
How does ALPHV operate the RaaS membership program?
December, 5, 2022
14 minutes read
By Ramses Vazquez & Miguel Gonzalez from Metabase Q’s Ocelot Team
Context
DARKSIDE/BLACKMATTER/ALPHV-BLACKCAT
The ALPHV Ransomware group also known as BlackCat has positioned itself in the Top 5 of most active ransomware groups. Among the target industries of this group are construction, energy, financial, logistics, manufacturing, pharmaceuticals, retail, and technology. The scheme under which this ransomware operates is through Ransomware-as-a-Service (RaaS). However, they are not focused on random attacks, or spam campaigns (without a specific goal), all their attacks are focused to predefined targets through partners, who join forces to carry out attacks on previously profiled victims, which explains why the building of malware pieces (made in RUST) and infection methodology are specific to each case.
Throughout this profiling you will be able to know more valuable information about this group.
Some context before diving into this research. ALPHV is not a group of amateurs, they are a group of criminals who has been evolving and learning from mistakes made in the past. They started as DarkSide, and due to the persecution, hunting and shutdown of part of their infrastructure by US intelligence units, they had to retire and regroup, changing their name and eventually returning to the criminal scene as BlackMatter, a group that lasted only a few months, until the collaboration of the US and Russia forced them to shut down again.
Even though they had changed their name, the US government agencies hunting and the connection of BlackMatter with critical infrastructure attacks, made them fear a potential retaliation and therefore, they announced the dismantling of the group, without giving further explanation. Soon after, profiles began to emerge in private Russian forums, where specialists were recruiting for a “pentesting project”, this was the first sign of life of ALPHV-BLACKCAT.
Below is the timeline of ALPHV-Blackcat evolution:
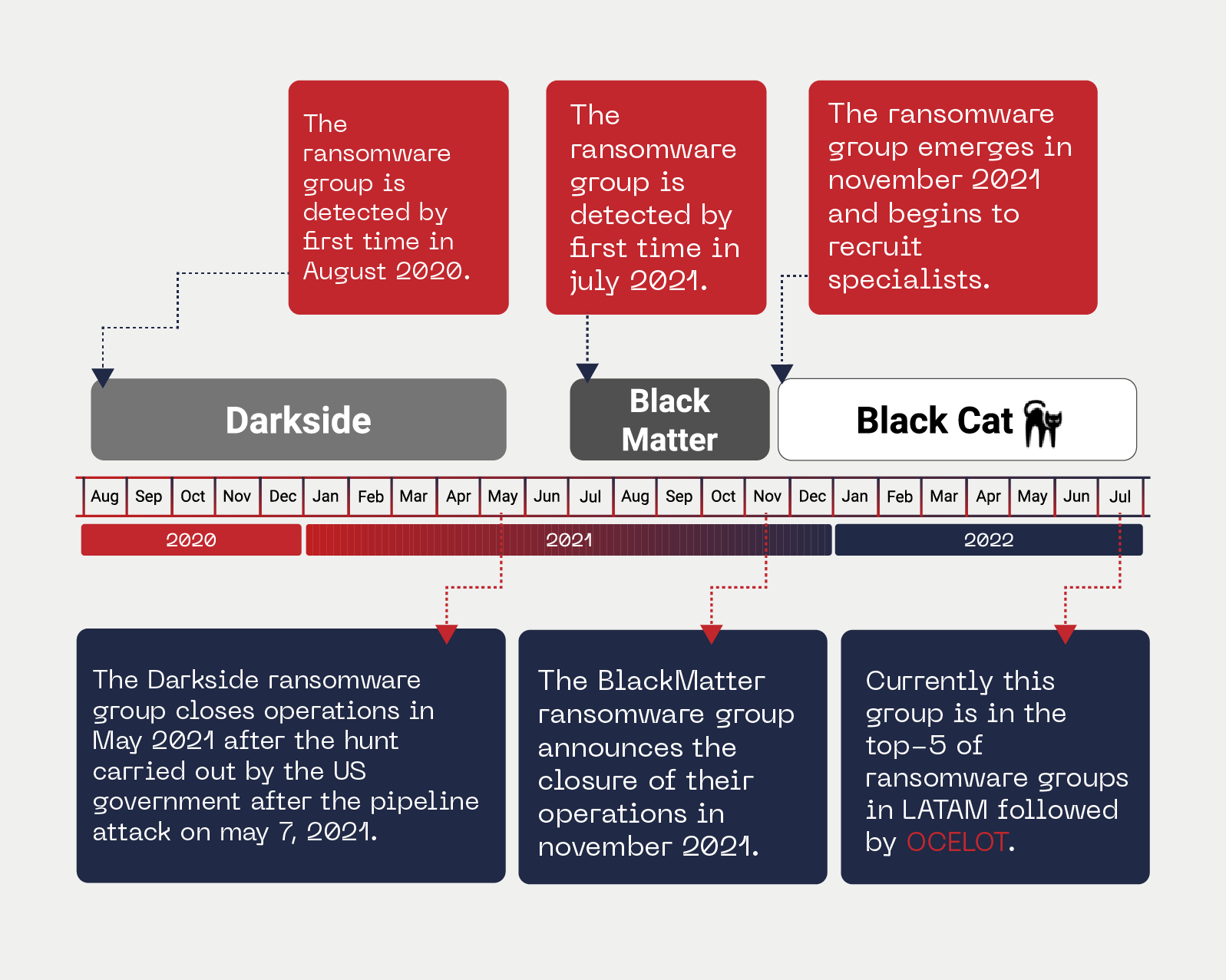
In the picture above, we can see that Darkside never disappeared, it only worked on rebranding and updating to continue operating, strengthening in each new revival.
ALPHV-BLACKCAT is another ransomware group now that uses triple extortion.
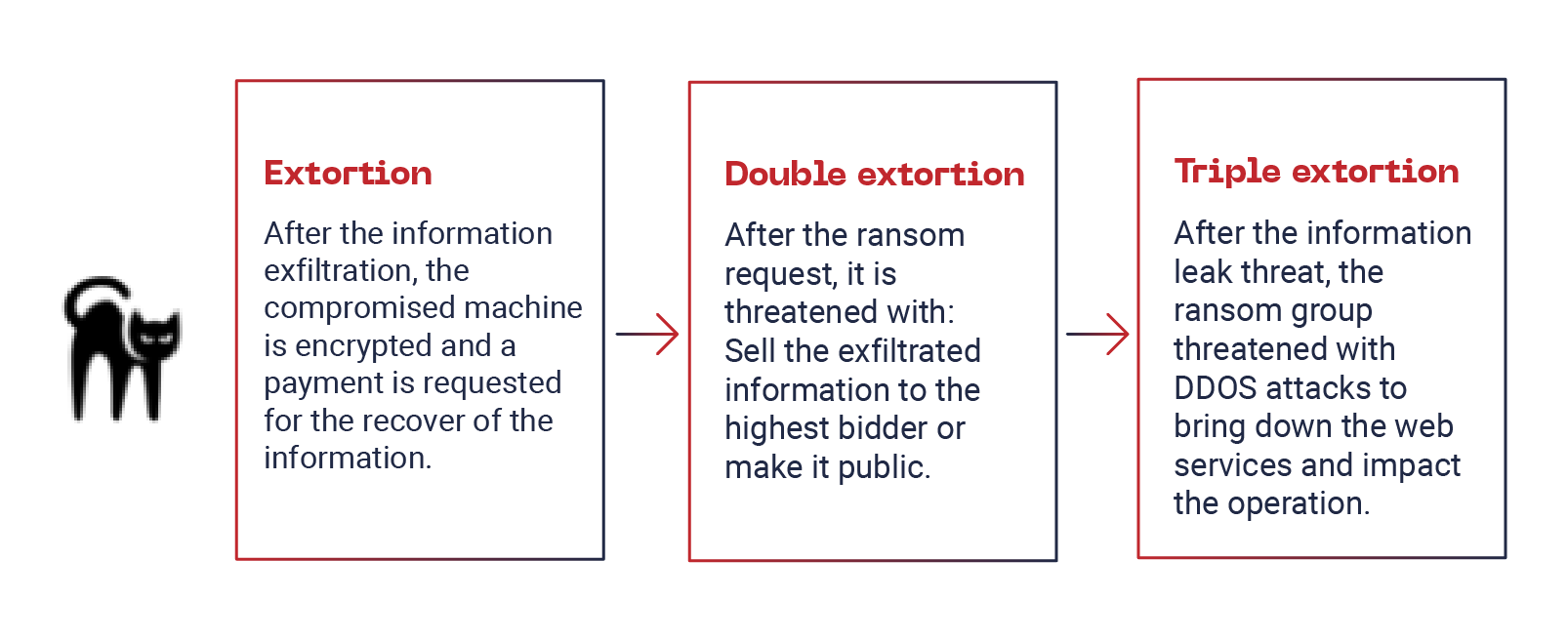
At the end of 2021, ALPHV-BLACKCAT began to make publications in different Russian private forums, where its objective was to recruit specialists in penetration testing.
