addition, we will be hosting a training session at BlackHat 2023 in Las Vegas. More information on the training and how to register can be found here.
IOCs found
Hashes:
8e41f365cde91e8f74d6d7ea1cdbd1d9
8c9f2298275fd486a40b8811436a3a04
Filenames:
conhost.exe
FiXS.exe