*******************************************************************************************
Нужны опытные пентестеры, такого уровня вы еще не видели, чтобы узнать все подробности пишите по контакту ниже.
—————————————————————————————————————————————————-
We need experienced pentesters, you have not yet seen such a level, to know all the details, write to the contact below:
*******************************************************************************************
These recruitment posts were made in private (closed) forums, seeking to recruit specialists and experts in different areas, however, one type of profiles was highly demanded by cybercriminals: profiles of RUST programmers.

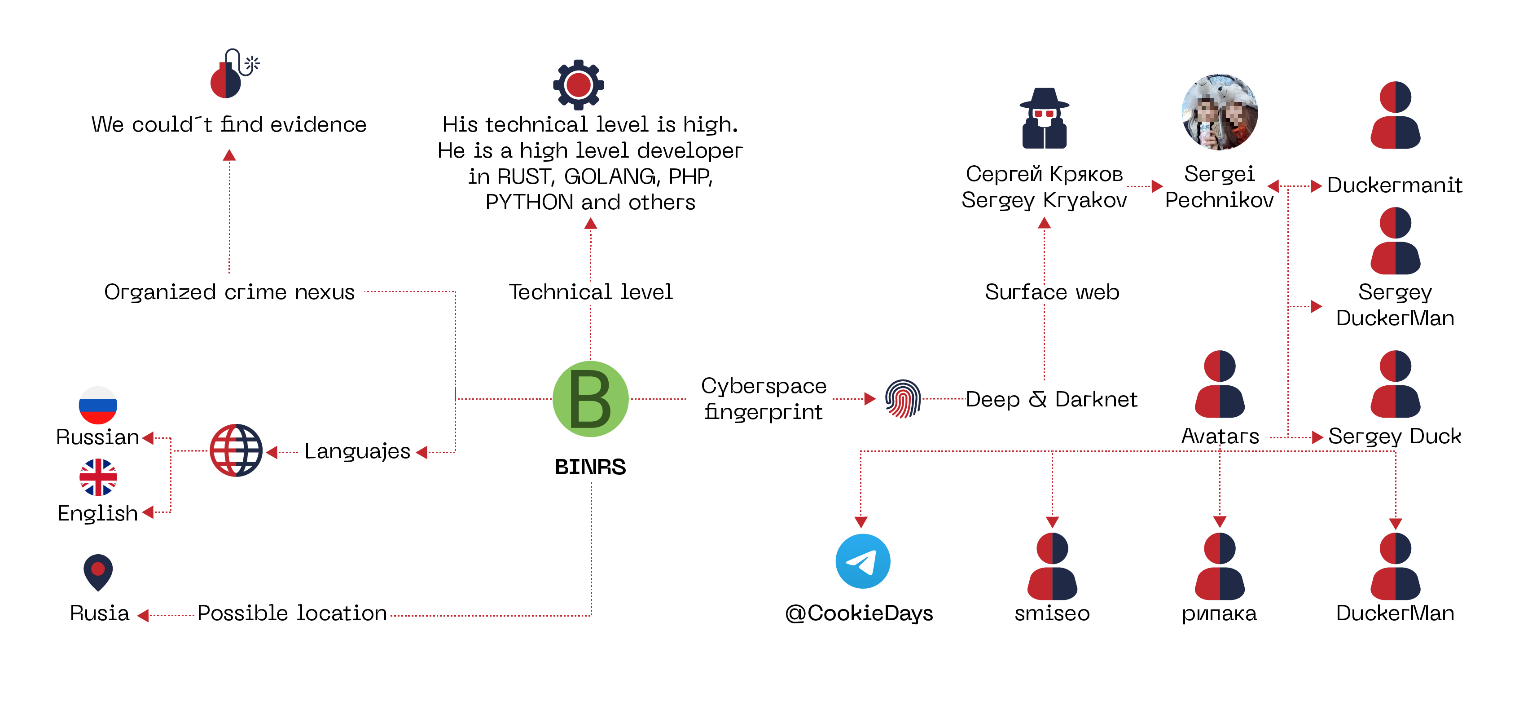
One of his biggest acquisitions was a specialist with different aliases, including BINRS.

BINRS is a Russian specialist in programming languages: RUST, nodejs, php, golang. Currently, this specialist has already closed all his accounts/avatars in forums and markets. His method of contact was by Telegram or TOX chats.

Making a brief parenthesis, the BINRS entity was exposed, mentioning some of its avatars in underground forums as well as its presumed departure from ALPHV. Mapping this information, we can have the following profiling:
BlackCat Partner Program
In their RaaS scheme, different benefits are offered, such as a dynamic rate, in which depending on the amount obtained by the payment of the ransom, the partner can obtain from 80% to 90% of the total, starting from 1.5 million dollars and up to 3 million dollars.
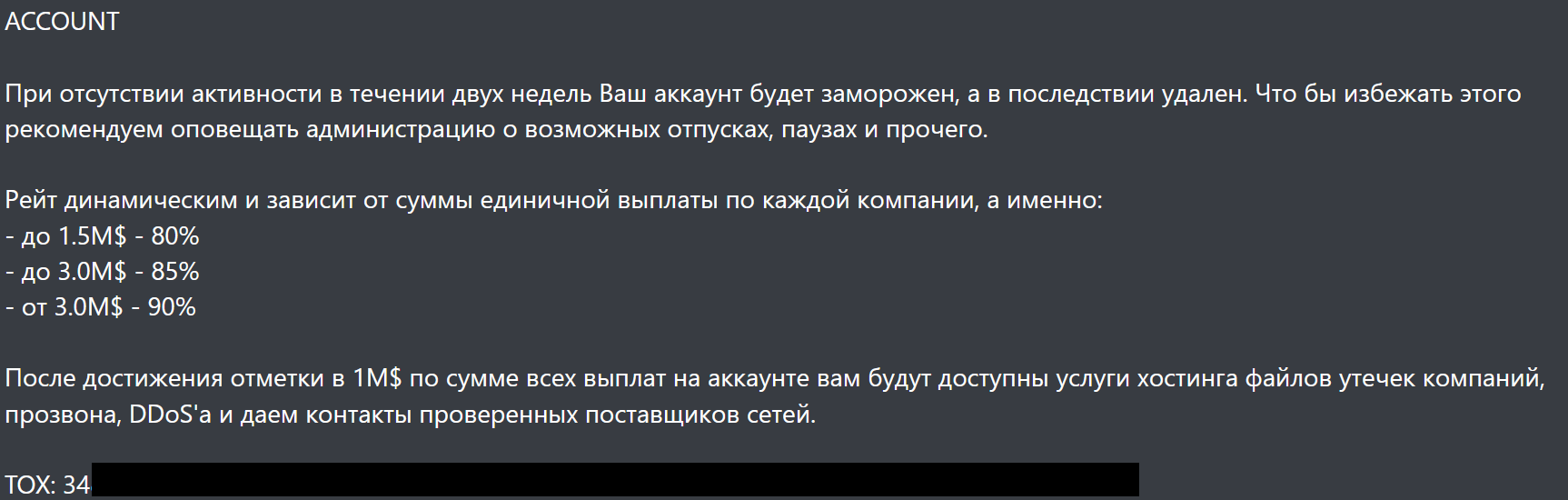

After reaching the $1 million mark for the ransom payment income, access to the hosting server of the data leaks is provided, DDoS and verified network provider contacts services is allegedly offered.
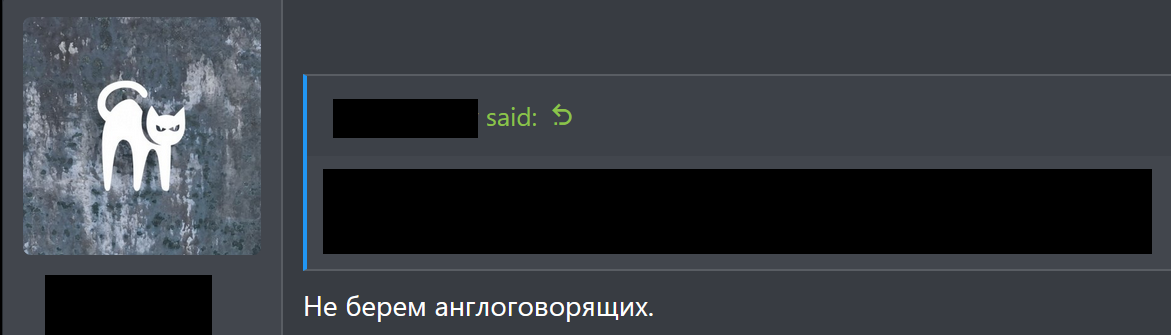
Although the moderators handle the Russian and English languages, they are unfriendly with the English speakers, mentioning that they are not accepted in the system.

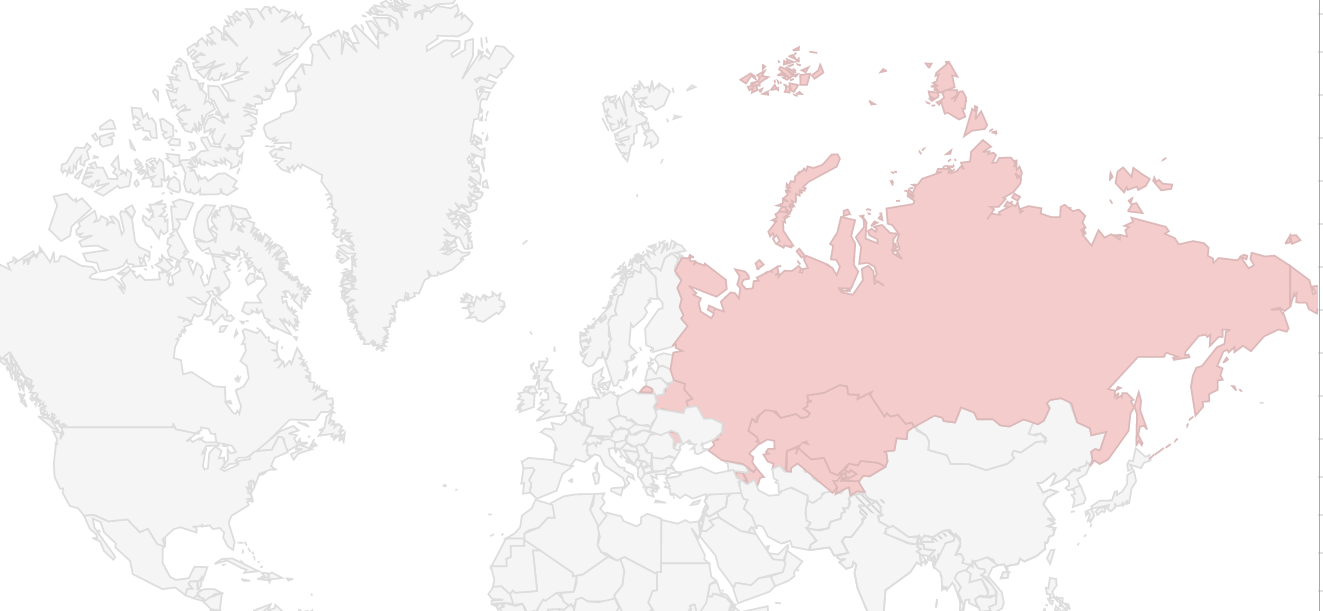
There are not targeted companies, as they impact from different sectors. However, after the stumble of the attack on the US oil Colonial Pipeline, it is forbidden for any associate to attack healthcare entities, non-profit entities and systems in their supply chain and critical infrastructure. As for geographical delimitation, it is forbidden for ALPHV-BLACKCAT partners to attack any country in the CIS (Commonwealth of Independent States) and countries neighboring Russia, including European ones.
CIS: Armenia, Azerbaijan, Belarus, Kazakhstan, Kyrgyzstan, Moldova, Russia, Tajikistan, Uzbekistan.
Even those who are no longer part of the CIS. Such is the case of an associate who attacked a company in Turkmenistan and retaliation actions were taken.
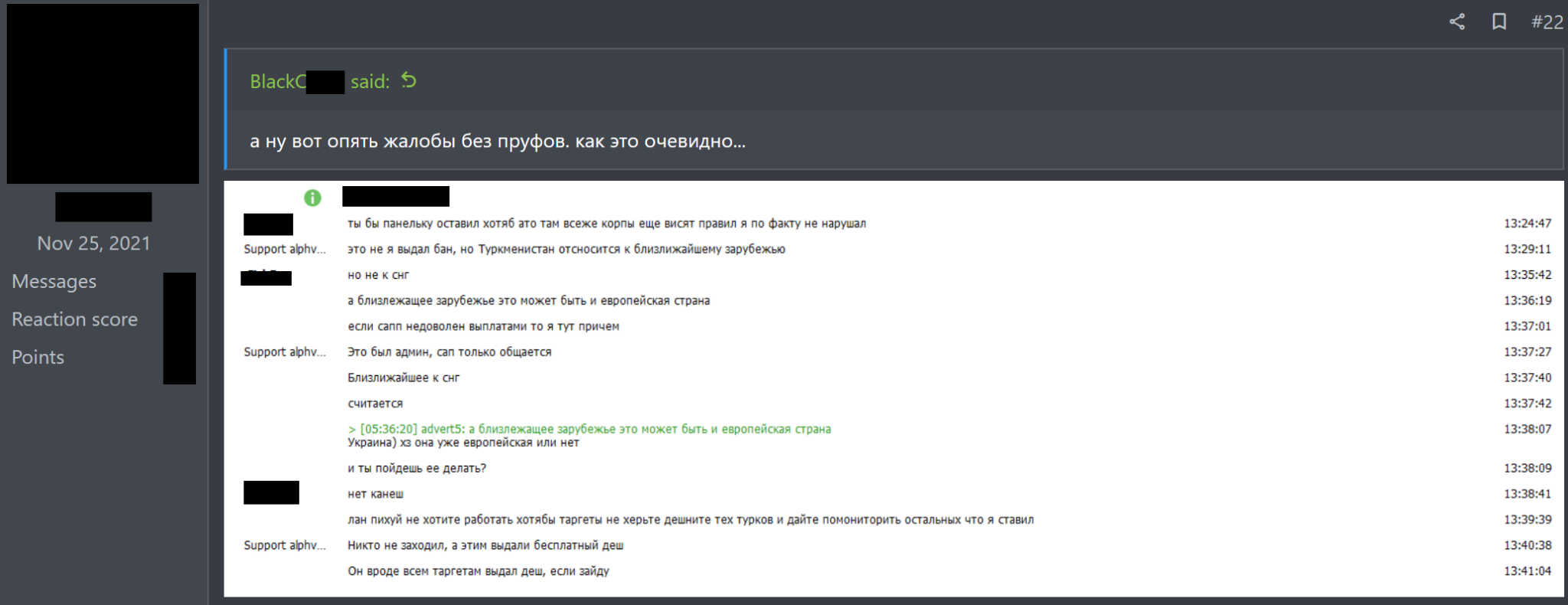
This is part of the confrontation translated to English:
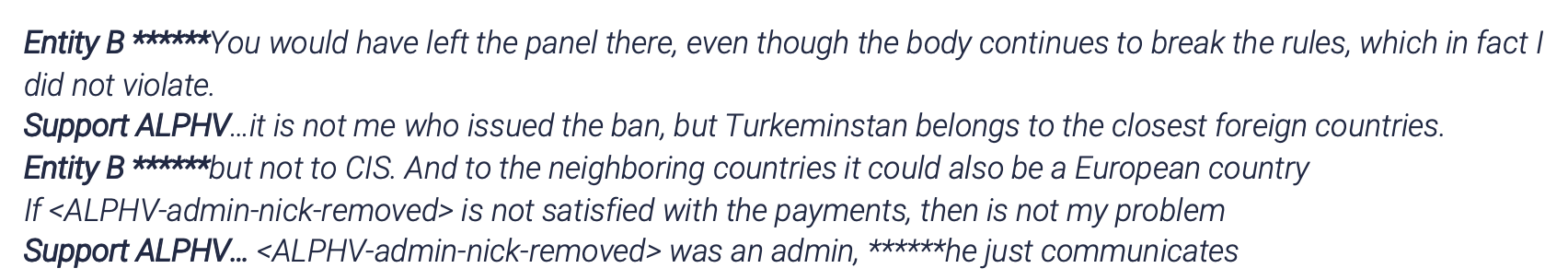
To conclude this part, their RUST-based ransomware adds a verification to avoid being executed on computers within the geofence, that we’ll review later.
About the motivations and impact in LATAM
Because they have been kept on the Darknet and in closed forums, we can assume that their motivations are merely economic.

This group has impacted LATAM, affecting 12 Mexican companies in April 2022, and another 4 companies in May. The affected companies were from the states of Guanajuato, Mexico City, Chihuahua, Nuevo León, Jalisco, and the State of Mexico.
Their last Mexican victim, a Mexican open television network, was recently attacked, on May 24, 2022, having their data exfiltrated.

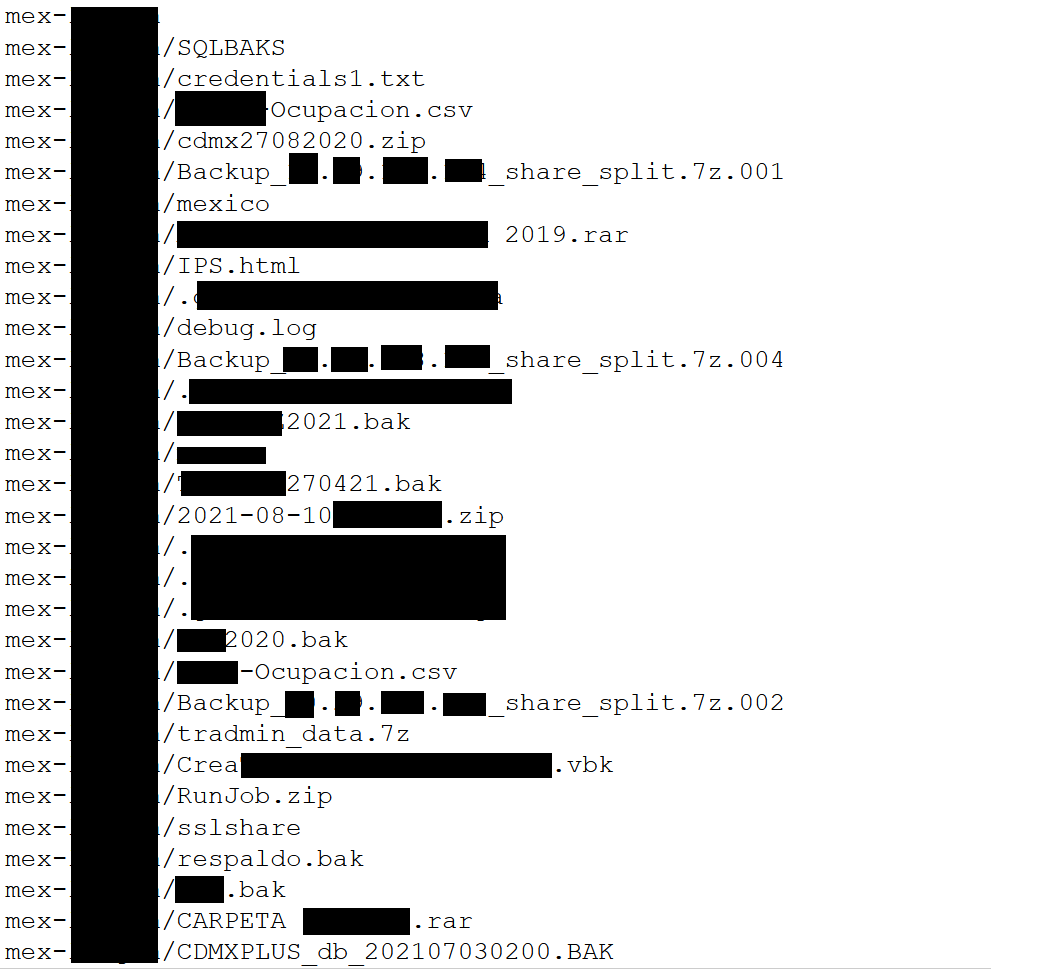
However, the content was modified on June 15, 2022. As it is no longer exposed, it is possible that the ransom was paid.
Highlights Ransomware BlackCat
- BlackCat Ransomware is developed in RUST.
- Ransomware encryption is based on AES.
- The BOX (RUST Programming Libraries) has creation date on November 2021; however, each sample seems to be customized for every campaign.
- The ALPHV-BLACKCAT Ransomware group leverages previously compromised user credentials (with some stealer) to gain initial access to the victim system.
- The ALPHV-BLACKCAT Ransomware group also performs targeted attacks via spear phishing.
- Once the malware establishes access, it compromises the Active Directory user and administrator accounts.
- The malware uses Windows Task Scheduler to configure malicious Group Policy (GPO) for persistence.
- The initial implementation of the malware leverages PowerShell scripts along with Cobalt Strike and disables security features within the victim’s network.
- BlackCat Ransomware also leverages Windows administrative tools and Microsoft Sysinternals during the compromise.
- ALPHV-BLACKCAT steals the data of the victims before the execution of the ransomware. They have a tool to carry out the exfiltration, that is called: ExMatter, which as its name suggests belongs to the BlackMatter Ransomware group.
BlackCat Malware Analysis
Through open sources, executable files belonging to the ALPHV group have been identified. This group has been infecting companies with its BlackCat Ransomware, encrypting their files, with the intention of extorting the affected companies by requesting payment for the “ransom” of their information. This time, the ransomware was identified in the month of June 2022 by the Ocelot Threat Intelligence team, which contains an executable file that has been present within the region infecting companies. Additionally, more campaigns in the region of this type, reported in the last quarter of the year, were identified using a variant of BlackCat, whose purpose is to obtain access and control of the infected computer, stealing sensitive information such as user credentials, logs, among others.
Key Points
- This campaign is active in LATAM.
- It was identified that the executable encrypts system files through thread creation, privilege escalation, deletion of shadow volumes, deletion of configuration processes, and removal of services.
- The malware used corresponds to BlackCat, which comes from the criminal group called “ALPHV”.
Malware Properties
File Name: w0kapn5k0.dll
SHA-256: 1048a41107f4d9a68c1f5fc0b99ac75dc198047f18bb6e50f3d462f262b8f6cd
MD5: 93f34fb60a180a3a80ca758b97c2e551
Type: Dynamic Link Library (.dll)
Rating: Ransomware
Binary properties
- Architecture: x86
- Compiler: MinGW
- Language: RUST
RUST Evidence
By inspecting the binary, it is possible to find evidence indicating that it was built with the RUST programming language.
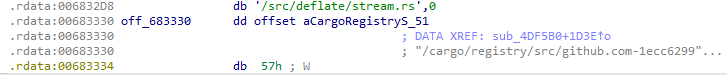
We can also find references of the RUST compiler:

We can also find the symbols in the source code:
Command-line interface
Interestingly, the malware won’t run unless it receives specific arguments:
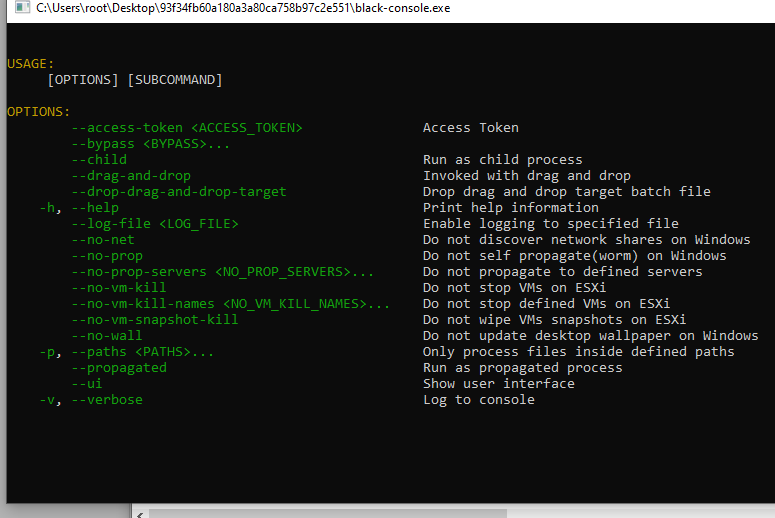
Algunos parámetros importantes:
- –access–token: key parameter for ransomware execution.
- –log-file: Name of file to execution log is saved.
- –no-net: Skip network shares discoveries.
- –no-prop: Prevents spread within the network.
- –ui: Displays a user interface.
- –verbose: Detail of each action performed within the system.
Execution flow
In order to execute the malware, it is necessary to provide an existing value for the “–access-token” parameter, otherwise it will not perform any action within the system. However, variants of the malware have been found that runs even if this value is not valid.
Thanks to the malware log, it is possible to determine the flow of the actions it performs within the system. The next image shows part of the log:
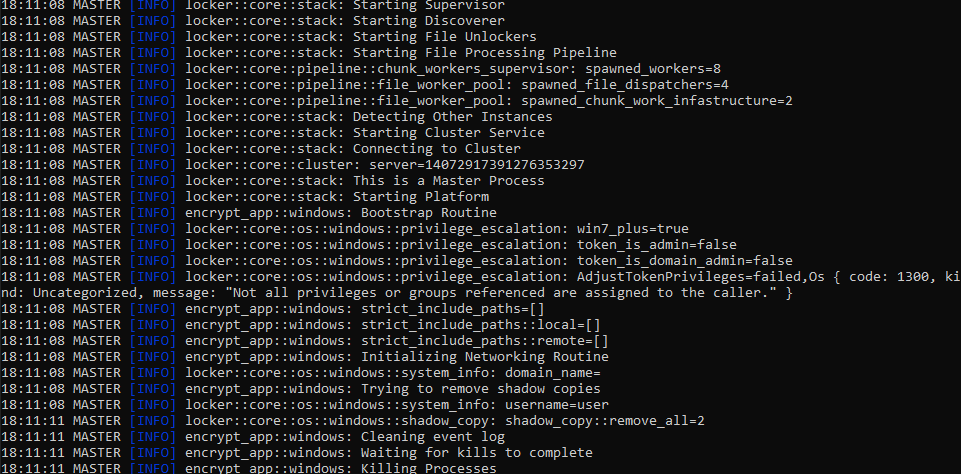
The malware executes the following actions within the operating system:
- Create threads for file encryption in parallel
- Detects if there are other instances of the program to avoid running twice
- Determine user privileges
- If no administrator privileges, it tries to escalate with UAC bypass
- Delete shadow volumes
- Delete services
- Starts the file encryption process
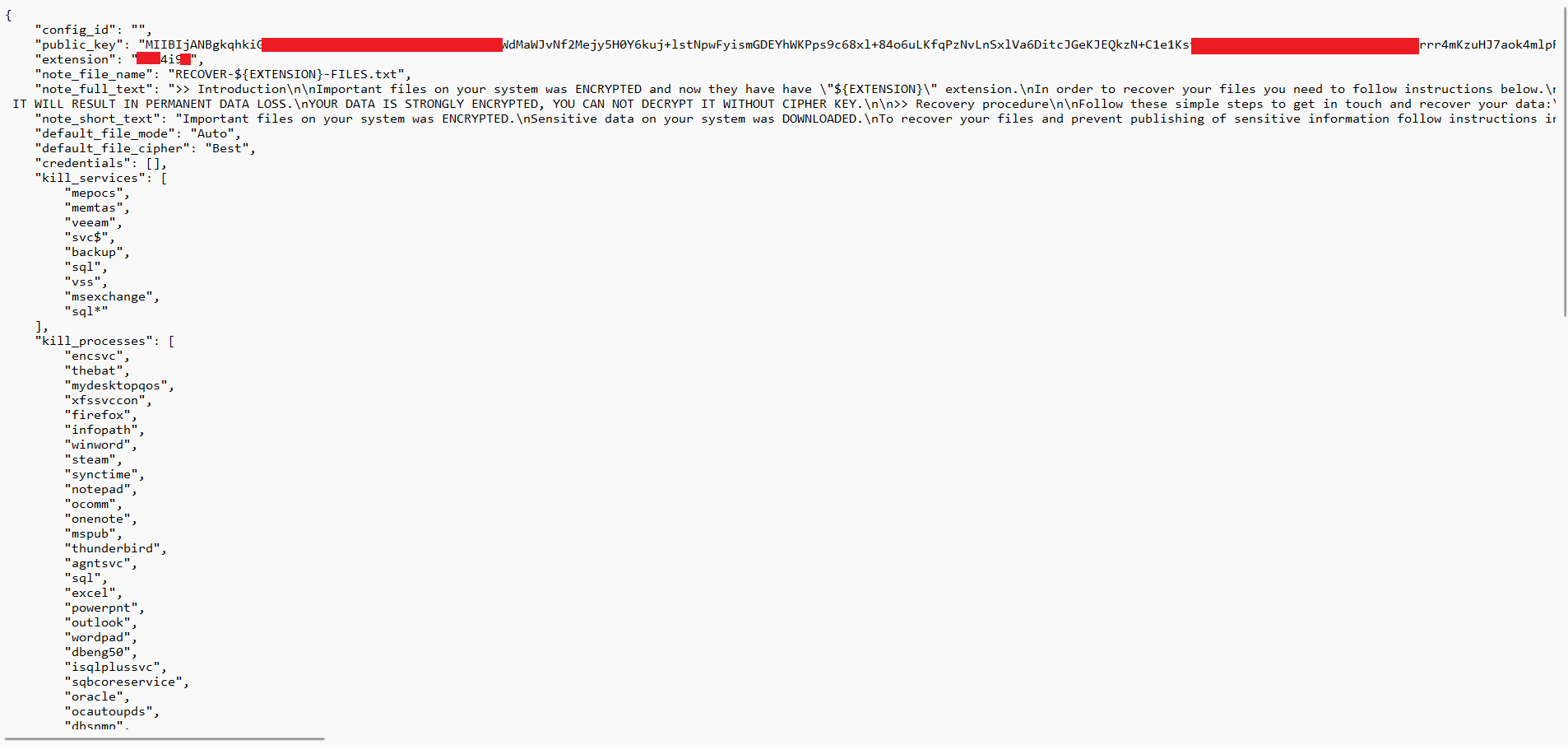
Configuration File
The configuration file of the ransomware was found embedded in the binary. In this configuration we can find the public key, the extension of the encrypted files, the ransom note, the services that must be deleted, the processes running, the directories and files to exclude and some other parameters for lateral movement purposes.
File encryption
Once the encryption process is done, we can verify that the files have been modified and an extension has been added that corresponds to the one found in the configuration file.

The desktop background is replaced:
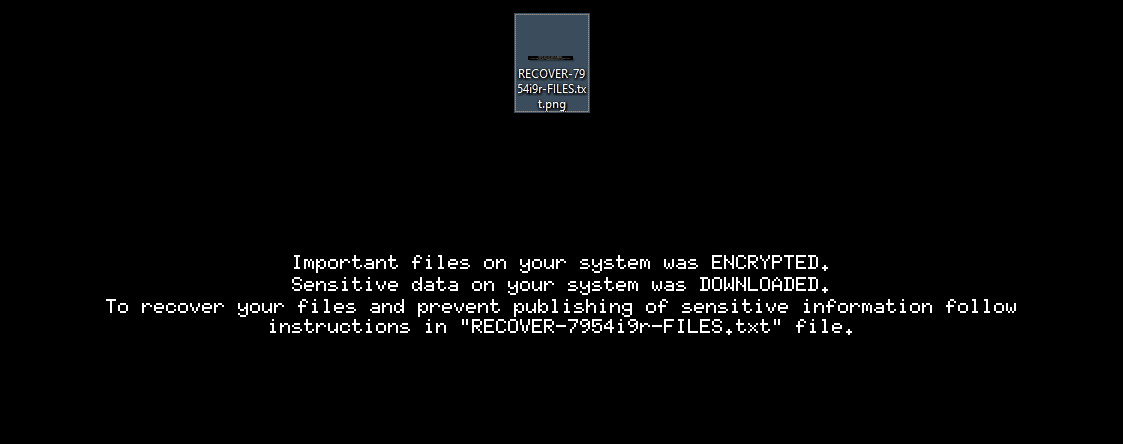
In each directory where a file encryption is performed, a ransom note can be found, as we can see in the next image:
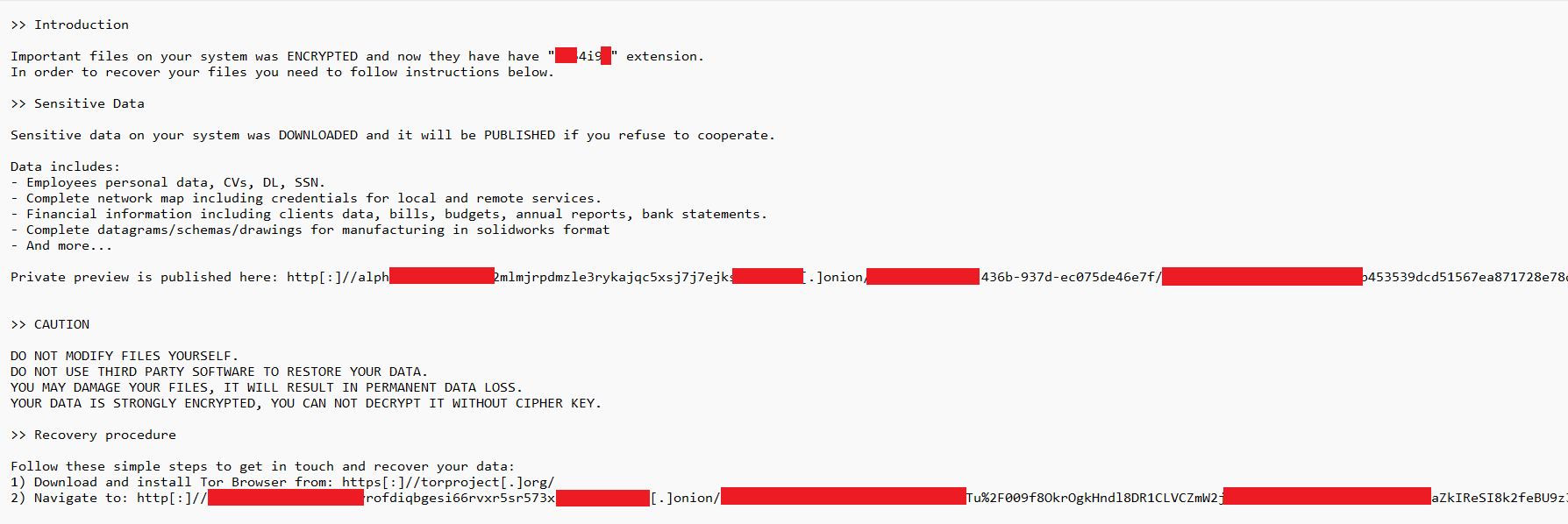
Encrypted file format
Files infected by BlackCat contain the following format
- Bytes encrypted with chacha20
- 4 bytes signature 19 47 bc c3
- 256-byte blocks
- 4 bytes length of the previous block
- 4 bytes signature 19 47 bc c3
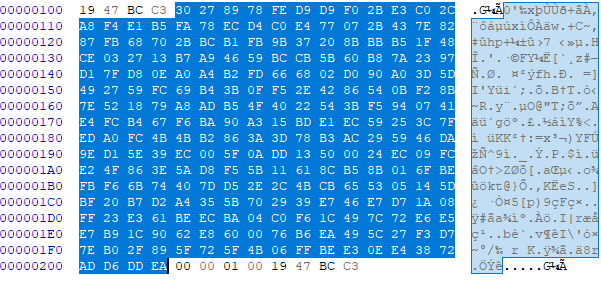
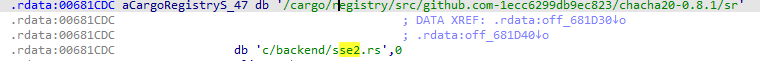
The ransomware has been determined to make use of a cipher stream that corresponds to the chacha20 algorithm and it is implemented with RUST’s native library. Within the binary it is possible to find the versions of the libraries used:
Ransom logistics
From the ransom note two sites are obtained. The first corresponds to the official website of ALPHV, where we can find a dashboard of all the attacks carried out by this criminal group that are currently active and that have not been paid yet:
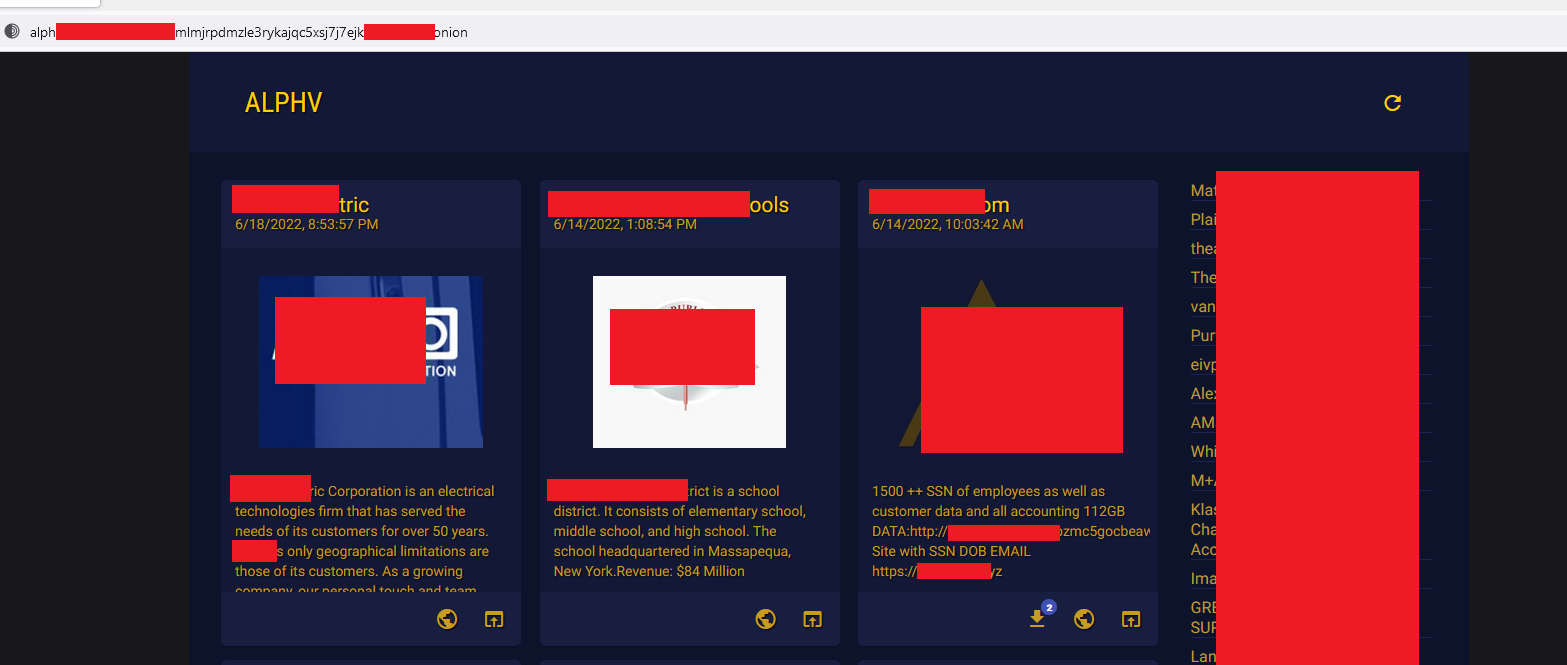
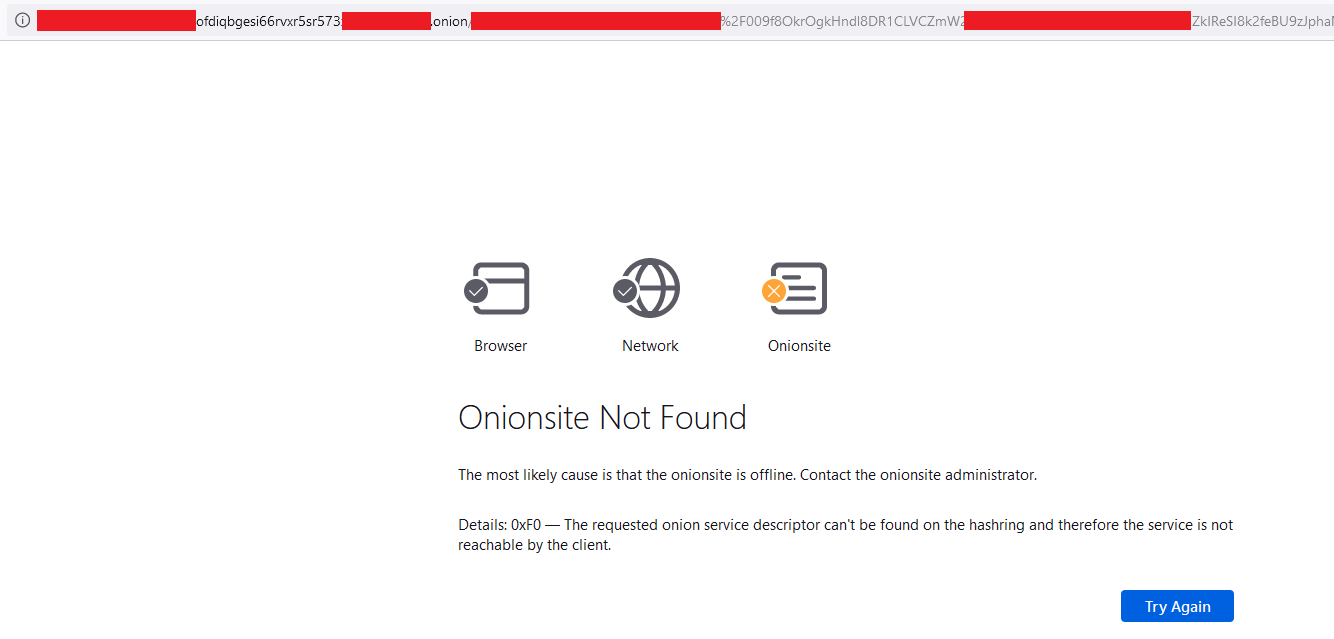
The second corresponds to the page where the payment for the ransom of the information can be made. At the time of this writing, the rescue site is not available:
Privilege Escalation
UAC technique is done using a COM interface in conjunction with the Elevation Moniker within the ransomware file.
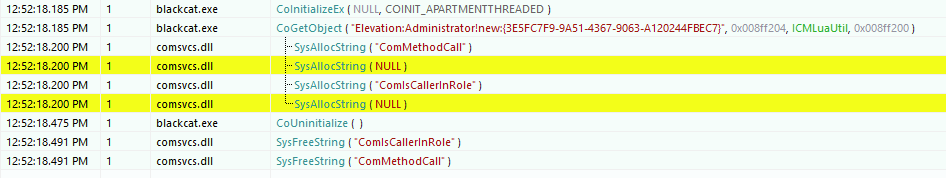
This technique works using a COM interface that is listed in the log shown in the following image:
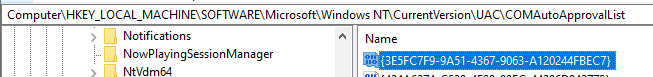
The COM interfaces listed in the registry share the feature that they can be elevated automatically (without the use of the UAC prompt) according to Microsoft specifications.
The COM interface in question has a method that implements a call to ShellExec, which can create a new process with the provided arguments. In this case, a new instance of BlackCat is created, but it now contains the access token with elevated privileges.
At the end of the execution of the parent process, it proceeds to create a new one with administrator privileges, to be able to encrypt the files without restriction:
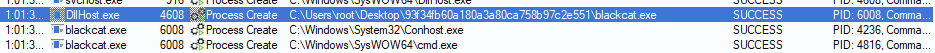
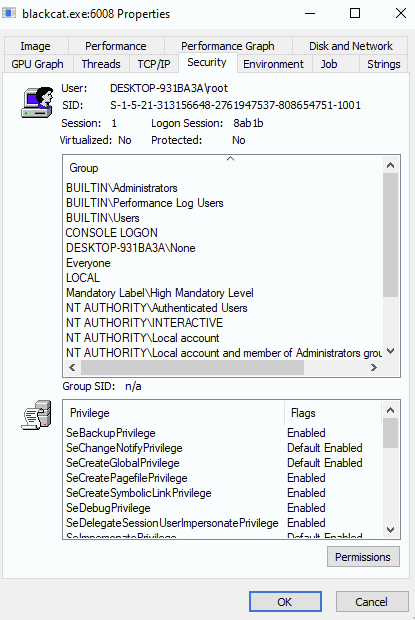
We proceed to perform an inspection in the process with PID 6008, where it has the administrator privilege. In this part, the SeDebugPrivilege permission stands out, which is a privilege that allows the user to debug processes belonging to other users, even with SYSTEM privileges, which allows (among other malicious actions) to be injected into different processes.
System Configuration
The ransomware is responsible for making modifications to the configuration of the system being attacked.
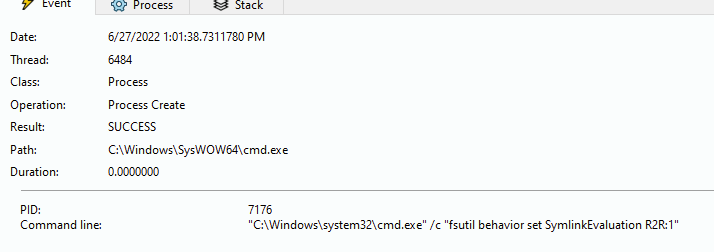
It starts using the command “fsutil behavior set SymlinkEvaluation R2R:1”, this command causes an alteration in the resolution of symbolic links of the system. The impact that causes this modification is the enablement of the resolution of links to remote files, to increase the scope of files to be encrypted.
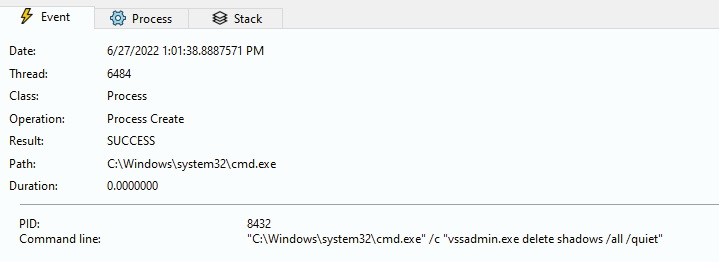
The removal of the shadow volumes from the system continues, this is done by executing the “vssadmin” command, which means that the system data will not be backed up.
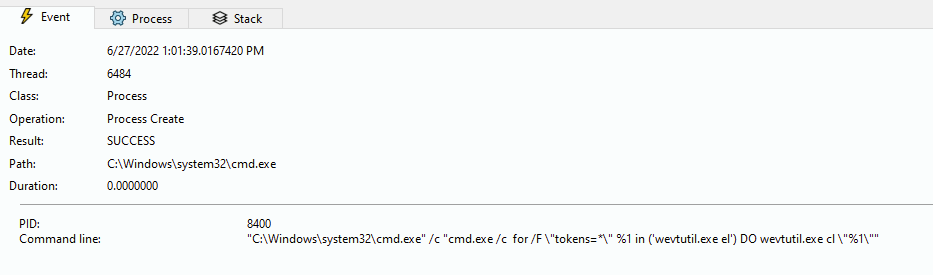
Finally, it proceeds to delete the system events to avoid leaving traces by using a wevtutil.exe command:
Propagation on the network
It has been determined that the malware makes queries through NetBIOS within the network, to identify other possible computers to attack. It does this by querying with the NBSTAT command:
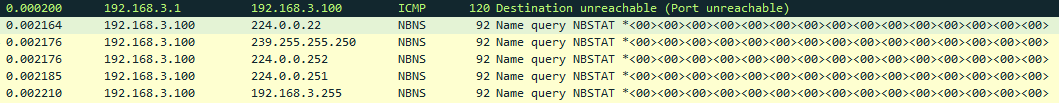
If you find other hosts within the network, try propagating using the SMB protocol using the credentials of the current user.

IOCs
TTP’s
- File encryption
- UAC Bypass
- Network enumeration by NetBIOS
- Network propagation over SMB
- Removing shadow copies
- Deleting records
- Changing the wallpaper
MITRE ATT&CK
- T1486 – Data Encrypted for Impact
- T1562 – Impair Defenses
- T1070 – Indicator Removal on Host
- T1078 – Valid Accounts
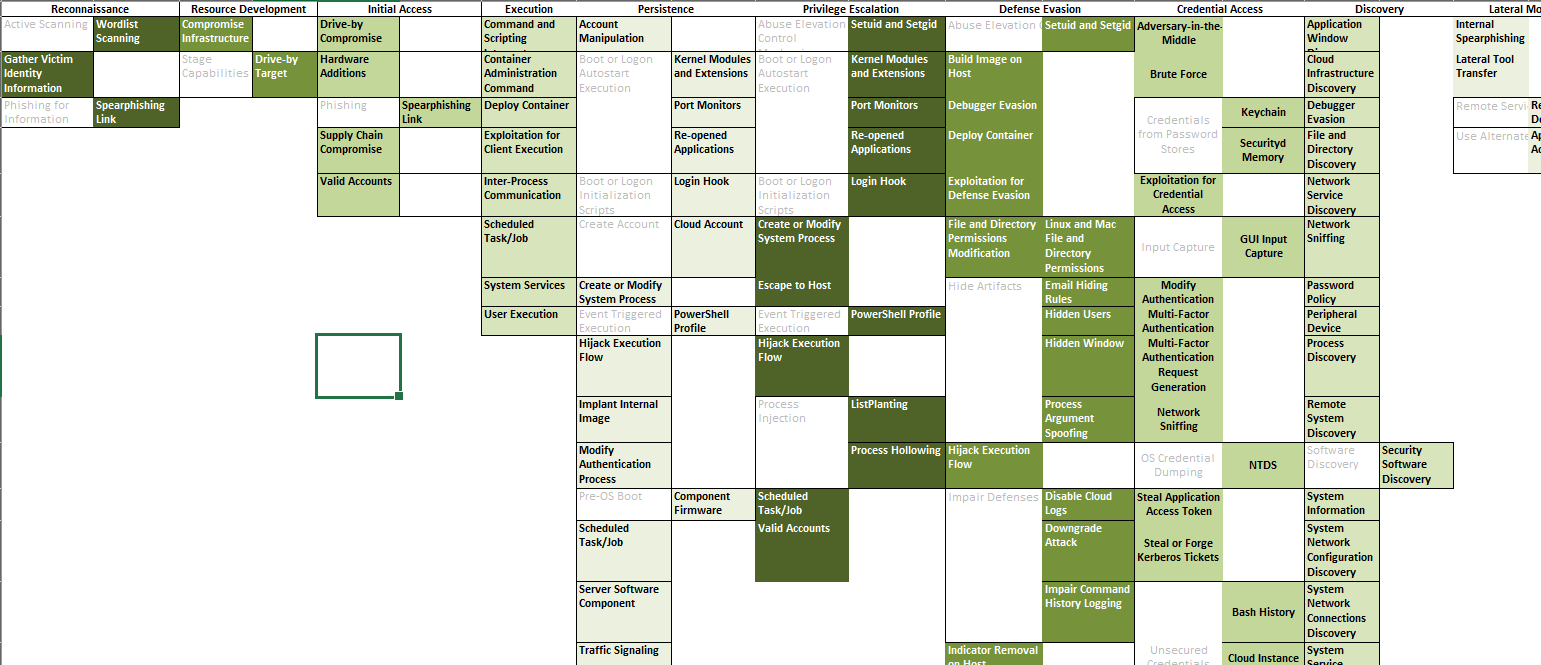
MITRE ATT&CK of Blackcat TTPs:
Arsenal
- Mimikatz
- Crackmapexec
- Psexec
- Cobalt Strike
Conclusions
The ALPHV-BLACKCAT Ransomware group is not new in the cyberspace. They have invested time and capital to position themselves as one of the main threat actors in 2022, having specialists from BlackMatter, who previously was DarkSide. We must pay special attention to their goals, as well as their recruitment processes for associates and possible insider threats. It is also important to take into account the techniques and indicators in this report for a proactive protection, and very importantly, to have a daily feed of new indicators and actors in the region.
At Metabase Q, through our Ocelot Threat Intelligence Service, we monitor this type of groups in LATAM to offer indicators of attack (IoA) and compromise (IoC) to our clients that allow them to take preventive actions. Furthermore, we offer context of these adversaries to understand their motivations, strategies and techniques that eventually, together with our Takedown Service and support of the local police, remove them from cyberspace.
Finally, with our APT Simulation Service, we create this type of ransomware in our laboratory and replicate it in our customers’ network, to strengthen monitoring, detection and response controls in processes, people, and technology.



